Thursday, July 10, 2014
Author: Chaotic Indian
A major vulnerability believed to be present in most versions of the Android Mobile OS can allow malicious Android applications to make phone calls on a user’s device, even if they lack the necessary permissions.
The critical vulnerability was identified and reported to Google Inc. late last year, by researchers from German Security firm Curesec. The researchers believe that the virus was first noticed in Android version 4.1, A.K.A “JellyBean.”
APPS CAN MAKE CALLS FROM YOUR PHONE.
“This bug can be abused by a malicious application. As an example, take a simple game which has this code in it. The game won’t ask you for extra permissions to perform a phone call to a tool number but it is able to do it,” said Curesec’s CEO Marco Lux and researcher Pedro Umbelino on a blog post last Friday. “This is normally not possible without giving the app that special permission.”
By leveraging these vulnerabilities, malicious applications could initiate unauthorized phone calls, disrupt ongoing phone calls, dialing out to expensive toll services and potentially framing up big charges on an unsuspecting user’s phone bills.
ANDROID BUG ALLOWS UNAUTHORIZED USERS TO TERMINATE OUTGOING CALLS AND SEND USSD.
This vulnerability can also be exploited to disconnect outgoing calls and to execute
●Unstructured Supplementary Service Data (USSD)
●Supplementary Service (SS)
●Manufacturerdefined MMI (ManMachine Interface) code.
These special codes can be used to access various device functions or operator services, which makes the problem a nasty one for those who value data privacy and confidentiality.
“The list of USSD/SS/MMI codes is long and there are several quite powerful ones, like codes that change the flow of phone calls(call forwarding), blocking a SIM card, enabling/disabling caller anonymity and so on,” reads the blog post.
Even the Android security screening apps, which do not allow apps without the CALL_PHONEpermission to be executed, can be easily bypassed and offer no protection from these flaws, because the exploits have the capability to deceive the Android permissions system all together.
“As the app does not have the permission but is abusing a bug, such security apps cannot protect you from the exploit without the knowledge of this bug’s existence,”wrote the researchers.
A large number of Android OS versions are affected by the vulnerabilities. Researchers have found two different flaws that can be exploited to achieve the same goals one found in newer systems, and the other meant for older systems.
FIRST BUG MEANT FOR NEWER VERSIONS OF ANDROID
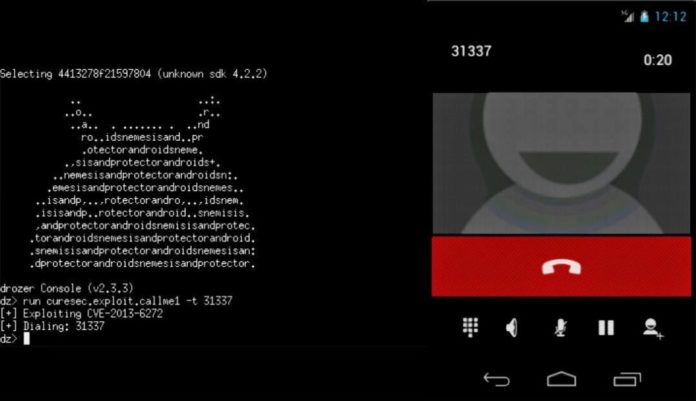
The first bug, known as CVE20136272, seems to have been introduced in Android version 4.1.1 Jelly Bean and continues all the way to the most recent 4.4.2 KitKat, before the security team at Google Inc. was able to fix it in Android update 4.4.4.
Unfortunately, only 14% of users have had the chance to download the update. Think about it how many other users are currently in the grip of the flaws? A very generous number, be assured.
SECOND BUG MEANT FOR OLDER VERSIONS OF ANDROID
The second bug is far wider in it’s reach, affecting both versions 2.3.3 and 2.3.6, the most popular versions of Android Gingerbread used by small phones and budgetminded phones which are immensely popular in emerging markets like those found in Brazil, China and Russia. The bug was fixed in 3.0.0 Honeycomb, but that was only a tablet release that no longer even charts on Google’s Android statistics. That means the bug is still open to 90% of the world’s Android users to the exploit.
Researchers at Curesec have provided source code and a proofofconcept demonstration app that lets users test their Android devices for vulnerabilities. In the meantime, it is strongly advised to Android users running 4.4.2 KitKat to update their device as soon as possible to prevent becoming a victim of this highly dangerous exploit. The update is expected to roll out in the coming weeks.
Links:
Anonymous – How to protect your devices from hackers and in general






Ooooh. I was considering on buying an android phone.
I am glad my android broke!
qui peux m’aider ici???
il vous suffit de restaurer votre téléphone si ce bug se produit pour vous
Why dont you? As i read it the new phones are running 4.4.2 or higher and if not will update as soon as you connect to the web. I would take an android phone over iphone any day.
I agree. I bought an Android phone 2 months ago. I immediately rooted it then upgraded from 4.1.2 to 4.4.4 Kit Kat. No need to worry about the bug unless I go back to stock 4.1.2! =8-D
I wouldn’t worry too much about it, as long as you stay on the official market then you should be fine. Any apps that look suspicious normally get reported pretty quick. and these malware apps are normally modded paid apps from official ones and uploaded to website.
You’re right
Dear anons, I am putting my Email address please contact me, so that I can know whats going with our anonymous family around the world thank you.
[email protected]
Ooooh. I was considering on buying an android phone. thanks
Anyways,Android is atleast better than IOS
What u think about that made android for developers and IOS for people*
and whats whith the versions from cyanogenmod? do they have the same bugs? and also when i use “LBE privacy guard”?
as long as you don’t go downloading malicious software then you should be fine
i’m not sure for this. i think that factory or i don’t know should’ve security about hackers or any type of code malicious on their O.S.
I hope there is nothing of this sort in iOS.
There is, same idea on iphone but once you’ve opened any type of financial information your login and PW is shared with work be thief. Non of this matters though as long as you don’t bypass security features and install questionable applicatios.
Or you could root your android and use XPrivacy. Because even apps in the store have hidden permission they wont ask for,but still use. Don’t be naive and think malicous apps are restricted to the outside of google play or where ever you get them.
I am not suprised … Vulnerabilities everywhere 🙂 for example if you have cydia on IPhone , there is something I coded with Assembly and c#plus , when I connect my iphone to my Computer which is it must be Ubuntu , cuz it works only with Ubuntu console, when I start to using the program with cydia , Ubuntu Concole automatically gives me private exploits , which is actually the exploit is coding by Assembly program I made , and for example when we start to root:www.google.com , assembly and c plus start automatically coding exploit which useful for the webpage you enter…and exploit also ip spoofing which is you don’t need VPN 🙂
Is this only for android phones or can it be for tablets aswell?
Tablets as well… If it’s android too..
Would like to link up with others like me. Please. Assist.
i think you’re doing it wrong^
why ads? no unique contents but ads? headquarter, affiliated with that / fb page…
not sure about your opinions^
WOW, So glad i did not get an Android. A friend of mine uses he’s phone ALL THE TIME! He even told me at least 4 times people have called him back saying that he called them but when they answered, No one was there!
Android is best by far. If you install an app like Greenify it will prevent any app from using the internet or phone. Many apps have access to your email and text messages, also. Since I installed Greenify I am able to view which apps performed which functions. There are a number of apps that monitor all functions. Advantage, Android.
s more, Google Play has exceeded its twentieth million download.
The quality of the links The quantity of the links The velocity of link building.
It allows users to see all the daily changes in any security’s stock price without having to visit financial sites.
All cellphones and software not coded by you…are at risk….so make urs or just playout kool.
you can get Launchers off the playstore for IOS Launcher and its fundamentally the same thing. like android can do so much more. but then again maybe it for the poeple that dont want to just call, text, or go on facebook. also the Blackphone and Nexus , and even the old original moto google Atrix phonez, that first wer coming out are so much better lul. Globus VPN i recomend for anybody usin Android as well as Maxthon browser is a kool alternative
Yes, 100% right