
Although we haven’t even reached the middle of the year, we have created a list of phishing scams. We have created this list because we want our readers to be aware. For those of you who do not know what a phishing scam is, they are tricks and coarse social engineering resources fashioned to stimulate tension in its readers.
Such scams aim to trick its readers into answering or clicking the present link(s) (in the email or a website, or any other form of interaction) instantly, as that form of communication says they will lose something valuable to them, -for instance, the user’s banking email address was hacked and the scam warns the user that they must click this link to reset the password and protect their bank account. Such claims are always an indication of a phishing scam, because financial institutions or trusted businesses and companies will not take these kinds of approaches, especially through online messaging.
Locky

Just two days after Valentine’s day, researchers discovered that a couple of email messages were delivered using Microsoft Word files that contain macro scripts designed to install Trojans. This MS Word malware cloaking strategy has been utilized by a number of hackers who use the Dridex Trojan.
However, this encoding ransom-ware was not like its older cousin, it was new and was calling itself Locky. One crucial distinction was that it was created from the exceptional application of Visual Basic coding. Furthermore, Locky employed a PowerShell code to grab and run the viruses.
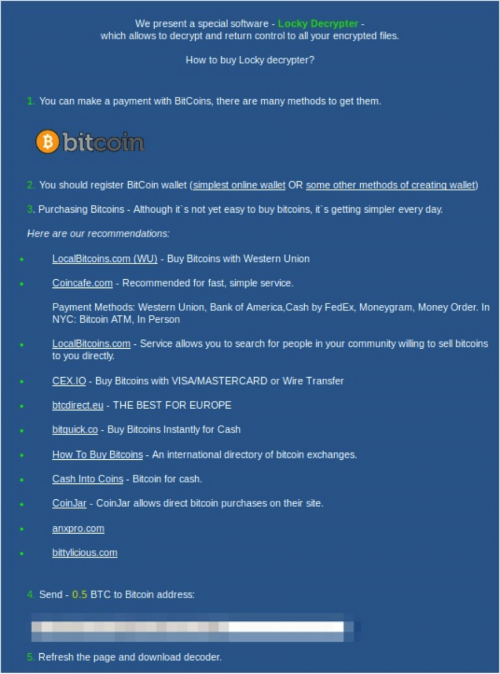
Palo Alto Networks, a security company based in Santa Clara, California, estimated that at least 375,000 computers worldwide had been disturbed by Locky within just a few hours. Even though Locky and Dridex Trojans are different, the resemblance of the emails and the Office macro files that were designed to supply Locky and Dridex is dazzling. Also, the downloadable URLs in the codes were designed in a manner that bears a resemblance to the naming convention designed to send Dridex.
For more information, find the detailed article at Palo Alto Networks
Cluster And The Internal Revenue Service
If you are interested in information and security, your eyes must have crossed the Internal Revenue Service (IRS) phishing case. And to make it sound even worse, the IRS recorded twenty (and more) different websites that created their personalized IRS phishing scams.
The Internal Revenue Service has a very effective security unit located in the United States Treasury Inspector General for Tax Administration, more commonly known as TIGTA. TIGTA is in control of battling phishing scams and searching for the scammers who victimize United States citizens.
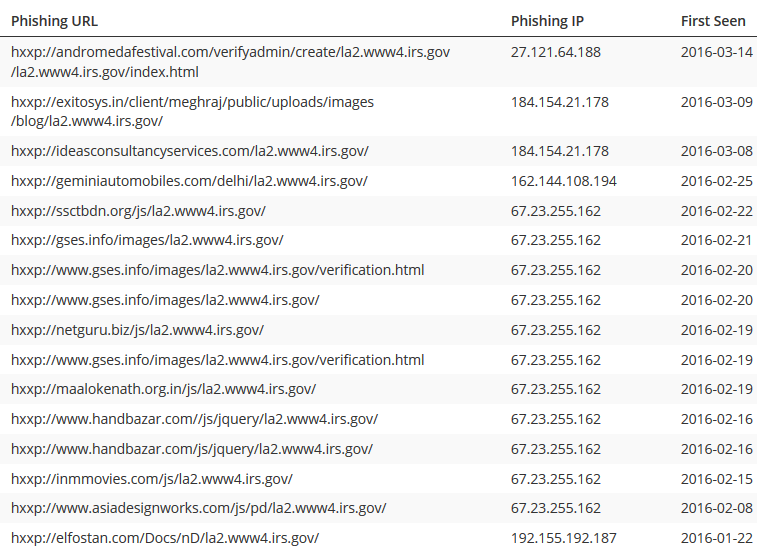
The ‘Cluster’ was the phishing layout that was most used when scammers wanted to lure individuals into logging in to a page where they could enter all their information. It was noticed that every login page in the series of different attacks had the same HTML title – Login – and the attacker commonly used a subdirectory route Ia2.www4.irs.gov. Throughout the second month of this year, most of the activities were managed on 67.23.255.162.
If you or someone you know has been targeted by this scam, then please report the Internal Revenue Service to [email protected].
For more information, find the detailed article at Phish Me
The Chief Executive Officer Scam

Another type of global phishing approach that may be taking place with frightening consistency, is the ‘Chief Executive Officers’ scam. The Federal Bureau of Investigation reports that since 2014, companies have shed more than a billion dollars internationally to the CEO scam. In one event in Paris, Etna Industrie endured from the scam when it shed thousands and thousands of dollars.

The BBC states that the head of the accounts department for Etna Industrie, was contacted by a hacker who had studied the company. The hacker mentioned that they would get an e-mail from Carole Gratzmiller (the Chief Executive of Etna Industrie) containing instructions for a private wire transfer. The accountant then received an email that had an address with the CEO’s name in it. The email also had an address that mentioned that the company was expanding, and was buying a property in Cyprus. The email further stated that the accountant would get a phone call from the estate agent and a lawyer, who would provide instructions on where to wire the funds.
These events took place within a short period of time, so the head of accounts was placed under pressure to respond instantly. During the opening office hours, the accountant received more than seven emails and a few phone calls. Before the lunch break of that same day, the transaction was authorized and more than $500,000 was sent to international banking accounts. Luckily for Etna Industrie, the banks stopped a few transfers just in time.
For more information, find the detailed article at The BBC
Scamming At Seagate

A criminal group of phishing frauds recently tricked a worker at Seagate Technology into disclosing W-2 tax paperwork on all existing and previous staff members. Such phishing scams are serious, due to the fact that the W-2 forms consist of workers’ personal and monetary information such as birth dates, home addresses, phone numbers, social security numbers, salaries, etc. Scammers value such information, because all this information can help scammers when filing fake tax return applications with the Internal Revenue Service.
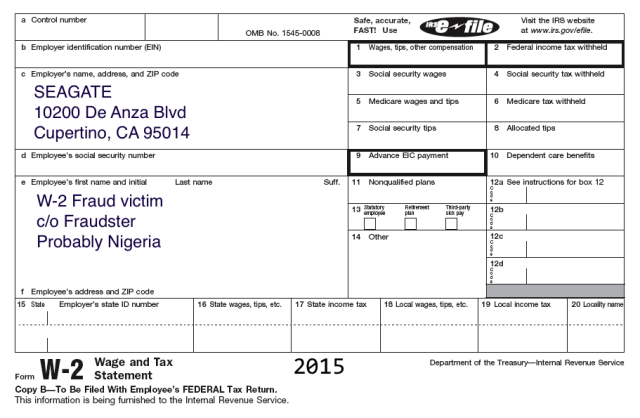
Seagate Technology PLC states that they were compromised on the first of the last month. The scam centred on last year’s tax details for existing and previous employees working in the United States. A large number of workers were disturbed.
For more information, find the detailed article at ARS Technica
The Snapchat Sorry Scam

Snapchat, the picture storytelling software, stated that one of its staff members was a target of a phishing attack that disclosed some paysheet details about their workforce. The Guardian reported that Snapchat stated that its computers had not been hacked, and no employee or customer data was leaked.
However, on the 26th of February, Snapchat’s accounts division was targeted by the remote message phishing trick, wherein the hacker assumed the identity of Evan Spiegel, the chief executive officer of Snapchat, and requested employee salary details. A few hours after the event, Snapchat verified that the email was not from Evan Spiegel. The incident was reported to the FBI. As a result, Snapchat offered identity theft insurance to its workers.
For more information, find the detailed article at The Guardian
The Hospital in Philadelphia Under Attack
Reports of a phishing attack at Main Line Health hospital in the Philadelphia region, busted out in the beginning of March. A spear phishing email had been mailed to a Main Line Health staff member in the third week of February. The staff member, who had assumed it was a genuine email, fulfilled the email’s demands by providing sensitive information on all Main Line Health workers.
Furthermore, the authorities identified that the message was a part of a worldwide phishing strategy that used fake emails to acquire private information. Authorities mention that no client or patient details were circulated or jeopardized throughout the assault.
For more information, find the detailed article at NBC Philadelphia
City of Hope Cancer Hospital Gets Scammed

City of Hope, a cancer treatment hospital and research center, was mauled throughout the third week of January. The event contributed to the illegal accessibility to the emails of more than two employees, based upon a press release distributed by the center. After a brief examination, it was established that many of the compromised emails contained confidential health records such as patient names, healthcare report numbers, date of birth, addresses, email addresses, phone numbers, and some medical details.
Luckily, the information held inside the compromised email accounts contained nothing more than the names of patients and their healthcare report numbers. After the analysis, it was discovered that the hackers did not intend to sell this information, instead, they planned to send more scam emails to the email addresses obtained from the medical records.
For more information, find the detailed article at My News LA
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (The Cleverly Devised Scams That You Need To Know) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.




