
There is a new ransomware in which is slithering across the Internet that has been brought to my attention.
This new ransomware is named Mamba.
The confusion about Mamba is that is has not emerged to perform attacks. This virus is not even written properly, nor is it reliable.
However, if you do fall victim to Mamba, more than likely, recovering anything from your computer will be unlikely.
Previously, ransomware known as Petya, will scramble the Master Index of your main hard drive, often referred to as the Master File Table (aka MFT). However, instead of targeting individual files, ultimately leaving your computer unbootable, a window emerges, resembling something of a 1990’s style boot screen, informing you on how to purchase your way out of trouble.
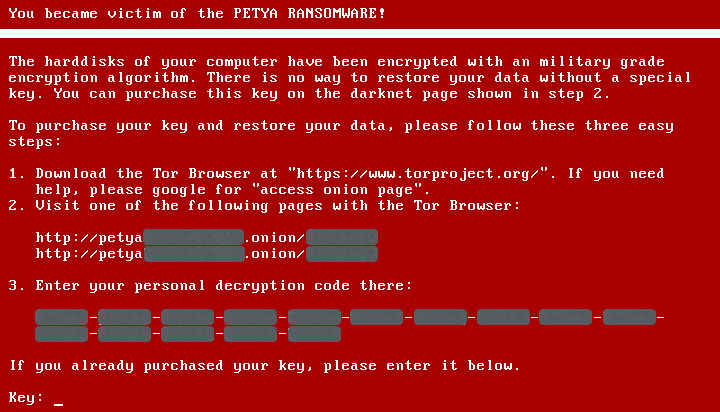
Luckily, Petya left the main bulk of your raw data completely unscrambled at the main sector level, albeit, tantalizingly out of reach.
However, Mamba takes a whole new approach on ransoming your entire disk. Mamba will scramble your desk sectors, including the MFT, your main operating system, any applications you have installed on your computer, and any and all shared files making up your personal information, as well.
Confusingly enough, Mamba performs this work with only a tiny bit of programming effort. The malware simply installs on the target computer and activates a pirated version of the software DiskCryptor.
DiskCryptor is also known as the FDE (Full Disk Encryption) tool. Much like the Windows BitLocker, or the Apple’s FileVault, this asks for a specific password during the boot up phase. It will decrypt each and every sector – as it is readable – and encrypts ever sector as it starts to be written out.
Since we have not seen a Mamba sample in any of our email traps at this time, we are unable to provide specifics. However, it is safe to assume that the hackers behind this ransomware use an email to carry out their threatening ransomware.
A security researcher from Brazil, Renato Marinho, had recently written an article about a real-world Mamba infection at a multinational company. However, even in that type of case, he was unable to figure out exactly how the malware was able to get inside, in the first place. Nevertheless, it can’t be stressed enough about the caution you should exercise when sorting your email and opening up email messages.
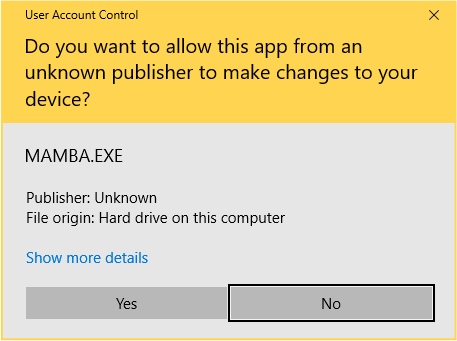
And if, accidently,the Mamba malware is downloaded, you will be prompted with an “elevation” prompt, first asking if you would like to give permission to this unknown application,to perform its respective tasks.
Within a few short minutes, your computer will then spontaneously reboot itself without any questions or knowledge. This then becomes your second and biggest red flag.
Before your computer reboots itself, the Mamba malware will have installed itself as a dummy version of the Windows Service, in which is named DefragmentationService, and then gives itself the LocalSystem privileges.
While the malware is running as a LocalSystem services, it activates itself – even if a user is not logged onto the machine. This is then invisible from the natural Windows desktop environment, ultimately giving complete control over the entire computer.
Once the machine reboots, the Mamba malware will then have the credentials required to install a low-level FDE software (DiskCryptor). This installation runs quietly in the background, after the computer reboots itself, or as instructed by the malware.
Mamba carries within itself, a copy of DiskCryptor. You can find this software in the C:\DC22 file. You can find this after the reboot by typing in ‘dir’.
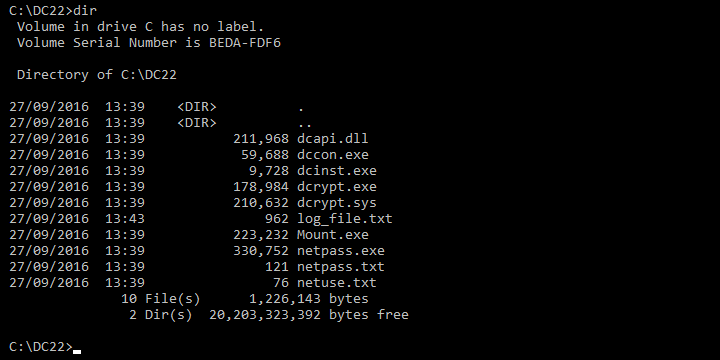
You can utilize the DiskCryptor held within the malware to see background. If you were to start the DiskCryptor, you will see the following image:
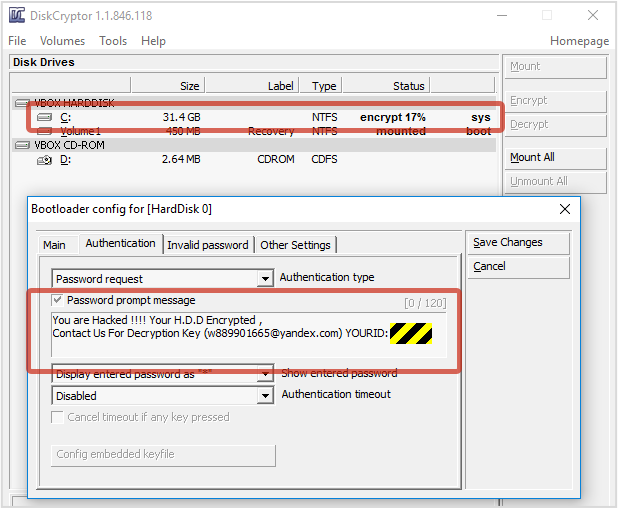
The encryption process is progressing along at a steady pace, taking several minutes to a couple of hours to complete, depending on the size of your hard drive and disk speed.
The creators of the malware have also developed this program to preconfigure their version of the development process of DiskCryptor, providing you with an option to ‘Pay Out’ instructions. Typically, you are asked for a password.
As soon as the encryption service has completed, you are in a tricky position. If your computer does not reboot automatically, your files are still in place. The DiskCryptor log – that contains all of the files – is nested inside the log_file.txt. This provides you with the plain text version of the password.
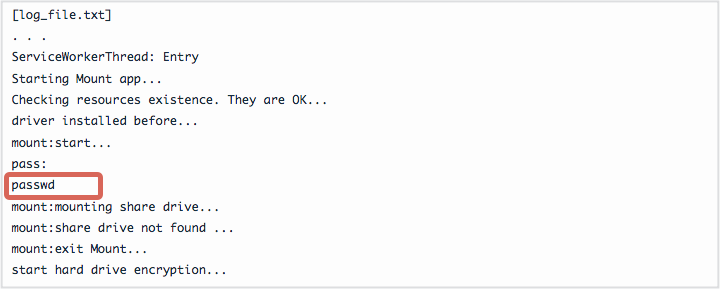
Now typically speaking here, we would be deeply critical of programs that dump our personal, private, or secured data into a plaintext document. However, in the case of Mamba, this becomes our lifeline. Rather, we can use the password from the log_file.txt and utilize the Decrypt option within the DCRYPT utility, reversing the encryption process.
If you are unaware of the process that is going on in the background – where the encryption is taking place, the story is entirely different. If you attempt to reboot your computer without decrypting the hard drive, you have just lost everything.
Unfortunately, DiskCryptor has made no new developments in the last two years. It is also incompatible with the new Windows installations that configure your hard drive. DiskCryptor uses a low-level bootup code in which you are then asked to enter your password. This is to encrypt your partitions then can be unscrambled in real time, thus allowing your computer to start up. (This is not compatible with the GPT disk settings.)
Regardless, Mamba will install the DiskCryptor, anyway.
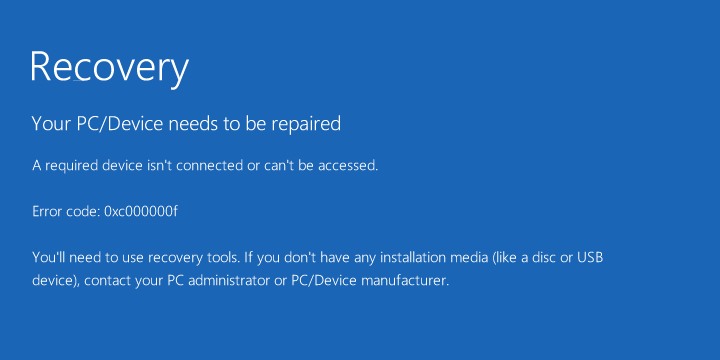
For those running a current version of Mac, you will most likely have a GPT-format disk. Those on Windows, once you reboot your computer, you are now seeing a bluescreen. No, not the ‘Bluescreen of Death’, but the bluescreen informing you that your PC needs repairing.
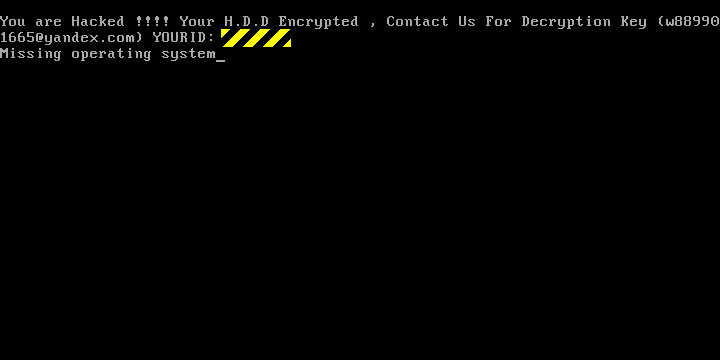
For those running an older module computer, the news isn’t much better. During the test of an older desktop, you are not able to go any further than the horrible “Missing Operating System” screen typically found on the MBR-Format disk.
What can you do?
I never encourage paying any amount of financial aspect to those ransomware demands.
In this case, I believe it wise to write off any data in which you have and just reinstall your operating system. I also highly recommend using a real time anti-virus software program. It would also do some good to look into an online cloud-based service to back up any important documents.
Sources: Secure List (Petya), DiskCryptor, Naked Security (Mamba Malware).
This article (Mamba Ransomware Attacks Your Entire HDD, Not Just Files) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.





Or just use a mac
lol…ever heard of linux?
Could someone list a few Anti virus programs that actually work against this?
thanks in advance
Can’t believe that someone would ask such a dick question…!!! How about searching on the internet!
Malwarebytes works best.
Never ever use a computer that has not 100% of the disks encrypted… and allways, allways boot that PC from a USB stick that you have under 100% control.
It is the only way to avoid “evil maid” attacks.
And do not forget to make BackUPs prior to reboot / shutdown on external media.
Things can go really bad.
I learn them the really hard way.
Now i allways use a power plugs that can be unplugged from wall (or have interruptor), i will never ever again let the PC powered off and connected to wall power.
One time ago… a little story… i had a PC powered off, but connected to wall power, i go away to buy some food, cinema, whatever you want to think on… then electricity power on the zone was cutted and restored after some minutes… when i came back home my PC was ruined (the chasis had explode), mainboard with black zones, processor broken, HDD open, etc… and some other things on the house also ruined (TV, Microwave, etc)… the case was that there where an idot that instead of pluging a 220V to zone calbes plug a 10000V (High voltage), not only my house was affected, all the neighbors also, etc… now i disconnect from wall anything i am not using (swicth or un plug power cables, etc). Yes all info on the HDD lost… thanks i had BackUPs on secure places on the house i could restore data… but not the one i was using prior to go out… now i allways do a full BackUP prior to reboot / shutdown.
No need for a Trojan, Malware, Virus… just a power failure on the zone can ruin your data, learned the rad way… also some cables on the house went out from walls.