
According to the website Net Market Share, Microsoft’s Windows is one of the more popular operating systems amongst users. From Windows holding the market users at 91.57% (operating systems from Windows 98 all the way up to Windows 10, in which Windows 7 holds the highest shares at 49.42%) brings forth major security concerns.
The tech giant, during the start of this month, updated a zero-day vulnerability that it found recently – the problem was the spreading of the Dridex Trojan.
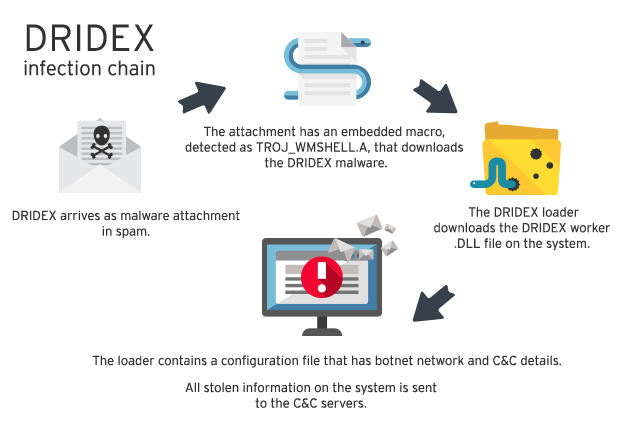
Dridex the banking Trojan was spreading quickly via a mass spamming campaign, where the hackers were emailing users with a contained Microsoft Word document. The document hid a malicious attachment, allowing the hackers to hop over many mitigating circumstances.
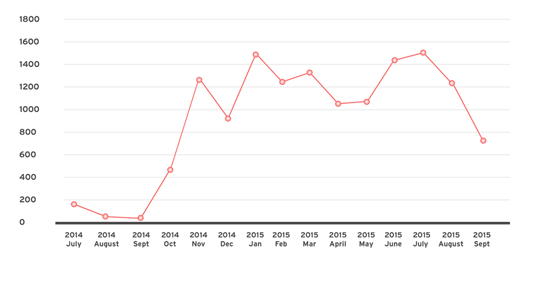
According to Proof Point, a cyber security company that wrote a complete analysis of the Dridex Banking Trojan, this was their first time observing the Microsoft vulnerability. They further added that the hackers have improved the new Dridex Banking Trojan.
The experts from Proof Point further explained that once the user opened the attachment in the Microsoft Document it would – if successfully installed on the target system – start initiating a series of actions to install the Dridex botnet ID, which is 7500 on the target operating system.
The exploit is directly proportional to the way Microsoft works with the OLE2Link systems.
According to Carnegie Mellon University’s Vulnerability Notes Database website, the OLE2Link system will allow an attacker to execute the application based on the server that consists of the Multipurpose Internet Mail Extensions (MIME) and allow the hacker to remotely attack and install code on the vulnerable system.

The security and anti-virus firm McAfee initially only reported the vulnerability last week.
In a test conducted by Proof Point, the attacked system did not require authorization; it was simply affected by starting the Word 2010 file. However, once the document is clicked on, a dialogue box hovers up asking the users to update the document as it contained links that refer to other files.
At this point, the interaction with the box was not required because according to the experts, the Trojan was already installing itself on the host system and the ‘yes’ or ‘no’ option made no difference.
The Devil Is In the Details

FireEye Inc., which is a cyber security company that provides protection services against online threats and malware protection, states the process revolves around the Microsoft Office Rich Text File (RTF) document that consists of the OLE2Link object. So when the target opens the document, the file publishes an online request to download and install the malicious file, which is masked as a bogus RTF document.
The masked file then installs and fires up the dangerous program, where it also prolongs the loading process of the fake RTF file. However, the malicious program then downloads a decoy document for its hosts to view, thus making the user believe it is a real file.
Moreover, this problem is not limited to only Microsoft Office 2010 but also affects the latest edition of the Microsoft Office that utilises the Windows 10 operating system.
However, there is a solution to this entire problem that comes in the form of an updated patch. But before you go ahead and look for the fix – the company does ask its users to have the Service Pack 2 installed for Microsoft Office 2010.
Also as an extra precautionary practice, one must block the RTF documents in Microsoft’s office and use the Office Protected View, which can protect the user in many other ways.
This article Microsoft Office Used to Spread Dridex Banking Trojan) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.
Supporting Anonymous’ Independent & Investigative News is important to us. Please, follow us on Twitter: Follow @AnonymousNewsHQ




