
You need one hundred and four dollars, more or less, eight hours and Amazon’s cloud computing to hack the National Security Agency’s website. Oh, and you need to make use of the NSA’s very own FREAK vulnerability to hack them in their own game.
A group of researchers did just that, using a few tools to implement man-in-the-middle-attacks. This is an ability that swiftly creates an outcome of 512 bit RSA (RSA is one of the first practicable public key crypto systems and is widely used for secure data transmission) keys.
The bug was reported on Monday. It allows the attacker to take control of secure connections between people using iOS devices or Android devices. This gives hackers a chance to mimic the target and steal private information like login details and passwords.
To factor the 512 bit export keys, the project enlisted the help of Nadia Heninger at University of Pennsylvania, who has been working on “Factoring as a Service” for exactly this purpose. Her platform uses CADO NFS on a cluster of EC2 virtual servers, and (with Nadia doing quite a bit of handholding to deal with crashes) was able to factor a bunch of 512 bit keys; each in about 7.5 hours, for $104 in EC2 time according to Vice.
Image Source: Google Image – A XKCD cartoon illustration
Let us explain the FREAK vulnerability to you in a more detailed manner:
Earlier this year, many cyber security companies revealed information about a vulnerability in OpenSSL. OpenSSL started accepting temporary RSA keys when using non-export cipher suites. A malicious server could make a TLS/SSL client using OpenSSL, using a weaker key exchange method.
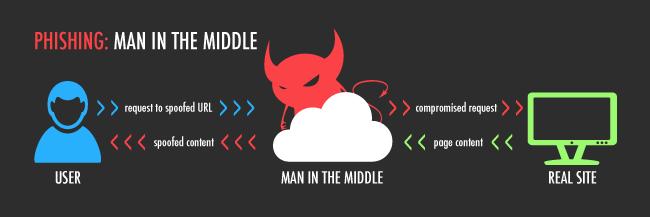
As stated earlier, OpenSSL clients accepted EXPORT-grade insecure keys even when the client had not initially asked for them. This could be exploited using a man-in-the-middle attack, which would intercept the client’s initial request for a standard key and ask the server for an EXPORT-grade key. The client would then accept the weak key, allowing the attacker to factor it and decrypt communication between the client and the server.
The vulnerability affects all Linux systems too, including the Server, Workstation, Desktop, and HPC Node variants that have not installed the fixed version of OpenSSL packages.
While the use of EXPORT-grade ciphers is disabled by default in OpenSSL), it can be enabled by applications that utilize the OpenSSL library. For this reason, the vulnerability is able to affect all Linux 6 and 7 systems, including the Server, Workstation, Desktop, and HPC Node variants, which have not installed the fixed version of OpenSSL packages.
However, using Internet-wide scanning, we can perform daily tests of all HTTPS servers at public IP addresses to determine whether they allow this weakened encryption. More than a third of all servers with browser-trusted certificates are at risk. i.e all the HTTPS servers at Alexa’s top 1 million domain names have their current vulnerability levels at 8.5 percent. HTTPS servers with browser trusted certificates are at 6.8 percent vulnerability, and the rest of the HTTPS servers are at 11.8 percent.
Browsers are vulnerable to the FREAK attack because of bugs that allow an attacker to force them to use weak, export-grade encryption. One example is the OpenSSL bug described in CVE-2015-0204, but some other TLS libraries have similar problems. Far more browsers are vulnerable to the FREAK attack than was initially thought when the attack was announced, including:
Patch available now
| Browser | Link & Status | |||||||||||||
| Internet Explorer |
| |||||||||||||
| Chrome on Mac OS |
| |||||||||||||
| Chrome on Android |
| |||||||||||||
| Safari on Mac OS |
| |||||||||||||
| Safari on iOS |
| |||||||||||||
| Stock Android Browser |
| |||||||||||||
| lackberry Browser |
| |||||||||||||
| Opera on Mac OS |
| |||||||||||||
You can check whether your browser is vulnerable using our FREAK Client Test Tool.
Chrome for Windows and all modern versions of Firefox are known to be safe. However, even if your browser is safe, certain third party software, including some antivirus products and adware programs, can expose you to an attack by intercepting TLS connections from the browser. If you are using a safe browser but our client test says you’re vulnerable, this is a likely cause.
Image Source: Google Image – Man in the middle attack explained via diagram
In addition to browsers, many mobile apps, embedded systems, and other software products also use TLS. These are also potentially vulnerable if they rely on unpatched libraries or offer RSA_EXPORT cipher suites.
If you are running a server, then you should immediately disable support for TLS export cipher suites. While you’re at it, you should also disable other cipher suites that are known to be insecure and enable forward secrecy. For instructions on how to secure popular HTTPS server software, we recommend Mozilla’s security configuration guide and their SSL configuration generator. We also recommend testing your configuration with the Qualys SSL Labs SSL Server Test tool. If you are a systems admin or are a developer, then please make sure any TLS libraries you use are up to date. Unpatched OpenSSL, Microsoft Security Channel, and Apple Secure Transport all suffer from the vulnerability. Note that these libraries are used internally by many other programs, such as wget and curl. You also need to ensure that your software does not offer to export cipher suites, even as a last resort, since they can be exploited even if the TLS library is patched. We have provided tools for software developers that may be helpful for testing this.
Furthermore, if you are using Microsoft Vista or newer versions of Windows, you can take the following steps as the system administrator to protect yourself. However, not all versions of Vista, Windows 7, and Windows 8.x include the critical gpedit.msc program. Vista Home Premium; Windows 7 Home Premium, Home Basic and Starter, and Windows 8.x Home Premium do not include it. There are ways to add gpedit to these systems.
Go to computer configuration> Administrative Templates> Network>SSL Configuration Settings. Under SSL Configuration Settings, click the SSL Cipher Suite Order setting. In the SSL Cipher Suite Order pane, scroll to the bottom of the pane. And simply enter the following cipher list.
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256,
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256,
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384,
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256,
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384,
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384,
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256,
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256,
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA,
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA
These will keep you protected and safe. We at Anonymous want our friends and readers to be up to date. As for normal users, we once again recommend that you use up-to-date Firefox and Chrome.
AnonHQ recommends: Protect your PC & mobile devices from hackers and governments & surf and download anonymously





http://www.itanimulli.gov
illuminati reverse
you’re doing good,where can i get the chrome on android patch file??
The latest versions of chrome and firefox are safe.
Hi
I do not use chrome new version using the old and do not use it much but if mozilla most current version
Anonymous will take over everything 😉
anonymous is not a group
Lol!!! I hate to break it to you, but there has been a major advancement in integer factorization. I factored ten 2048 bit semi-prime numbers in under thirty on a regular laptop! Is it a 1 or a 0 or not? Plus, the NSA isn’t dumb enough to use 512 bit encryption. I’ll break 512 bit RSA for ten bucks a pop. AES is weak, too. I have a better encryption method…
Actually you would be surprised on how stupid the NSA actually is, they have been cought trying to take over several different sites owned by hackers, and several different forum accounts and how many millions of other websites that are now owned by the NSA and USA governemnt. The government hasn’t updated thier encriptions since like the 1990s so it is very well possable that they are still using 512 bit encription.
How exactly is this going to stop the “Black Hats” from getting into the NSA? This blantently tells us that the NSA isnt as cracked up as they, say they are. unknown to what people think, NSA is just a simply group of hackers just like any given DOX or attack from our OPs, just the NSA is just paid by the US Governemnt, and not to mention whom are overpaied. They say that the newest virsions of Chrome and Firefox are safe, OR is it? we can never know unless we find out ourselves whether or not they are “safe” Nothing is safe anymore on the internet, no matter where you go (unless your using a VPN) you ip is logged then sold to the government, we can never know who is using our IPs or even our computers to launch attacks. This NSA hack is just the begining, for just posting this, people will try and try to attack the Servers of the NSA and constently get caught and Give us “White Hats” and “Grey Hats” a bad name because people are starting to get scared of being on the internet because the next war will be a Cyber War