
The title is correct, this is not a hoax, lure, etc. In fact, this is 2016 and you are now able to earn some serious money by simply contribution your attacks into a well-organized DDoS attack…scheme.
When discussing BitCoins, and BitCoin mining process, in order to properly mine for BitCoins you would need to not only build, but also maintains an extremely massive public ledger. Within this ledger, you would then be holding a large record of every single BitCoin transaction in the ledgers history.
With this, you would also need to know that while you are mining for BitCoins, you are also contributing onto a very large source of computational power. This amount of power is needed in order to properly keep the BitCoin network alive and running.
Whenever Person A sends Person B a BitCoin, these miners will then perform a validation in order to properly ensure that Person A has enough BitCoins in the ledger in order to pass along to Person B. This is also adding information onto the transaction section of the ledger. Once verified, then the miners finally seal the transaction behind layers upon layers of a vastly large computational network. This is setup in order to properly protect that ledger from becoming compromised…or Hacked!
So, in conclusion…You can reward your miners with Bitcoins by attempting to hack your way into these ledgers.
If you think about it, you are being awarded in order to contribute onto the, already massive, amount of computational power in which is the soul of the BitCoins transactions and makes sure that each miner is running properly and recording every transaction. In return, your award is a small piece of this digital cryptocurrency as a form of incentive.

However, of course all great things does have a “bad” section. BitCoin has been one of the most criticized for not properly operating such large amounts of computational power for more resourceful uses. In order to mine for BitCoins, you would need a lot of CPU cycles as well as power. However, just a few short years ago, some researchers have moved the BitCoin mining operations forward by creating a new line of cryptocurrency known as “PrimeCoin”.
When discussing PrimeCoin, the miners main computational power is not then just utilized for the upkeep of the different transactions, but it also utilized in order to find the long chain of the prime number. This plays a huge role inside of the encryption settings as well as the cryptography.
But this article takes a strange and mysterious twist to it. We see all the time about “Hackers are Bad”, “Hackers destroys everything” and so on. However, a pair of researchers had gathered up the muster and enrage their curiosity. These researchers has proposed the weirdest concept for the hacking community.
A malicious digital currency, in which the miners operating a full capacity can only mine if they are participating inside of a Distributed Denial of Service (DDoS Mining). These attacks would be targeting specifically preselected targeted websites in order to make those websites temporarily unavailable for viewing. This would be done by flooding the website(s) server(s) with several millions of simultaneous requests.
DDoSCoin, in which has been developed by Eric Wustrow and his partner in crime Benjamin Vandersloot in which comes from the University of Colorado Boulder, and the University of Michigan, is indeed a theoretical cryptocurrency in which rewards a designated miner in order to open up a large number of TLS Connections in order to target specific web servers.
This new malicious concept, or proof-of-work, (which has been dubbed as the “Proof-of-DDoS”) model is utilized by the DDoSCoin Minners functionality. However, the DDoSCoin Minners can only operate on TLS 1.2. But with so many of top million websites floating around on the internet that already utilizes TLS 1.2 version of this protocol, every miner participating in the DDoSCoin operations are entitled to a piece of the reward.
The two researchers posted an article on “USENIX.Org” pertaining to the concept and operations of how DDoSCoin miners will work. In which they state:
“In modern version of TLS, the server signs a client-provided parameter during the handshake, along with server-provided values used in the key exchange of the connections,” This paper is entitled DDoSCoin: Cryptocurrency with a Malicious Proof-ofWork. They continue saying “allowing the client to prove that it has participated in the DDoS attack against the target server.”
Using this new system, users are then awarded to those in which have proven they have participated in a DDoS Attack.
It gets better!
Users that utilize DDoSCoin in their blocks can also trade their digital money for other forms of digital currency, which can include Bitcoin and Ethereum.
Did you think that after reading all of that, we wouldn’t provide you the details on setting up your own DDoS Targets for DDoSCoin? Well, think again!
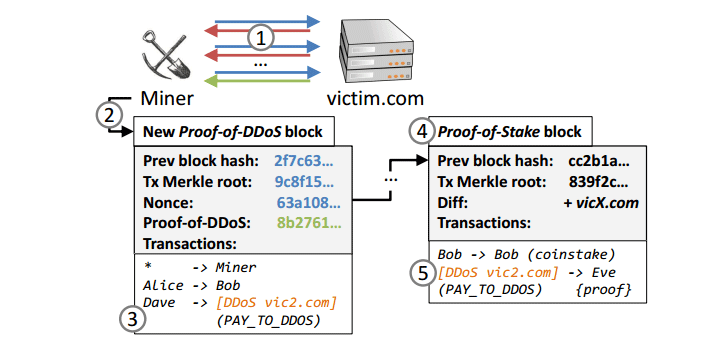
In order to setup a specific target for DDoS, you can utilize the PAY_TO_DDOS transaction. This transaction will include two arguments:
* Domain of the Victim Site
* The number of TLS connections in which will be needed in order to established the connection.
Each of these transactions are then recorded under the DDoSCoin blocks inside of a database (also known as “Blockchain”). Now the easy part. Your miners can now select just one of the blocks, launch their malicious attacks, and ultimately…receive your DDoSCoin as a reward.
However, what if everyone just DDoS’d everyone? The researchers has concluded that those participating in the DDoSCoin attack program would all have to agree on the specific target.
As of now, there are several people hiring hackers on the underground market to perform DDoS attacks in order to earn money.
This system is only on paper for now. This is just a theoretical concept that is still in early stages of development.
As this story progresses and further development is made, we will be covering this story.
Sources: The Hacker News | USENIX
This article (The Rising Cryptocurrency is Paying Hackers to Participate in DDoS Attacks) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.





What is DDoS?
you basically flood the server with requests until it crashes.
Seems legit xD