
Police in the United States are now using ‘Stingrays’ to track phones. The Stingray is an IMSI catcher (International Mobile Subscriber Identity) manufactured by the Harris Corporation. The way it works is that it gathers signals from nearby cell phones to pinpoint a suspect’s location. These cell phone tower simulators, or IMSI catchers, were designed so that neither the cell phone’s user nor carriers can detect their utilization.
In order to understand the Stingray better, we need to understand how a cell phone finds a signal tower. Put simply, cell phones typically look for the strongest, and therefore usually closest, tower that is broadcasting a cell signal to link into the network in order to send or receive phone calls, SMS, MMS, or internet data.
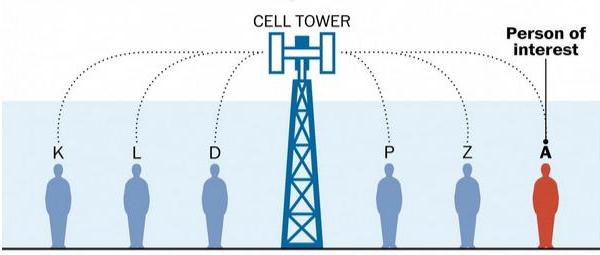 Image Source: Google Image – A picture showing how a cell phone tower works.
Image Source: Google Image – A picture showing how a cell phone tower works.
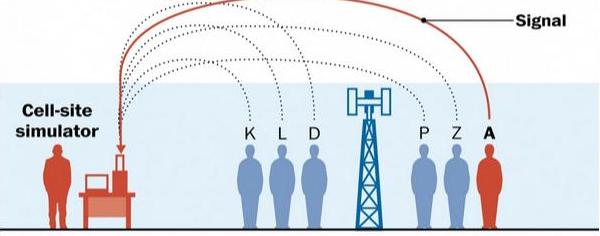
The Stingray device, once activated, mimics a cell tower, providing the best signal in the area which tricks cell phones to register with it. (NOTE: The phones are not required to be on a call or using internet or even sending or receiving any kind of messaging.) The cellular phone then transmits its phone number and unique electronic serial numbers (ESN, IMEI and IMSI) to the Stingray. This allows the phone to be tracked.
Using a Stingray, the police can do the following, and more:
- Extract saved data, such as International Mobile Subscriber Identity & Electronic Serial Number: This is accomplished by downloading the IMSI, ESN, or different characteristic information from every one of the devices connected to the Stingray. In doing this, the IMSI, ESN or equivalent identifier is not obtained from the cellular provider, but rather, the Stingray downloads this information directly from the device’s transmitted radio waves.
- Write cellular protocol metadata to internal storage
- Force a cell phone to increase its signal rate (which allows the police to hear your calls live): Cellular telephones, radio transmitters and receivers all have a very similar link, however, the cell phone solely communicates with a ‘repeater’ within a nearby cell tower installation. At that installation, the devices absorb all cell calls in its geographical region and repeat them through different cell tower installations onward to their destination mobile device (either by radio or land line wires). Radio is used, additionally, to transmit a caller’s voice/data back to the receiver’s cell device. The two way phone communication exists via these interconnections.
- Force extra radio signals to be transmitted
- Real time tracking and location of the device: A Stingray is used to track a phone or different, compatible cellular device even when the device isn’t engaged in an activity or accessing information services.
- Flood the cell phone with data, using a Denial of Service attack (DoS): The Federal Bureau of Investigation has claimed that when used to identify, locate, or track a cellular device, the Stingray doesn’t collect communication content or forward it to the service carrier. Instead, the device causes disruptions in communication. Beneath this state of affairs, any attempt by the cellular device user to make a call or access information services can fail while the Stingray is conducting its data mining.
- Extract the encryption key(s)
- Intercept communication content
- Conducting base station surveys (a process of using over the air signals to identify real cell sites and precisely map their coverage area): A method of summing up data on cell sites together with identification numbers, signal strength, and signal coverage areas. When conducting base station surveys, the ‘ray’ mimics a telephone while passively collecting incoming signals being transmitted by cell sites within the area of the Stingray.
- Radio jam
- Protocol rollback attacks
The use of this device has been funded by the Department of Homeland Security for the Los Angeles Police Department. The device was introduced in 2006 to battle ‘regional terrorism,’ but there is almost always an abuse of power; according to a report published by the Electronic Frontier Foundation, “the LAPD has been using it for just about any investigation imaginable.”
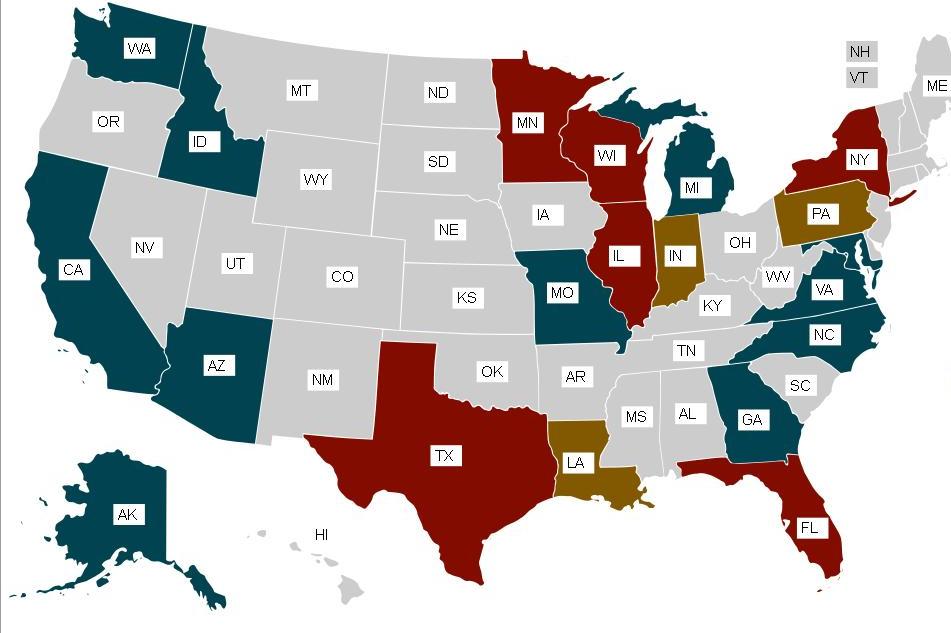
In addition to the police, federal law enforcement agencies, the military and various other intelligence agencies are also using Stingrays for their own purposes. According to the American Civil Liberties Union, the device is being used in 42 law enforcement agencies in 17 different states, all purchased under ‘anti-terror grants’ as the cost of each unit varies from $15,000 to $130,000.
Image Source: Wikipedia – A US map showing the usage of Stingray by law enforcement agencies (red being the highest).
Furthermore, this is not only limited to the US; the Sunday Times and Privacy International have reported, “The usage of Stingrays and IMSI catchers has reached Ireland, against the Irish Garda Síochána Ombudsman Commission (GSOC), which is an oversight agency of the Irish police force Garda Síochána.”
Cloak of Secrecy
Listening to people’s calls is one thing, but keeping this secret from the court systems is a complexly different game. In 2014, police in Florida revealed that they had used such apparatus at least 200 times since 2010, without telling the courts or acquiring a warrant. The American Civil Liberties Union has filed increased requests for the public records of Florida law enforcement agencies concerning their merit of the cell phone tracking devices. Naturally, local law enforcement as well as the government have opposed legal appeals for information regarding the use of Stingrays.
In June of 2014, the American Civil Liberties Union distributed intel from court with reference to the broad utilization of these gadgets by Florida police. After this, the US Marshals Service snatched the local police’s reconnaissance mission records to keep them from showing up in court.
Image Source: Google Image – An image showing how Stingray mimics a cell tower which allows the cellphone to connected to the device.
The ACLU has stated that an illegal government reconnaissance mission of this scale should not be kept hidden from the population nor should law enforcement be permitted to conceal its use from judges.
SOURCES:
http://www.wired.com/2014/03/stingray/
http://arstechnica.com/tech-policy/2013/09/meet-the-machines-that-steal-your-phones-data/
http://www.wsj.com/articles/SB10001424053111904194604576583112723197574
www.egov.ci.miami.fl.us/Legistarweb/Attachments/34769.pdf
https://www.documentcloud.org/documents/1282619-11-10-17-2011-u-s-v-rigmaiden-cr08-814-phx-dgc.html
https://www.documentcloud.org/documents/1282618-10-08-23-2010-fl-v-thomas-2008-cf-3350a.html
http://www.cryptome.org/gsm-crack-bbk.pdf
https://www.documentcloud.org/documents/1282618-10-08-23-2010-fl-v-thomas-2008-cf-3350a.html
http://papers.ssrn.com/sol3/papers.cfm?abstract_id=2440982
https://www.aclu.org/node/37337
http://www.businessinsider.com/stingray-phone-tracker-used-by-police-2015-3
http://www.newser.com/story/203094/cops-quietly-using-secret-spy-tool-to-find-suspects.html
http://www.nytimes.com/2015/03/16/business/a-police-gadget-tracks-phones-shhh-its-secret.html?_r=1





You are not anonymous.
This is just sharaholic blog spam.
While such technology is rather scary, discovering it is the first step of getting around it. I wonder exactly how long it’ll take for someone to create a way to avoid such devices.
It didn’t take long at all, lol… check out AnonCom on IndieGoGo. We are getting around these devices. I have my Android programmed to show my location as being in their headquarters.
Thank you for sharing this information. There is a great informative video here with collaborating news about surveillance from many sources. https://www.indiegogo.com/projects/anoncom-extreme-encrypted-private-android-phone/x/9855548
Hi I am gaining a lot of info from your FB page, and personally am forced to ask myself many questions about our society. Would you please try to make your FB pages reproducible by printing, they are virtually unreadable at present when printed out.
Can u hack king 5 news and can you hack my phone so I can see and do what ever I want
I thought the phone had to be 2G compatible as the stingray connects and then tricks the phone into 2G connection there by routing past the 3G security features.
I wanna be anonymous