
We at the Anonymous Headquarters have jotted down a list of tools that one requires for penetration testing, along with other hacking resources that are put together by some truly best programs in existence today. These tools can simplify many of the challenging jobs which require our immense time and constant coding – with these and more software available they take our painstaking tasks and make it easy.
So, without further waiting, let us start off with list:-
The Social-Engineer Toolkit
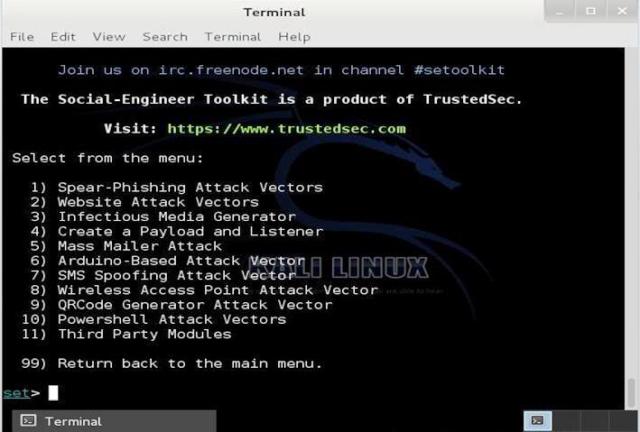
Also highlighted on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is definitely a state-of-the-art platform for replicating several varieties of social engineering strikes such as phishing attacks, credential harvestings plus a lot more. Elliot, the protagonist from Mr. Robot, is using SMS spoofing tool available in the social engineering toolkit. However, this Python powered application which happens to be a common means of social engineering penetration checks with over a million downloads. The attacks produce mask e-mails, malevolent internet pages and much more.
To download SET on Linux, type the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
Outside of Linux, Social-Engineer Toolkit is to some extent supported by Windows, Mac, and Linux.
Maltego
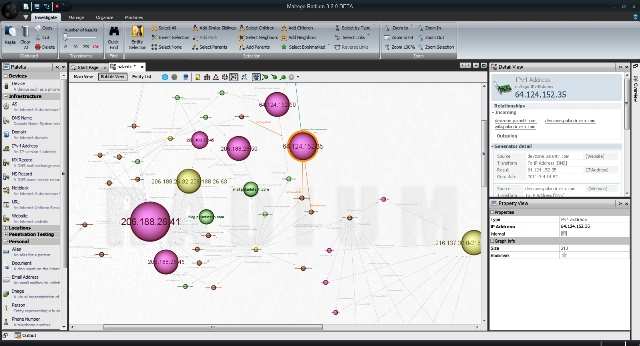
This open source forensics program provides arduous exploration and insight mapping for coating an image of online hazards surrounding you. Maltego does really well in revealing the complexness and intensity of points of failure in your system and the encompassing setting.
Maltego is a superb security program that evaluates the real world connections amongst individuals, businesses, online websites, domains, DNS, internet protocol address, documentation and everything in the middle. Dependent on Java, this unique tool works with a convenient, usable visual interface with many modification selections while scanning.
This software is available to download on Windows, OS X, and Linux platforms.
Nessus Vulnerability Scanner
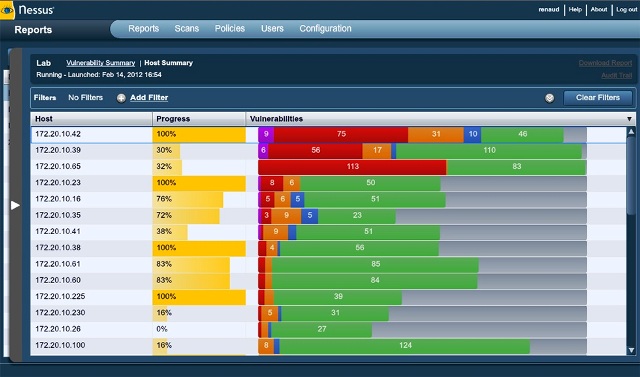
This leading free of charge security program of works jointly with a client-server framework. Brains at Tenable Network Security made this possible; the software is amongst the preferred vulnerability scanners available to us. The brand provides distinctive software, everything a security specialist needs to get started – Nessus Home, Nessus Professional, Nessus Manager and Nessus Cloud.
However, utilizing Nessus, anybody can scan several kinds of weaknesses including remote access defect recognition, misconfiguration notification, denial of services to prevent TCP/IP load, organizing of PCI DSS audits, virus discovery, hypersensitive data queries, etc. To start a dictionary breach, Nessus then takes extra help from Hydra externally. Besides the above revealed basic features, Nessus may be applied to browse several systems on IPv4, IPv6 and cross networks. One can plan a scan so it may execute at the time that was added as well as re-scan each or a subsection of earlier reviewed hosts by making use of particular host checking.
Nessus Vulnerability Scanner is compatible with a number of operating systems most notably Windows 7 and 8, Mac OS X, and prominent Linux distros such as Debian, Ubuntu, Kali Linux &, etc.
oclHashcat
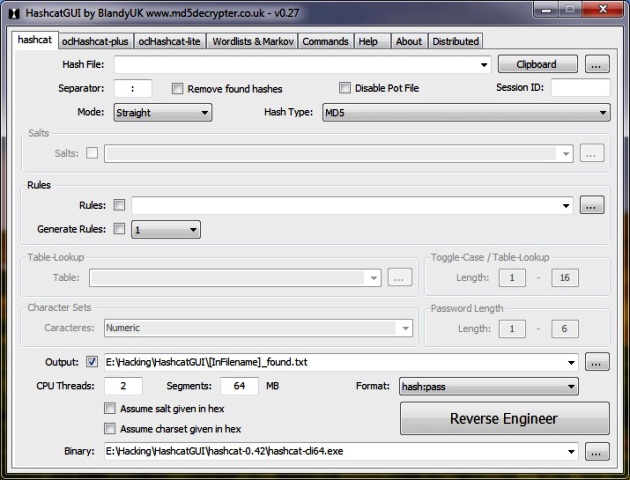
If you are a big fan of password cracking, then you might be familiar with oclHashcat password breaking program. Although this software can be described as a CPU-based password cracking instrument, oclHashcat is its cousin that uses your GPU instead of your CPU power. However, oclHashcat dubs itself world’s speediest password cracking instrument with industry’s first and only CPGPU dependent system. For making use of the program, NVIDIA consumers should have ForceWare 346.59 or the ones after that while AMD consumers should have Catalyst 15.7 or any versions installed after that.
This software uses the attacks listed below:-
Hybrid mask + Dictionary Attacks (& vice versa)
Brute Force Attacks
Straight Attacks
Combination Attacks
Pointing out a great additional element, oclHashcat is an open source instrument with Massachusetts Institute of Technology license which enables a quick integration for the popular Linux distros.
This software is available to download on Windows, OS X, and Linux platforms.
Wireshark
This sniffing software is a popular packet altering program which finds weaknesses inside a network and pushes firewall set functions. Utilized by a large number of security experts to evaluate systems, live packet recording as well as deep checking of numerous protocols. Wireshark enables you to study real-time data from your local area network to PPP/HDLC, IEEE 802.11, ATM, USB, Token Ring, Bluetooth, Frame Relay, FDDI, as well as others.
Wireshark is free to download and like any other great software, it is opensource & for those who like it old school you can use its command line version labeled as TShark. This GTK plus.
This software is available to download on Windows, OS X, and Linux platforms.
Nmap
Nmap or Network Mapper lies in the group of a port scanning tools. This software is also, free and open source. It by far on the most prominent port scanning tools available which enable effective networking detection and security audit. Employed for an array of solutions, the port scanner makes use of raw IP packets to discover the hosts located on a circle, the systems they are using, the services they are using, and firewalls used all of this is information comes to the screen after a simple scan. In 2015, Network Mapper obtained numerous achievement awards and was also showcased in several movies particularly, Die Hard 4, The Matrix Reloaded plus many others. Easily obtainable in the command line, the port scanning software is available in an enhanced graphical user interface called ZenMap.
This software is available to download on Windows, OS X, and Linux platforms.
Acunetix WVS
This Web Vulnerability Scanner guessing by its category it has the ability to scan and discover the faults in your website(s) by checking them if they are vulnerable. This multi-functioning program searches the online web page and examines and tests for vulnerabilities such as SQL Injections, Cross Scripting, as well as other weaknesses. This quick and easy to use program scans websites that are built on WordPress since there are more than 1200 plus weaknesses in WordPress alone. The software features a login series recorder that enables a person to get inside the password defended sectors of the online site. The revolutionary AcuSensor development employed in this program which enables you to minimize the false positive rates. Such functions are making Acunetix WVS a liked testing tool amongst the community
This software is available to download on Windows XP and its later editions.
Metasploit
At the end Metaspoilt takes this list – this gem of a tool needs no introduction in the community of security auditors, testers or hackers for that matter, instead of labeling it as a tool it is a whole different world Metasploit is a group of exploit resources, one can call it a substructure which one can harness to establish one’s personally customized methods. This free program has become one of the most favored online security systems which means it gives a person the ability to discover vulnerabilities at various systems. Metasploit is supported by over a hundred thousand customers and members that aid you by updating its database so its users can help maintain security.
This list of the hacking tool allows you to mimic real-world problems to identify the weak spots and what can you do to defend them. Very useful for finding vulnerabilities in all kinds of operating systems the ones in your laptop to the ones in your cell phones, Metaspoilt points out these issues with Nexpose closed–loop incorporation making use of leading remediation reviews. By using this free and open source framework all a user needs to do is be creative and the possibilities are endless with this one of a kind security testing tool.
This software is available to download on Windows, OS X, and Linux platforms.
Here is an additional list worth mentioning
Password Auditing:-
a) Aircrack
b) Cain & Able
c) John the Ripper
Sniffers:-
a) Cain & Able
b) TCP Dump
c) Kismet
d) Ettercap
e) NetStumbler
f) dsniff
g) Ntop
h) Ngrp
i) EtherApe
j) NetworkMiner
k) P0f
l) inSSIDer
m) KisMAC
Rootkit Detectors:-
a) Sysinternals
b) Tripwire
c) DumpSec
d) HijackThis
e) AIDE
Vulnerability Exploitation Tools:-
a) w3af
b) Core Impact
c) sqlmap
d) Canvas
e) sqlninja
f) Netsparker
g) BeEF
h) dradis
Wireless Tools:-
a) Aircrack
b) Kismet
c) Netstumbler
d) inSSIDer
e) KisMAC
Source: Security Tools
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (The Best Hacking Tools) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





Dear anonymous, With due respect I have been following anonymous for a year now. and i have been watching free live stream matches for more than 2 months.
so is there any way or vice versa to find that sites is malicious
I’ve been looking for a good list of tools (particularly crackers) for a while now. Thanks for compiling this.
Hmmm Seems nice content but its not enough there is more in the top list check this list of Hacking tools and add some more here.
Please help Anonymous,we r learning from u teach us more make us prof couse we understand what u do and we hope help
we don’t forget
kindly help me with some sites, i need some tutoring
Thanks for sharing these latest hacking apps
Tnx M8! ./.
Good
i m very crazy about hacking its my passion thanx for everything….!!!!
Please bro, do you have idea any of virus for spamming?
help me hak plz i ned to ga to a web
Aha! kinda innovative for me…
WE ARE LEGION brother.
How do i hack a fax machine to intercept fax so i get copies of all documents.
Any help?