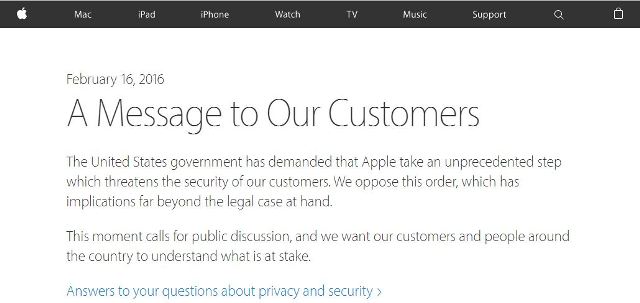
On February 16, Tim Cook, the chief executive officer of Apple, published a report that said Apple must take unprecedented steps in creating a backdoor for iPhones; something that Cook regards as cancer in the software world, and at Apple they take security very seriously. Since the production of the revolutionary iPhone 3GS, the company has developed security within the electrical components and the software parts of their iPods, iPhones & iPads.
Every single Apple product running their firmware has a specialized Advanced Encryption Standard (AES), which is a 256-bit cryptographic system that is placed among the hard drive and primary model storage. The system operates along with the SHA-1 crypto hash characteristic, which happens to be employed in the physical components in order to cut off expensive cryptographic operations. So, in short, the iOS information security is administered at the application stage, and harmonizes with the components and firmware security in order to deliver the perfect level of security to its users.
However, when data security is equipped, each file is connected with a particular pattern that helps a different volume of admittance and safeguards information when it does not require access. The encoding and decoding functions linked to each session are predicated on an elaborate key structure, which uses the iPhone’s or the iPod’s unique identification system based on the user’s assigned password or PIN, along with a group key, file process key as well as pre-document key. The pre-document key is designed to encode the information inside the document. The group key is cloaked over the document key, and is placed in the document’s meta-information. The document system key is utilized to secure the meta-data, password and the group key.

For instance, a brute force intrusion on a system that runs on a 7 figure numerical PIN, can take anywhere between 4 and 9 days—remember, Apple’s firmware imposes increasing time hold ups in order to prevent such activities. Conversely, an 8 digit password or PIN that consists of numerical figures and small letters, can take between 45 days and 3 months. So, naturally, a 9 digit password or PIN, consisting of numbers and small letters, can take between 1 year and 2.5 years to break.
A password consisting of 10 digits – again combing a mix of letters and numbers, will take between 12 years and 25 years. And if your password is 11 digits strong, the code breaking software is going to take between 127 years and 253 years. Then again, if you have a password or a passphrase that is made up of 12 digits, the code breaking software can take between 1200 years and 2500 years. And if you choose a password that is made up of 13 digits or more, it will take between 12,000 and 25,000 years. Even if a programmer had the ability to jailbreak an iOS device and shunt the PIN or the password, the information would still be unobtainable, given that the programmer would certainly not have the password.
#Apple vs #FBI: A Closer Look – Late Night with Seth Meyers ?????????https://t.co/YvN7BfKBxG
— Anon.Dos (@AnonDos_AnonHQ) 27 February 2016
Since the launch of iOS 7, the firmware that was released on the 18th September 2013, iOS consumers can enjoy additional control over applications. Even though encoding elements do not change the revolutionary operating system, the iOS demands a user’s approval prior to a newly downloaded application that has the ability to access private information such as the camera, notes, reminders, calendars, pictures and other applications which use contact details.
After iOS 7, people were able to alter information accessibility for particular program(s) in the smartphones controls. However, in order to fully benefit from iOS encryption, the user must keep complete command over the applications used on the iOS system, especially the applications that are used to manage your business’s classified information. If you are careless about it, don’t be surprised when hackers and government agencies begin snooping on your credit card information, pictures, messages and anything that can affect your life. So, the longer and stronger the password, the longer it takes it to crack.
TIP: IF YOU ARE USING A LINUX OS OR A OS x, THEN YOU CAN GENERATE A PASSWORD BY TYPING THIS IN THE COMMAND TERMINAL.
python -c ‘from random import SystemRandom as r; print(r().randint(0,10**11-1))’
This command will allow the system to generate a random 11 digit string password for you.
Source: The Intercept, Apple
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (Toughen Your iPhone Password To Better Protect Your iPhone From The FBI) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.




