
A unique malware that is dependent on USB devices has been discovered; however, this program has employed special programs, allowing it to remain undetected. In addition, the malware can also get a grip on the movement of portable variants of programs, such as stand-alone editions of portable Skype, Linux Live USB Creator, Data Crow, Portable Photoshop, etc. This seriously damaging program is referred to as Win32/PSW.Stealer.NAI, or is more commonly known as the USB Thief.
Professionals from ESET were the first to identify this malware, and one of their researchers, Thomas C., explains that the malware’s script is not just designed to survive in a USB stick, but it will also attempt to reproduce itself on the target device. Then again, once it has successfully cloned itself onto the target system, this malware will not duplicate itself on any other USB stick.
Win32/PSW.Stealer.NAI was created to focus on air-walled computers. These systems (which primarily consist of only two units) are there to ensure that they keep the network physically isolated from an unauthorized network(s). With that said, the absence of the cloning ability in the malware signifies an uncommon trademark and intention.
However, the security company’s report also signifies that the malware is liable to stay on a solitary USB device because it does not, or should not, be replicated or backed up. As a result, the creator(s) retains sole ownership of the malware. The architecture of the malware, its complex execution and multiple stages of security make the malware extremely hard to identify and evaluate. The malware uses encoding to not only conceal itself from scanners that are meant to scan things faster, it also uses it to protect its operations on unidentified or unauthorized USB drives.
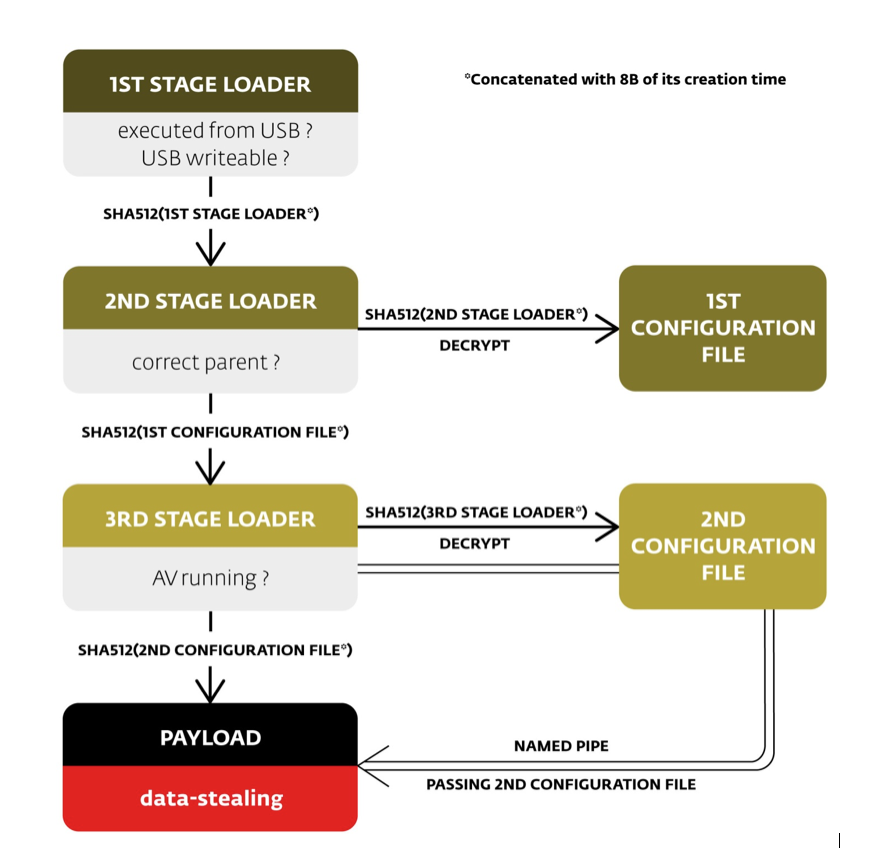
Furthermore, this malware was created to extract information from the target—‘air-walled systems’—despite the fact that details surrounding the malware’s methods of communicating with the servers that the information should be sent to, were not mentioned in the ESET’s report. Let us believe for a moment that the hacked information is not being sent to a foreign server. Ultimately, this approach would appear to demonstrate an inside job, which would mean that the malware would be sending information to a local level machine.
However, the most astonishing component of this malware is its close link to portable editions of software such as Mozilla Firefox, and particularly the discontinued portable edition of TrueCrypt. Such portable applications are developed to reduce their impact on the computers that store and execute them. Therefore, an assault within their library will ultimately cripple the safety disposition backing them.
‘The output destination must always be on the same removable device. In the case we analyzed, it was configured to steal all data files such as images or documents,” states the report published by ESET. “The whole Windows registry tree (HKCU), file lists from all of the drives, and information gathered using an imported open-source application called “WinAudit”. It encrypts the stolen data using elliptic curve cryptography.”
The study recommends that USB ports be deactivated physically—unplugging them from the motherboards—or via their driver settings. Although this can be very troublesome in today’s day and age, such tight procedures must always be applied to air-walled machines or personal computers.
Source: The Hacker News, We Live Security by ESET Security
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (A USB Malware That Can Steal Your Data Without Being Detected) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





Do you guys teach out how to hack? i need to get an assholes ip. so i can DOS him.
Go back to reddit, kid