If you still believe that the NSA is all about guarding you from terrorists, or even securing the US against foreign intelligence agencies, think again.
The FBI is investigating a recent security breach, with independent researchers believing that a back door created by the NSA had allowed foreign governments to spy on US government communications.
California-based Juniper Networks manufactures the networking equipment that corporate and government systems rely on.
On Thursday, it announced that it had uncovered a back door in its ScreenOS firewall software. Attackers were able to decrypt encrypted traffic that was sent and received via Juniper’s equipment.
This announcement came during an FBI investigation into whether foreign governments were trying to access the confidential communications of employees at US agencies. Juniper is cooperating with the Department of Homeland Security over the matter.
The Department of Justice, Department of Defense, the FBI and the Department of Treasury use Juniper’s routers and networking equipment.
According to CNN, an official called it “stealing a master key to get into any government building.”
While the US itself has been quick to blame the backdoor on foreign governments like China and Russia due to the high level of sophistication, Ralf-Philipp Weinmann (who is the founder of Comsecuris, a German security firm) wrote in his blog that he believes that the evidence points towards the modification of an existing backdoor that was embedded into the equipment by the NSA.
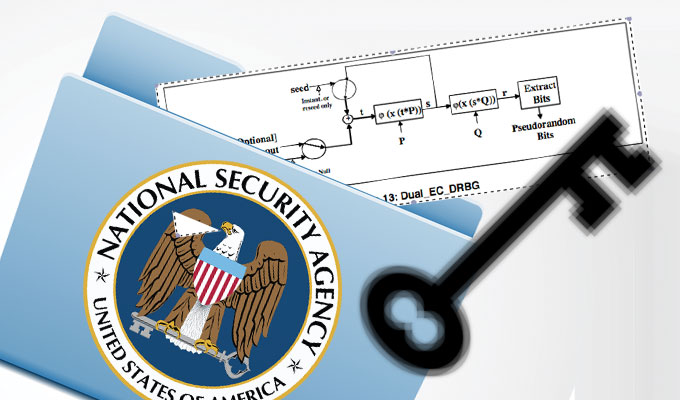
Dual_EC is a pseudorandom number generator that Juniper and others use to encrypt traffic; the NSA is believed to have placed a US government-approved weakness in the system. Juniper was itself partly responsible- it had made an alleged error in the configuration of the VPN encryption scheme, which allowed the attack to occur.
Of course, the NSA or its partners in the UK and Israel could well be behind the attack- they have the requisite know-how and resources, on top of placing an exploitable weakness into the system to begin with.
However, a gamut of unnamed US officials have come out to deny that the US spy agency was behind it– according to CNN anyway.
A pseudorandom random number generator isn’t truly random; it depends on an algorithm to generate a series of numbers which seem to be random, based on a “seed” or set of initial numbers. The backdoor worked by altering Juniper’s source code to change the seed that generates a key that is used to encrypt data.
Together with a second key that is only known by the attackers, it was used to decrypt Juniper’s VPN traffic.
Dual_EC’s weakness is well-known; a Microsoft employee named Dan Shumow had even given a speech about it almost a decade ago in 2007.
Shumow stated that it was possible to predict the random number that was being generated, due to problems innate to Dual_EC itself- he devised an experiment which showed that it was easy to guess any key created with the Dual_EC.
Johns Hopkins professor Matt Green even stated in 2013 that “in the course of proposing this complex and slow new PRNG where the only frigging reason you’d ever use the thing is for its security reduction, NIST forgot to provide one.”
In spite of all that, it was still approved by the National Institute of Standards and Technology for inclusion in a standard used to encrypt government classified communication- a cause that was championed by the NSA.
Sources: Wired, RT, Ars Technica
This Article (Oops: How The NSA Helped Foreign Governments Spy On The US) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author(CoNN) and AnonHQ.com.




run by zionist jews who owed nsa by 97%,in contracts, of course these zionists will
Helped Foreign Governments to Spy On The US, these is just the beginning, and it;s going to get a lot worse.