
Scientists from Rochester University have created a way to transfer data via photons by using twisted light. This phenomenal achievement is possible due to the fact because the experts used the OAM or Orbital Angular Momentum of the photons to encode data on them, instead of encoding it more frequently used emission of light.
Quantum cryptography guarantees much safe and stable communication, the initial step in such a setup would be the use of QKD or more commonly known as Quantum Key Distribution Quantum Key Distribution. This system makes sure that both the transmitter and the recipient – usually referred to as Alpha & Beta – are communicating in a unique way because of which only they know what is being sent to them. Plus Alpha and Beta are the only ones who hold the password or the key to the message(s), and the networks are set in a way to which the existence of any other secret listener(s) will be identified.
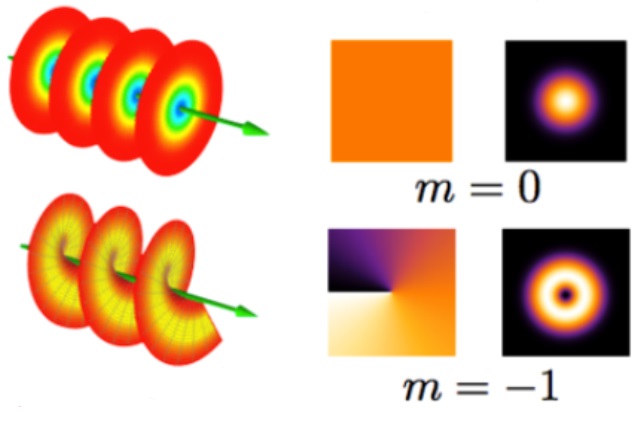
A paper that was published in the New Journal of Physics on the March of this year in which Mohammad Mirhosseini (Doctoral Student at University of Rochester Dept of Quantum Optics & Quantum Information Science) described via a proof of rule test that showed that by utilizing Orbital Angular Movement to scribe data rather using the same old polarization or emissions technique; unravels the opportunity of a much better Quantum Key Distribution. Mirhosseini further defined that because of this he and his colleagues were able to create a unique set of encoded alphabets. He further went on saying that these were seven symbols or letters that were created utilizing both their angular positions and orbital angular momentum. In short – the accurate information is only revealed to Alpha only if he encodes the data using an exclusive basis and Beta also calculates on that same basis.
Furthermore, in a quantum key distribution, as soon as they have produced a shared key or a password, Alpha and Beta tell each other the characters that both of them used in their password or the key. Then further on they exchange the letters as to which ones were used for sending and vice versa. The only part they get to keep are of the similar alphabets that were utilized for sending and receiving data. And with the common letters that were received by both that parties are then compared and used for producing a safe password, or a key, and that can be used for encrypting the message(s).
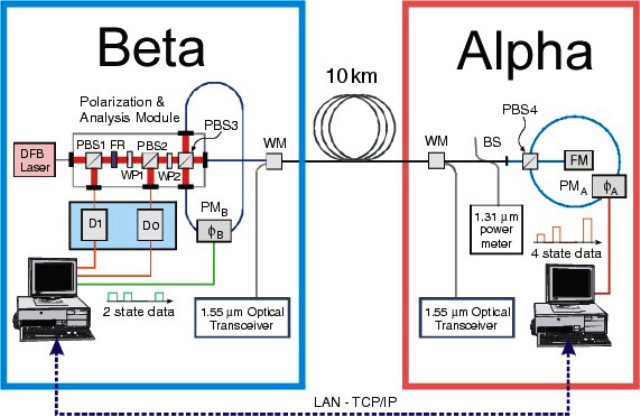
However, if let’s say the commutation between Alpha and Beta was breached for some reason, then there shall be a variation amongst Alpha nd Beta’s passwords, and they would have to sacrifice a short part of their code. Once they have shared this publicly and have identified any disparity. This means of finding an error, or a miss match would allow them to determine whether if their connection is protected or not.
Mirhosseini bonafide by stating that his experiments show that it’s possible to utilize twisted light for quantum key distribution that enhances the volume when in comparison to the polarization or emissions.
Furthermore, he says that the real-world challenges are not straightforward to overcome at the moment, but when it’s about Quantum Key Distribution, he gets thrilled about the options that present themselves.
Source: The Hacker News – Google Scholar – Wikipedia QKD – Wikipedia QC – Wikipedia OAML
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (An Unbreakable Encryption) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





Hi. I love the site and the open content, but I believe a more stringent editing procedure is needed. I come across too many articles with glaring grammatical issues the quickly degrade the integrity of the articles.
Thanks.
*that. See, I even need an editor!