
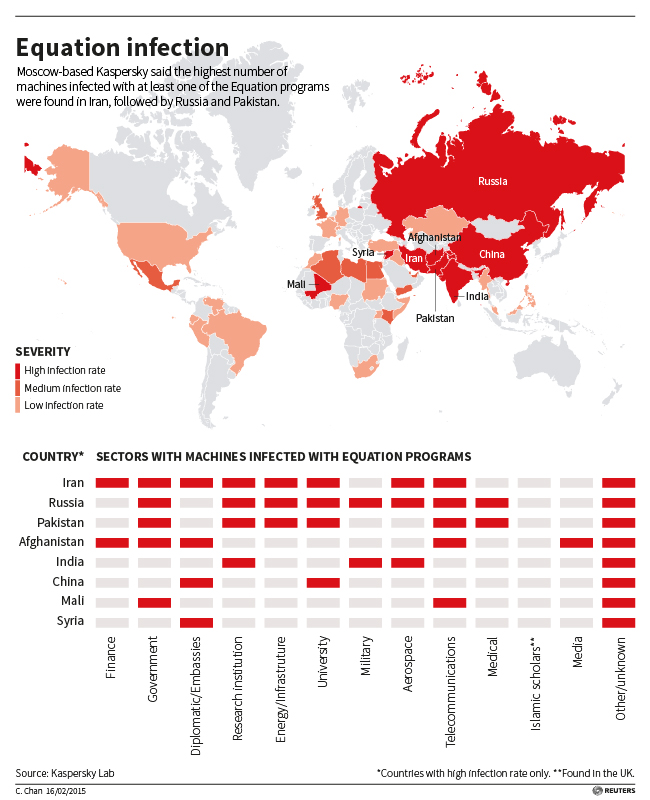
A hacking group, named Equation, with ‘superhuman technical feats’ indicating ‘extraordinary skill and unlimited resources’, has compromised the firmware of hard drive controllers from Western Digital, Seagate, Toshiba, IBN, Samsung and many other top manufacturers. The 14-year cyber espionage campaign associated with the US National Security Agency hid spying software deep within hard drives allowing NSA to snoop on personal computers in 30 countries with maximum spying in Iran, Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria.
The cluster of spying programs and Western cyber espionage operations were discovered and exposed by Kaspersky Lab. According to Kaspersky, the targets included government and military institutions, telecommunication and aerospace companies, banks, energy companies, nuclear researchers, media, Companies developing cryptographic technologies and Islamic activists. The campaign was closely linked to Stuxnet, the NSA-led virus that was used to attack Iran’s uranium enrichment facility.
Kaspersky revealed that the spies figured out how to lodge malicious software in the obscure code called firmware that launches every time a computer is turned on. The technique created a secret storage vault that survives military-grade disk wiping and reformatting.
By compromising jihadist websites, infecting USB sticks and CDs, and developing a self-spreading computer worm named Fanny, Equation spread other spying programs also. Lead Kaspersky researcher Costin Raiu said Fanny was like Stuxnet and that it was quite possible that Equation used Fanny to scrutinize targets for Stuxnet in Iran and spread the virus.
Kaspersky also identified several malware platforms used exclusively by the Equation group:
- EQUATIONDRUG – A very complex attack platform used by the group on its victims. It supports a module plug-in system, which can be dynamically uploaded and unloaded by the attackers.
- DOUBLEFANTASY – A validator-style Trojan, designed to confirm the target is the intended one. If the target is confirmed, they get upgraded to a more sophisticated platform such as EQUATIONDRUG or GRAYFISH.
- EQUESTRE – Same as EQUATIONDRUG.
- TRIPLEFANTASY – Full-featured backdoor sometimes used in tandem with GRAYFISH. Looks like an upgrade of DOUBLEFANTASY, and is possibly a more recent validator-style plug-in.
- GRAYFISH – The most sophisticated attack platform from the EQUATION group. It resides completely in the registry, relying on a boot kit to gain execution at OS start-up.
- FANNY – A computer worm created in 2008 and used to gather information about targets in the Middle East and Asia. Some victims appear to have been upgraded first to DOUBLEFANTASY, and then to the EQUATIONDRUG system. Fanny used exploits for two zero-day vulnerabilities which were later discovered with Stuxnet.
- EQUATIONLASER – An early implant from the EQUATION group, used around 2001-2004. Compatible with Windows 95/98, and created sometime between DOUBLEFANTASY and EQUATIONDRUG.
A former NSA employee told Reuters that Kaspersky’s analysis was correct, and that people still in the intelligence agency valued these spying programs as highly as Stuxnet. Another former intelligence operative confirmed that the NSA had developed the prized technique of concealing spyware in hard drives, but said he did not know which spy efforts relied on it.
NSA has in the past funded the development of other persistent attacks, especially as presented in NSA’s infamous ANT catalogue. Though the agency has multiple ways of obtaining source code from tech companies, it is not clear how NSA obtained the source code in this campaign. Whatever the case may be, there is no denying the fact that the exposure of these new spying tools could lead to greater backlash against Western technology.
Anonymous recommends: Protect your PC & mobile devices from hackers & governments & surf anonymously
Source:
http://pontiactribune.com/biggest-nsa-backdoor-exploit-ever-computer-now-nsa-gateway/




fuck i have a seagate hard drive and i live in norway am i safe
No. We already have your info. Also, stop watching so much porn.
Not safe. Hundreds of thousand of muslims and other crasy people live in Norway (like the guy who killed almost 100 young people on a island).
You know that guy was a hardcore christian radical right?
if you wanna talk crazy look at islam with 270 million killed
Confirmed. Consider an alternative to Asian scat porn. We watch what you watch. Pick something tasteful.
Do me next
That’s what she said.
That’s what she said.
SHOW ME YOUR MOOVES!!
Drink less and stop beating your wife.
The NSA have gone too far. This needs to stop.
I live in Ireland. Does that mean I’m safe?
No one is safe…i think
Depends … are you planning on blowing anything up?
Is the kaspersky resercher a romanian?….. Seagate hard drive and i’m living in romania….hope mine aint infected….dont want some crazy nsa agent to know what kind of porn i’m watching…
Canada, Fuck Yeah!
Nsa has crossed all lines, India too. Wow I think time for open hardware after opensource.
NSA has crossed all lines, I think its time for open hardware after opensource.
if the fda wants to see all my porn they go for it,
No one is safe! I have concluded that while technology upgrades are constantly moving forward and the sheeple are dumb enough to buy a new system every few years. The ONLY way we are to survive is to move backwards in technology! And with the super sniffers that are out hunting us these days it is important to have more than one PC. You have the one that is used for everyday life bullshit and being connected to the web via WiFi/LAN, then there is the one that you have for storage. Your storage PC should have absolutely no networking capabilities whatsoever and should be shut down and unplugged when not in use. Think of it as a massive drug deal where there are 2 different dealers in different locations one guy takes the money then you have to go get the product from the other person somewhere else. This way it can never be proved that the money and the drugs were ever linked.
yeah, Canada is suspiciously grey… but Mexico? Really? and what’s up with Japan? No, I mean, really… what’s up with them? funny guys xD
And Czech reupublic ? …. Noone cares about czech r. especialy hackers 😀
really, no one is safe even if no one is far from technology
Que carajos se puede hacer? por mas que naveguemos anonimante nuestra iunformacion ya la tienen los cerdos
Who’s IBN? Never heard of that company. This is really lacking in details, basically that’s every major HD manufacturer (even the giant IBN!) I followed this article all the way back to Reuters, still no hard info. Model numbers? Firmware lists? A scanning app to check? Something beside a vague list?
Here’s far more information: https://securelist.com/blog/research/68750/equation-the-death-star-of-malware-galaxy/