
It looks like there happens to be a typical scenario for viruses to advance…
Initially, hackers or programmers push out a frame of malware with standard features, to which that bit of malware functions silently for a certain amount of time, revealing virtually no destructive movement. Normally it comes to the attention of numerous security companies that update their anti-virus program soon after it is unleashed. However, the analysts approach is like another bit of possibly malicious script: absolutely nothing of special interest.
As time passes, the Trojan viruses (most of the time it is usually a Trojan) obtain extra functionality, carrying out more harmful attacks, compared to its predecessor. Over time, a huge attack plan begins – thus, a large number of systems get contaminated and following this, the Trojan virus performs its bawdy task. The degree of harm addressed here is subjectable to the form of the Trojan. It can end up being, perhaps a ransomware locking your data up and asking the user for a certain amount of money (usually in form of bitcoins). It could also be in the form of a banking malware robbing anything it can get from a debit or credit card. Acecard can also be used as a remote accessing tool for spying on you.

This had been the precise situation for Asacub (to read more on Asacub, please click here), which initially surfaced as a simple phishing program and then evolved into a financier program with functionality, compared to a big system. In a short time, the Acecard malware has adopted a similare route, looking like it’s rather more serious than Asacub.
Acecard happens to be a form of an Android banking Trojan group comprised of many adjustments of the identical Trojan. Much like nearly all banking trojan viruses, it executes itself by overlaying smartphone banking programs with its personal phishing varieties, which the naive consumer will fill in their personal and financial details. As soon as a user clicks submit (or an identical action) — the logged information is compromised, and the hackers either advance your money from those cards into their fake accounts, or market out your information to the highest bidder.
This Android-based malware stands apart from the competition for two primary reasons:
Firstly, to begin with, the typical banking Trojan viruses often have the capability of superimposing just around a few cellular financial applications; whereas Acecard knows more than 25 various financial institutions, as well as many payment systems. Acecard may also be programmed to launch the control host, concealing any software, hence the level of assaulted applications may be higher.
Secondly, it will not restrict its program to monetary applications. Acecard could be employed for phishing mobile social websites programs like Facebook, Messenger, Twitter, Instagram, Skype, etc., as well as the PayPal application and the Gmail software. What’s more, it can overlay Google Play Store and Google Play Music with a counterfeit window.

This ‘program’ is dispersed not by the typical electronic mail spamming system, but by masking itself as something quite helpful. For instance, feigning as a Java application that you are familiar with. If you are thinking that Acecard comes in the form of updates from various unofficial websites, you are wrong. According to Kaspersky, they found Acecard to be lurking on Google Play Store, as well.
Acecard was discovered at the beginning of 2014, and in those days, as we have previously mentioned, it was exhibiting absolutely no harmful activity. It took the programmers more than a year to turn Acecard into the menace it is today; incorporating unique functionality from one variation to another one, updating it for better attacks and stealth. Analysts have discovered a lot more than seven separate variations of this threat; each new version or update is packed with advanced ability to attack its target maliciously. The present day types are extremely effective, so much so, that many security and online research analysts have labeled Acecard among the most hazardous and serious threats to smartphone users today.

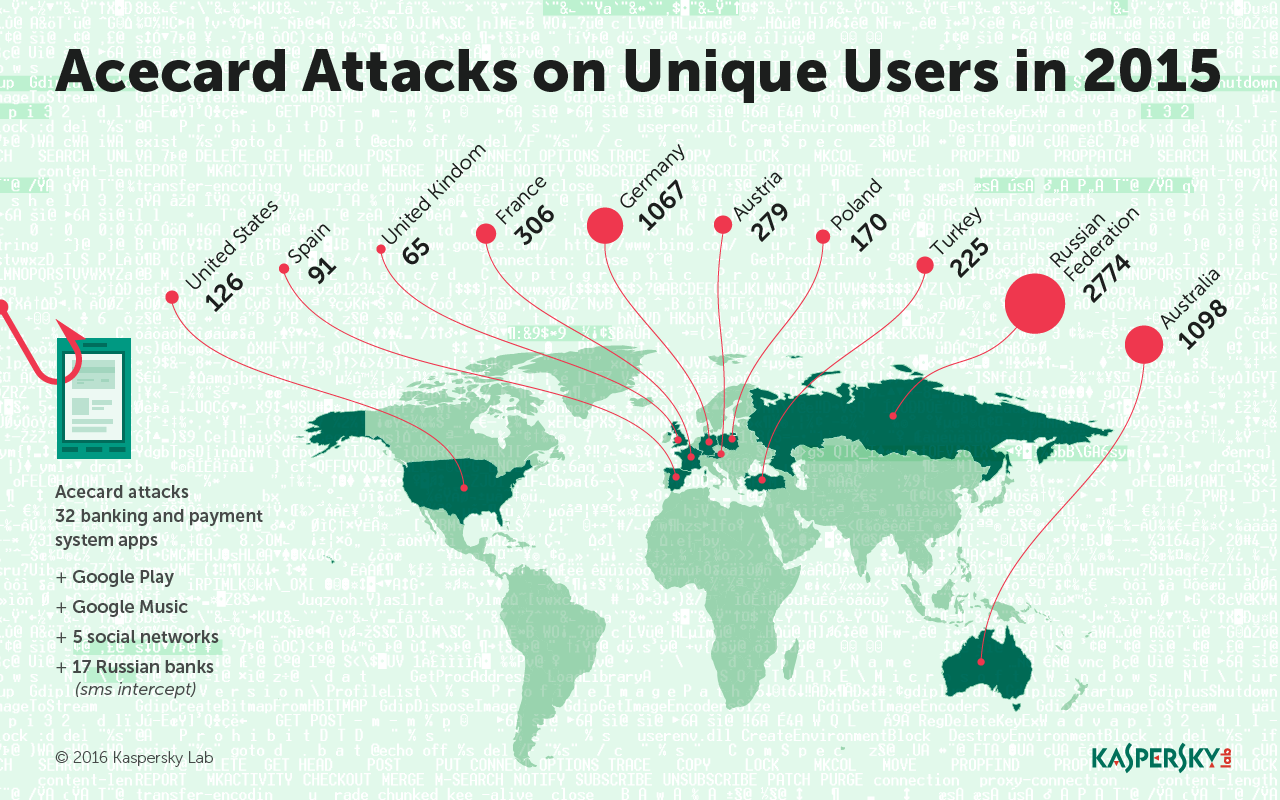
However, last May, when the Acecard assault started off, more than 5,000 users were victimized in the space of five months. The malware is solely accountable for a large boost in the volume of online financial attacks in Australia, with remaining targets in Russia, Germany, Austria and France. On the other hand, according to security specialists, the programmers and hackers that designed Acecard are most probably from Russia.
Unfortunately, there is no manual way for you to remove the Acecard, once infected. However, there are many paid security suites that offer complete protection.
Here is some advice that can offer you protection before trouble hits. we recommend that you follow the steps below:
Always take note of the application(s) you install or even buy. Android Marshmallow offers a great feature where it prompts you with the permissions from the application, which needs to be granted by you. Also, some versions of Acecard do not show anything except the Flash Player icon when functioning.
Do not download programs from sketchy or bogus stores, or online sites that offer you paid software for free. Even if you’re on the official Google Play Store, do not install applications that you do not trust or require. In fact, before you do, always make sure to read the reviews of the application first, so you get an idea. Hackers have the ability to go over Google Play’s security system.
Use an effective overall security scanner or an anti-virus. Many paid and free security solutions applications detect all recognized variations of Acecard and therefore would function as a satisfactory security against Acecard, along with other malware programs.
If you want to read a detailed technical article on Acecard and its functionalities please click here.
Source: Kaspersky Labs, Secure List
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This article (Acecard is the Android Nightmare that can Steal Your Credit Card Information) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.




