
What is a ‘denial of service’ attack (or ‘DOS’ attack)? To break it down as simple as possible, it is a malicious attempt wherein hackers make the available resources on a network or a server unavailable to the actual users; commonly by disturbing the services of the host connected to the internet.
However, there is more to it than simply unloading packets and bombarding them at a set internet protocol. The DOS attacks have three basic types:
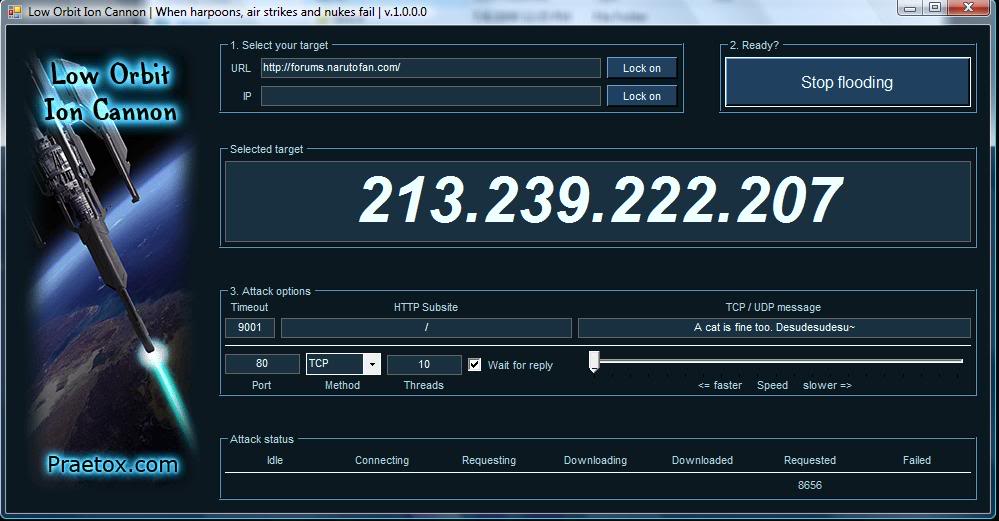
Image Source: Google Images – Low Orbit Ion Cannon (LOIC) is an open source and entry level network stress testing and denial of service attack application, written in C#. LOIC was initially developed by Praetox Technologies, but was later released into the public domain, and now is hosted on several open source platforms. (http://sourceforge.net/projects/loic/)
1) Volume Based Attacks (Measured in Bits/Second), the main purpose of this is to saturate the bandwidth of the target. It includes a few of the following methods:
- UDP Floods: ‘User Datagram Protocol’ is a connection-less computer network protocol. And it is used for checking applications listening at that port. It is also used to see if no application listens at that port. And finally, to reply with ICMP Destination Unreachable Packet.
- ICMP Floods: It sends packets without waiting for replies. This attack is good for consuming both incoming and outgoing bandwidth, resulting in the victim’s overall system slowdown.
- Spoofed Packet Floods: ‘Spoofing’ attack is a broad term. It consists of IP, DNS & ARP attacks. But we will just stick to the basic of it. This attack is used to mimic other devices or users on a network in order attack network hosts, hack information and spread viruses or bypass access controls.
Image Source: YouTube – A rad visualization of Distributed Denial of Service Attacks
2) Protocol Attacks (Measured in Packets/Second), this technique consumes actual server resources, such as firewalls and load balancers. It includes a few of the following methods:
- SYN Floods: This attack is possible due to the vulnerability present in the TCP. The flooding is done by sending multiple SYN requests (with no responses given back to the sender) and the host system waits for acknowledgement. Since it is unable to do that, a new connection can be made and ultimately results in a denial of service.
- Ping of Death: This attack requires the attacker to send many malformed or malicious pings to a computer.
- Smurf Distributed Denial of Service (DDOS): ‘Smurf DDOS’ is a distributed attack, sending large amounts of ICMP packets with the intended victims’ spoofed source IPs broadcast to a computer network using the IP broadcast address.
If you spend more on coffee than on #ITSecurity, you will be #hacked. What’s more, you deserve to be hacked.
— Anon.Dos (@anondos_) February 19, 2015
3) Application Layer Attacks (Measured in Request/Second), is a way in which the hackers send a ‘legitimate request’. The main purpose: to crash the web server. It includes few of the following methods:
- Slow Loris: This tool can be used on a low bandwidth network but is a highly targeted attack, enabling one server to take down another, thus creating a chain – without affecting other services or ports on the targeted network. It simply holds as many connections to the targeted web server, keeps them open for as long as possible and sends only partial requests of HTTP headers but never completes any request. This overflows the maximum connection pool and leads to denial of additional connections from legitimate clients.
- Zero Day or Zero Minute Distributed Denial of Service Attack: These attacks are simply widely unknown or new attacks and this is very useful for hackers as the vulnerabilities do not have a solution yet.
- HTTP Flood: In this attack, the hacker checks for seemingly legitimate HTTP GET or POST requests to attack the server. This technique does not use packets, spoofing or reflection techniques and require less bandwidth to bring down the targeted website or server. The attack is most effective when it forces the server or application to allocate the maximum resources possible in response to each single request.
- NTP Amplification: In NTP Amplification attacks, the perpetrator exploits publicly accessible Network Time Protocol (NTP) servers to overwhelm the targeted server with User Datagram Protocol (UDP) traffic. In an NTP amplification attack, the query-to-response ratio is anywhere between 1:20 and 1:200, or more. This means that any attacker that obtains a list of open NTP servers (e.g. – by using tool like Metasploit or data from the Open NTP Project) can easily generate a devastating high-bandwidth, high-volume DDOS attack.
Anonymous recommends: Protect your PC & mobile devices from hackers & governments & surf anonymously
SOURCES:
http://ftp.ntua.gr/mirror/technotronic/denial/smurf.c
http://tools.ietf.org/html/rfc2827.html
http://www.cert.org/advisories/CA-1996-01.html
http://www.veracode.com/security/spoofing-attack
http://ha.ckers.org/slowloris/
http://en.wikipedia.org/wiki/UDP_flood_attack
http://en.wikipedia.org/wiki/Denial-of-service_attack
http://www.webopedia.com/TERM/D/DDoS_attack.html





I was curious by the title. And yes you definitely kept it simple enough for anyone with basic network knowledge can understand. It’s a fun read for me since it reminds me of some attacks I have not seen in a while.
Is there a way to prevent ddos attack ? If Yes then plz tell what can be done.
A special hardware is to expensive, get a VPN. Anon recomand https://www.ipvanish.com/anonhq/?a_aid=anonymous , but i make my own VPN on a rented VPS form OVH.
Better known as script kiddies. 🙂
Aug. you already occupied … LOCK program HUSSARIA DURING . Polish with you. Only family .
Virus..
nexgen you got that to?
The Antivirus will detect it as a virus but relax its not one.
Thanks it’s a great booter
this was a great read , thanks a lot for sharing