
Written by: Anon.Dos
When it comes to selecting names for their new secret project these agencies show a flare for inattentiveness. Once in a while they acquire from Mother Nature, with monikers, for example, “Evil Olive” and “Egoistic Giraffe.” Or else they would appear to take their direction from Hollywood. Software called Treasure Map even has its own particular logo, a skull superimposed onto a compass, the eye holes sparkling in devilish red reminding me of a few films from Hollywood.
Christian Steffen, the CEO of German satellite communications organization Stellar PCS is looking at classified documents laying out the extent of something that is refer to as Treasure Map, a top secret NSA program. Stellar PCS gives web access to remote parts of the globe by means of satellite. He further lets us know that the organization, and some of its clients, has been infiltrated by the U.S. National Security Agency and British spy agency GCHQ.
The intelligence services could utilize this information to close down the web in African nations that are given access by means of our satellite associations, said by the chief engineer at Stellar PCS.
The stunning mission is portrayed in a report from the document of NSA that was informed by the whistle blower Edward Snowden. Treasure Map’s objective is to make an graphical guide of the worldwide web in almost real time. Employees of the alleged “Five Eyes” brainpower organization or simply intelligence alliance; England, Canada, Australia, and New Zealand can install this program and utilize the system on their own machines. It brings out a sort of Google Earth for worldwide data activity, a top-down view perspective of the planet’s internet connectivity.
Despite the fact that the NSA reports show that it might be utilizing the program to screen against enemies or computer attack or simply exploit planning offering a kind of front line map for digital battle. They likewise demonstrate that Treasure Map screens traffic and gadgets inside the United States. A few intelligence people told the Times that the project didn’t have the ability to screen all internet connected devices, and was centered on foreign networks and additionally the U.S. Defense Department’s own computer system. 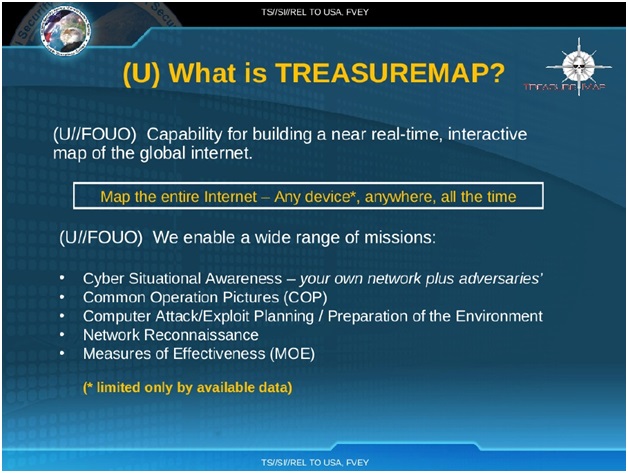
The Treasure Map design contained in the Snowden file don’t simply give itemized perspectives of worldwide networks but they also provide notes which carries and inside service providers networks Five Eyes agencies claim to have already penetrated. In graphics produced by the software, a portion of the autonomous systems; fundamentally, networks of routers all controlled by one company, known by the initials “AS” under Treasure Map’s watchful eye are checked in red. A NSA legend clarifies what that signifies: “Inside these AS, there are access points for specialized monitoring. In simpler words, they are under observation.
In one of the GCHQ documents, an AS belonging to Stellar PCS is checked in red, as are networks that are of two other German firms, Deutsche Telekom AG and Netcologne, which works with a fiber-optic network and provides cellular and web services to more than four hundred thousand clients. 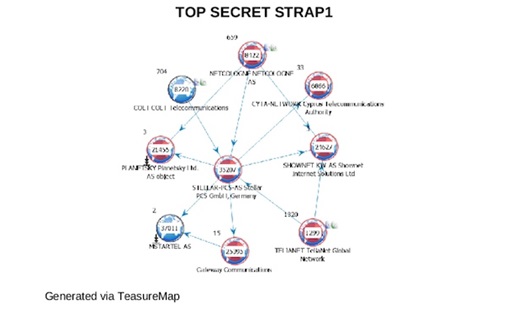
Deutsche Telekom, of which the German government possesses more than 30 percent, is one of the dozen or international telecommunications organizations that work worldwide networks alleged Tier 1 suppliers. In Germany alone, Deutsche Telekom provides cell phone services, internet and landlines to more than sixty million customers.
It’s not clear from the records how or where the NSA got access to the networks. Deutsche Telekom’s independent network, checked in red, incorporates several thousand routers around the world. It has operations in the U.S. also England, and is some piece of a consortium that works the TAT14 transatlantic cable framework, which extends from England to the east shoreline of the United States. Getting to of our system by foreign intelligence agencies would be completely unacceptable, said a Telekom.
Netcologne is a provincial supplier, with no worldwide operation, would appear to show that the NSA or one of its accomplices accessed the network from inside Germany. Provided that this is true, that would be an infringement of German law and conceivably an alternate NSA-related case for German prosecutors, who have been researching the observing of Chancellor Angela Merkel’s cell phone.
Journalist from a known organization reached both organizations a few weeks prior to provide for them a chance to research the claimed security ruptures that have happened to them. The security departments of both firms say they have launched intensive investigation, yet failed to discover any suspicious equipment or flow of information leaving the system. As far as NSA is concerned, they declined to remark on this story, and GCHQ offered no reaction past its standard case that all its exercises are legitimate.
Deutsche Telekom and Netcologne are not the first German organizations to be pinpointed by Snowden archives as having been effectively hacked by intelligence agencies. In March, Der Spiegel provided details regarding a large scale assault by GCHQ on German satellite administrators Stellar, Cetel, and IABG, all of which offer satellite web connections in remote areas of the world. Each of the three organizations works their self-ruling frameworks. What is more is that every one of the three is being stamped red in Treasure Map illustrations.
One record, from GCHQ’s Network Analysis Center, lays out of being an assault on Stellar. The report records central employees at the organization, and expresses that they ought to be distinguished and “tasked.” To task some person, in signals intelligence language; is to participate in electronic observation. Notwithstanding Stellar CEO Christian Steffen, nine different representatives are named in the document.
The electronic assault on Stellar has notable similarities with the GCHQ observation operation focusing on the Belgian supplier Belgacom as reported last year. There as well, the GCHQ Network Analysis office penetrating profoundly into the Belgacom system and that of its subsidiary BICS by hacking employee computers. They then arranged routers for cyber attack.
Journalists from Der Spiegel went to Stellar at its headquarters and gave the records to Steffen and three of his special workers. They were able to recognize, in among other things, listings of their central servers as well as the organization’s mail server, which the GCHQ attackers seem to have hacked.
The record likewise laid out the insights assembled from the spying efforts, including an internal table that showed which Stellar clients are, no doubt being watched by which particular satellite and identifying them by the satellites transponder. Those are business secrets and sensitive information said Stellar’s IT chief, Ali Fares, who is himself referred to in the documents as an employee of the organization who needs to be monitored. 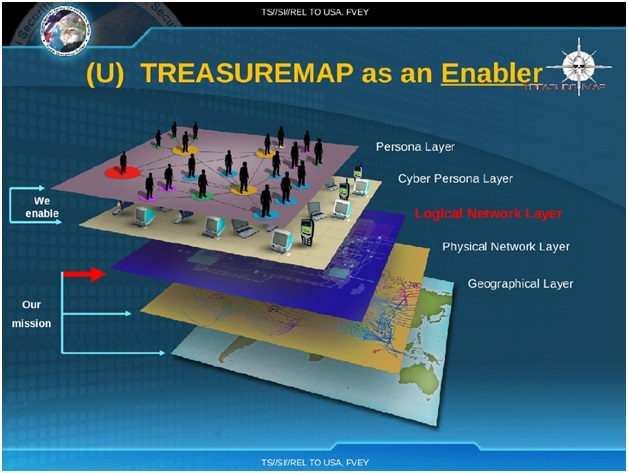
The Stellar officials showed alertness when they saw the passwords of the central server of a vital client. The significance of the robbery is huge and this is just disturbing, said Fares.
Steffen, in the wake of releasing his four-letter evaluation, said he considers the records to constitute proof that his organization’s system were hacked illicitly. He further said that the hacked server has dependably remained behind our organization firewall. The main method for getting to it is whether you first effectively break into our network. The organization being referred to is no more a client with Stellar.
At the point when inquired as to whether there are any reasons that would incite The United Kingdom, to take such a forceful methodology to Stellar. Steffen shrugged his shoulders and said that our customer traffic doesn’t run crosswise over conventional fiber optic cables. According to intelligence agencies, our company is clearly seen as hard target. Still, he said, that doesn’t show anybody the right to a break in and hack data. 
Furthermore, Deutsche Telekom’s security division has led a forensic survey of critical routers in Germany, however has not yet recognized anything. Volker Tschersich, who heads the security division, says it’s conceivable the red dots in Treasure Map might be clarified as access to the TAT14 cable, in which Telekom involves a frequency band in England and the U.S. At the end of last week, the organization informed Germany’s Federal Office for Information Security of the discoveries for Der Speigel’s reporting.
The secret documents also show that other information from Germany helps keeping the worldwide treasure map updated. Of the 13 servers the NSA works with; as far and wide as possible so as to track current data streams on the open Internet, one is spotted some place in Germany.
Like alternate servers, this one, which provides information into the secret NSA network, is camouflaged in a subtle data center.
____________________________________________________________
Sources:
https://firstlook.org/theintercept/2014/09/14/nsa-stellar/
http://www.ibtimes.co.uk/nsa-gchq-using-treasure-map-real-time-spy-worlds-internet-telecom-networks-1465495
http://www.spiegel.de/international/world/snowden-documents-indicate-nsa-has-breached-deutsche-telekom-a-991503.html
http://www.v3.co.uk/v3-uk/news/2367571/gchq-and-nsa-hacked-deutsche-telekom-to-create-internet-treasure-map
http://www.scribd.com/doc/239728882/NSA-GCHQ-TREASUREMAP-Docs





por que o interesse em pessoas simples,comum,o que fazem com essas informaçoes??