
More than two billion people are connected to the Internet in some way, and the more people are connected, the more elaborate plans to hack people are surfacing. There are many types of ways that a hacker can attack a normal person, and discussing them requires a completely new article. However, we have extracted one method, the oldest in the book – phishing, to discuss.
To be precise, phishing attacks are methods that hackers use to defraud people into giving their important information – and at times, also installing malicious software on their systems.
There are three types of common attacks, loosely described below:
1) Large Scale Phishing – An attack where hackers are just sending emails or similar forms of communications to a number of people.
2) Spear Phishing – This attack targets a special group of people or employees, using their personal information.
3) Whaling – As you can guess by the name, this tailored phishing attack is made for victimizing important people in a company, such as Presidents, CEO’s, CTO’s and people holding major information.
Furthermore, the above-mentioned attacks are there to give you a general idea of how hackers work. Now let us get specific about a few details in phishing attacks.
Email Phishing

This phishing method is commonly used by hackers or con artists who want your identity. They use methods such as spamming your email accounts with links to fake websites for Facebook, Twitter, or any other social media website. If they want specific information, they may even create a website with your bank’s login web page telling you that your account is under threat, pushing you to update your information.
How can you tell if the email you received, with emotionally charged information, is true? To begin with, you should look for the email address: where did it come from, does the email address end with the proper link, i.e. [email protected], or is it ending with something fishy like [email protected]?
Also, check if the body of the email contains messages specifically targeted to you. Sometimes, if a bank sends out a mass email, it won’t be highlighting your name, but rather, refer you as ‘Dear Customer’ to inform you about an event.
With a phishing email, they tend to personalize it specifically to you, usually be means of using a bot. Once you have checked for this tell-tale sign, you should then check if the email has grammar errors – big corporations will never send out emails without proof reading, while on the other hand, a hacker is likely to do just that.
With that said, most email services warn users about a malicious attachment in an email.
Also, worth noting is the need to check for fake links, i.e. the email contains a link to www.hsbc.com, but in essence, the hacker has changed its address in the code – leading to a different web site. You can check this by right-clicking on the link and then press ‘inspect element,’ which will show you an alternative link under the element <a href=”www.nothsbc.com”>www.hsbc.com</a>.
Vishing

The term Vishing translates to voice phishing, where hackers call you over the phone, pretending to be people from a bank or an important institution. From this, they can scoop important information out of you.
If that is the case, ask: did the hacker have all my information? Since we are currently posting our lives online every day, telling the world about our last wonderful meal or updating our pictures, tagging every place we visit; this gives hackers or a stalker easy access to their desired information. Hence, they collect this data without even hacking your social media account. Once all the information is gathered, then when speaking to you over the phone, the fake call seems more legit.
Once they have all the information on you, they will call you up and use it. Fear tactics are common, telling you that if you don’t pay them, they will call the police, or feed your mind with utter nonsense, telling you that your money is vulnerable. Automatically, you will panic, giving you less time to rationalize the information, thus naturally, giving in. In a very recent case, call center agents from India were calling U.S. citizens and posing as IRS agents, which made them millions of dollars.
So no matter what, always check the phone numbers and return call the original source. In the above case, calling IRS directly and asking them for you tax record would be the best approach.
Smishing

Smashing involves text messaging, where the hackers ask you for private information by making you believe that some major issue has hit you, or they have sent links in messages, which once you click them, will pave the way for a malware on your phone.
The most important thing to look for in such situations is the recipient number. Most times, the hackers will conceal the number using 3rd party software or online services that will send an email for them. In essence, if the number looks unfamiliar, don’t even bother opening it.
However, like email, messages can also have links to malicious websites that resemble the real thing. One example might be ww1.microsoft.com; these websites will only lead you to malicious programs, or cipher information from you.
It may be that a hacker might send you a message asking you to update your financial information, such as your complete name and address; it looks real – they might even add the last four digits of your credit or debit card in the message to give it a hint of genuine content. But even then, do not give in your information. In such cases, the bank, or any financial institution, should be contacted directly to verify if they sent the message.
Social Media Phishing
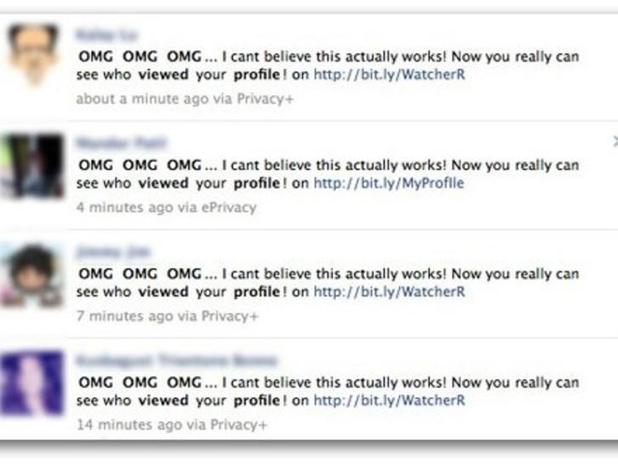
This phishing tactic is the hottest and the most popular, from script kitties to professional hackers, everyone uses this tactic. Using this method, the hacker uses popular websites such as Facebook, Twitter and other websites to get your information.
So how do you know if the account you are getting the link from, is not of a scanner? Firstly, you need to check the age of the account -when was the account created? Scammers tend to create multiple accounts and usually use alluring images to attract people.
In addition, they tend to create fake accounts replicating images of your friend(s), messaging the target with a link that tells them to click on the link as there is a prize waiting for them. However, the link automatically extracts personal information of the target, sending the information to the hacker’s server.
If the hacker, who is posing as your friend – isn’t going to message you directly with links, they might post malicious links on their wall, saying that this link will provide you with money or a free lottery. The link, however, will most likely open a scam website with a really cool interface, but after few seconds, a pop-up will open saying that your account is infected, prompting you to add personal information and ‘secure’ your account.
Conclusion
So by far, what have we learned first, is that hackers are very creative people when it comes to stealing information. In addition, it is extremely important to always be watchful and use your common sense. Always check the emails or messages from companies asking for your sensitive information. Never click on files or attachments from an email you don’t trust, or have never seen before. Also, if the email or messages asking you for personal information come from a financial institution – or any company, for that matter – that is housing your personal information, call them directly. Ask them if the email/message is theirs. Lastly, always contact them on their official number or official email address listed on their website.
Also, you can register your complaints with the FBI’s department of internet crimes by clicking here.
Source: Digital Guardian
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This article (How Hackers Phish and Ways For You to Find Them Out) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.




