
In May, several media sites published reports saying that a new kind of malware could be utilized to destroy victims computers. Although such reports may have provided effective ratings, it has been confirmed that the worry and doubt that they caused was actually unhelpful. Luckily, many security and hacking professionals, such as Graham Cluley, have been quick to correct the false perceptions these articles developed, enabling us to discover the menace, known as Rombertik.
The software company knows as Tripwire acknowledges Rombertik as a fascinating example of malware, mainly because of its anti research behavior. Let’s inspect the threat by exploring how it utilizes each of the four most frequent evasive methods applied by malware: external consciousness, confusing automated resources, time dependent evasion, and baffling inner data.
EXTERNAL CONSCIOUSNESS
First, the ambiguous action or external consciousness relates to the capability of a malware sample, including Rombertik, to evaluate the circumstances of the PC it is attempting to taint.
Furthermore, Talos Security Group (TSG) risk analysts Ben Baker and Alex Chiu, posted a report on Rombertik’s evasive behavior. Their particular findings concluded, among other factors, that the malware implements a line of inspections to identify whether it is operating around a sandbox. Upon execution, Rombertik initiates a round of checks before installing itself on a victim’s computer. It subsequently launches a second duplicate of the malware, which is overwritten by the malware’s primary operation. Before the malware activates, it perform an additional sequence of inspections to determine whether it is running in memory. If this last guard filters, the malware makes an attempt to overwrite the Master Boot Record (MBR) and reboots the machine, effectively making the computer useless.
Fundamentally, it is Rombertik’s ability to overwrite the Master Boot Record that fueled the speculative information contained within the articles in question. However, even then, generally there is a lot more to this protective measure than what meets the eye. In fact, a few days following the release of Cisco’s report, security firm Symantec published an article on their Security Response web page in which it explains how Rombertik is, in fact, the latest version of a black market crimeware kit known as Carbon Form-Grabber. In this particular summary, Rombertik’s ability to overwrite the Master Boot Record probably operates less as a counter-measure versus security professionals, and more as a discouraging factor to less experienced attackers who may be seeking to alter the malware’s code.
As an additional protection, Rombertik injects itself into its victims browsers to help conceal itself. As explained by Joe Giron, the malware therefore continuously goes through operating web browsers to hook a security specialist from Last Line Labs. In the event Rombertik does identify that the browser memory consists of a hook, this might be due to the work of the sandbox.
PERPLEXING AUTOMATED RESOURCES
This malware additionally makes use of perplexing automated resources so it can create a means to evade recognition. The malware then writes a byte of arbitrary data to store approximately nine hundred and sixty million times. This particular method obscures sandboxes. As they are not able to identify, regardless of whether it is stalling because the malware is not sleeping, many sandboxes ultimately time out their analysis before Rombertik commences to demonstrate any malicious behavior. In addition, these types of stalling loop floods and tracing tools with log entries, complicates the analysis process while malicious behavior is noticeable.
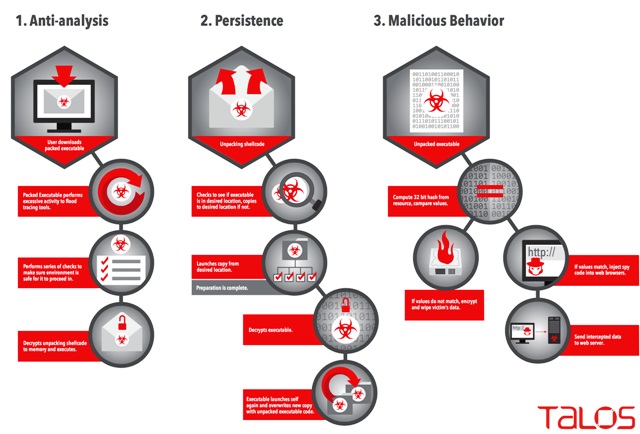
Rombertik’s runs on stalling code, which is a testament to how malicious strategies have evolved in tandem with the counter-measures utilized by security personnel. Few of the first elusive methods embraced by the malware was to code and encrypt. This tactic motivated AV companies to adopt robust analysis, which in turn brought rise to attackers designing malware with external awareness in mind. By the time security researchers responded with analyzing how malicious program code runs in virtual and real environments, an advancement which brings us our present phase in which malware creators incorporate waiting or stalling code as a method to close out this analysis. Clearly, Rombertik has gained the attention of malware intrigued communities because it makes use of this particular current development.
TIME DEPENDENT EVASION
Time Dependent Evasion is probably the least obvious strategy in Rombertik’s actions. According to Symantec, the malware produces the file “%SystemDrive%\Documents and Settings\All Users\Start Menu\Programs\Startup\[RANDOM CHARACTERS].vbs,” that makes sure that its code can run every time Windows boots up. However, not much else is known, as most explanations have targeted Rombertik’s remaining evasive characteristics.
BAFFLING INNER DATA
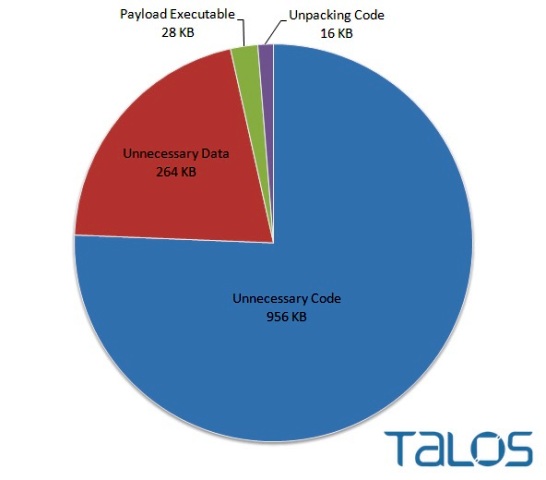
Pretty much the last evasive technique generally employed by the malware is confusing program resources. Here Rombertik creates use of garbage code to assist in concealing some of its most important functionalities. Believe me when I say, Baker and Chiu discovered that about ninety-seven percent of the packed file comprised of seventy-five images and roughly eight thousand functionality that are by no means used. This one approach allows the malware creators to conceal much of the primary Rombertik file, that is only twenty-eight kilobytes in size, thereby making it difficult for analysts and automated tools to analyze each and every function of this malware.
CONCLUSION
Provided its ability to overwrite the Master Boot Record subordinating specific conditions, its usage of both the garbage and stalling code, and its start-up every time Windows begins, leads us to believe that Rombertik is a master of evasion. Then again by no way does this imply that its hiding techniques are infallible. Researchers at Symantec discovered a spot of an RSA public key that allows researchers to prevent triggering Rombertik into cleaning the Master Boot Record. In addition, while examining the malware, Symantec’s sandbox went undetected by Rombertik. Such are both encouraging advancements. Malware may be changing with relation to its use of hidden behavior, but the security market is keeping pace. Every day, security experts devise new techniques to meet these emergent threats, and every day, online individuals experience the advantages by enjoying added protection and safety.
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (Suicide Virus – It Can Destroy Your PC) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





not good :{
I would think a simple antivirus program would protect against writing over the boot record. I mean, there is absolutely no reason a program would want to do that *except* destroy, so that attempt will probably be blocked (IF using antivirus). Also, the boot-record can be re-built. Ya, it’s a nasty computer crash, but no data or program loss. Just kinda like losing the index of a book, and having to recompile a new one from the book’s own contents.
No you are very wrong, depending on the type of malware there is a good chance it could be missed, it could sit and wait until next boot up, then inject itself while entering start up before the antivirus software even kicks in, where there is an open door there will be an exploit, never opening emails from unknown sources is also first port of call