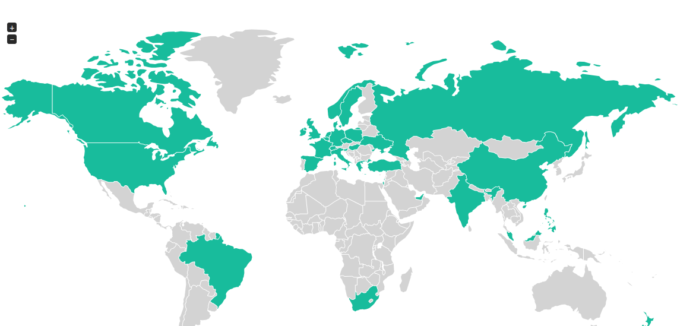
A new online map shows data of victims against attacks. This program is still new to the public and constantly updating for new lines of defense.
In a new technical age in which spies are able to carefully hide their tracks by utilizing multiple layers of obfuscation, as well as proxy servers, attempting to locate the perpetrators of online surveillance is rather an impossible task to accomplish. However, the victims of these ‘spying’ campaigns may occasionally become easier to place. With a single open-source initiative, it may allow us to map out cases in which state-sponsored malware campaigns have targeted society.
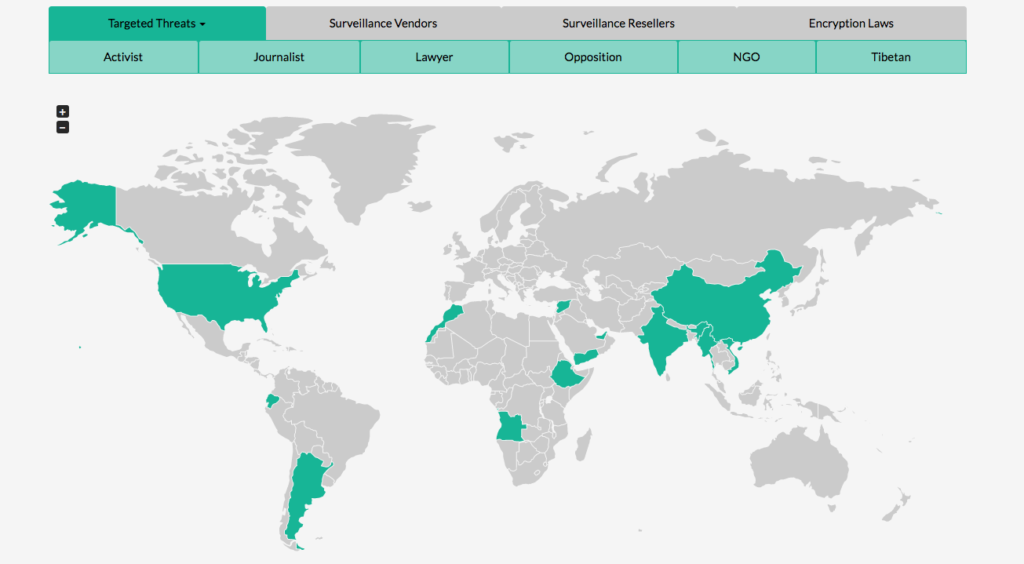
A new informal organization of top security researchers calling themselves “The Digital Freedom Alliance,” have launched a new collaborative online software project to better aggregate and map out government hackers, as well as the attacks against journalists, activists, lawyers, and includes international NGO’s. This project, in which code is uploaded onto the GitHub website, has the ability to collect information pertaining to state-sponsored malware infections from known public sources, such as the University of Toronto’s Citizen Lab, targetedthreats.net and top security firms. This program will then take the information and organize it into a large map, breaking down the attacks hosted by their date, target type, and the family of the malware that was used during the attack. This also hosts the location of the command, as well as the control server utilized in order to better coordinate each of the malware campaigns.
These new online maps were conceived last year. This project started while a Citizen Lab malware researcher, Claudio Guarnieri, had given a presentation during the Chaos Communications Camp Conference located in Zehdenick, Germany. His discussion touched on how security researchers work together and collaborate, while attempting to fight the governments’ digital oppression of known activists, as well as journalists.
During the conversation he states “We always lacked a starting point for people to get an understanding of what is going on…how countries are employing technologies to repress dissent,” he continues on with the conversation saying “Ideally, this would develop into a place where [we can] reconstruct narratives on what is happening in different regions of the world.”
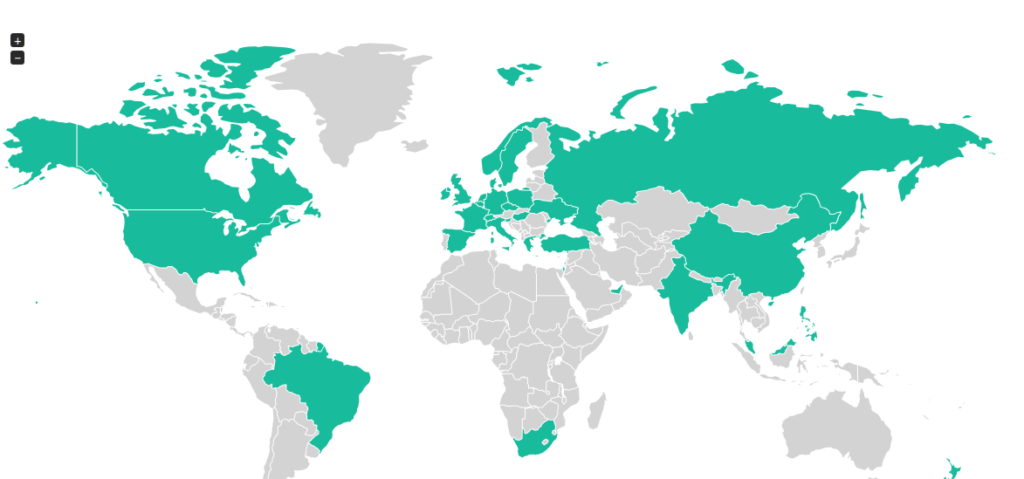
Surprisingly, the country in which held the most targeted attacks, is India. India has a total of 145 documented attacks. However, this is possibly due to the sheer volume of attacks carried out by the Chinese government. Guarnieri educates us about the Tibetan exiles and the separatist activists inside the Indian city of Dharamsala.
Second in line for the most targeted country based on the map, is Syria. This is where the brutal dictatorship of Bashar Al-Assad has proven to utilize malware to target opposition groups ever since the country started to devolve into a bloody civil war.
Adding onto the tracking of victims, the Digital Freedom Alliance’s map also provides the location of several companies that are selling and profiting off our surveillance technologies. With that collected data, Guarnieri stats that it is in fact sourced from the surveillance tracking projects, such as the BuggedPlanet.info and WikiLeaks Spy Files. With this collected data, it displays the country that holds the most surveillance vendors, which comes unsurprisingly, as the United States of America. However, Guarnieri has admitted that the lists of the definition of “Surveillance Vendor” is rather loose. This includes not just the original creators of the known malware documented inside the groups map, but also other potentially, and very nasty, technologies in a passive data collection of tools and other Internet filtering software.
At this point in time, the online map’s data is in no doubt incomplete. However, Guarnieri is hoping that other researchers will be able to contribute to the project. He is also hoping that this online map will be able to, someday soon, serve as a one-stop resource to track and fight back against government spying. He states “It provides relevant information to further investigate, identify victims, and perhaps rally campaigning if there are human rights abuses involved.”
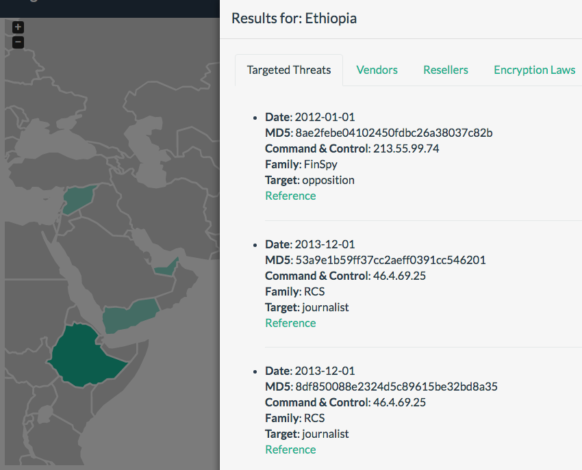
Guarnieri is also anticipating that the map project will one day serve as evidence in which Western surveillance technology firms’ do in fact, place us into the hands of the dictators that utilize its abilities. In a rebuttal against the claims of the large companies, such as the Italian Firm Hacking Team; Milan-based technology companies have denied their tools were used for wrongdoing. However, a hack of it’s email server has exposed that it did indeed sell their products to repressive countries, including Ethiopia, Egypt, Saudi Arabia and Sudan.
“I was tired of the Hacking Team-types claiming that there are no solid evidences of abuses, when there are plenty,” Guarnieri also says, “ You get most of them plotted in that map.”
Sources: Wired, DigitalFreedomAlliance, TargetedThreats, YouTube, BuggedPlanet, WikiLeaksSpyFiles.
This article (New Map Tracks Display Where Governments Have Hacked Activists and Reporters) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.




