
The new “iOS 9.3.5 Update” released by Apple, applies to those using iPhones, as well as iPads. This is in order to patch up not only 1, but 3 zero-day exploits/vulnerabilities. These vulnerabilities where found targeting the Apple users that target human rights activists, and was essentially found by a widely renowned UAE human rights defender, Ahmed Mansoor.
The NSO Group, which happens to be known as one of the world’s largest invasive software weapon distributors, is an Israeli-based hack group. They have been currently exploiting these three Zero-Day vulnerabilities, in order to carry out and perform spying techniques on dissidents and journalists, alike.
What’s more? The NSO Group is also known to sell spy and other related surveillance software, which allows the actions of digital spying to be conducted anonymously. Their software allows for the tracking of any targeted mobile phone.
One particular Zero-Day exploit had allowed the digital spy-ware company to develop a series of extremely sophisticated tools, whereby allowing a user to access their target’s device location, contacts, text-messages, call logs, email messages, and even their microphone.
Apple, the gracious company it is, has applied such a patch that applies to all 3 of these vulnerabilities with the iOS firmware. This was performed and carried out within a ten-day period of being informed of these exploits by two security firms. The firms who have brought these vulnerabilities to Apple’s attention are Citizen Lab, and Lookout Security, both of which have conducted an extensive joint operation of investigation upon the matter.
How Exactly did the Back-end Version of this Story Arise?
Mansoor, a Martin Ennals Award winner from the United Arab Emirates, had received a text message from an unrecognized number on his personal iPhone, on August 10.
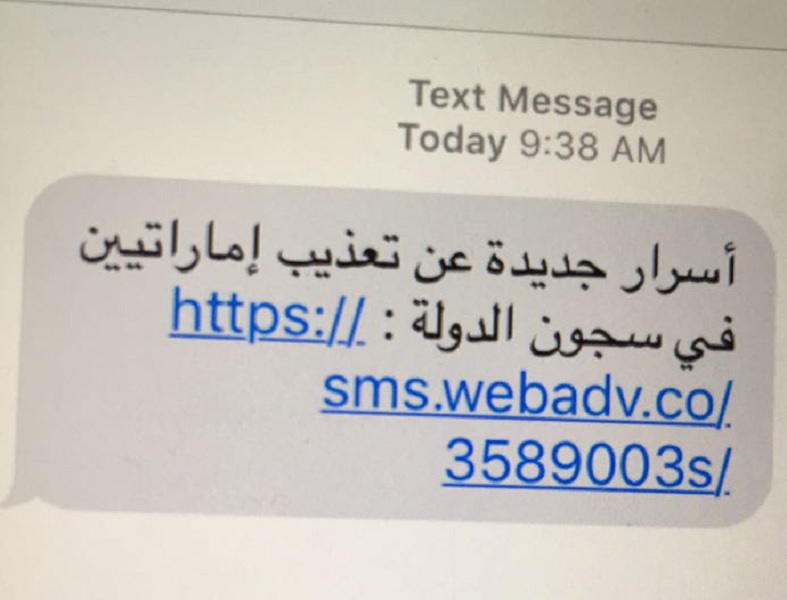
Naturally, Mansoor found this message to be suspicious, and aware that government hackers had already targeted his devices in the past, he proceeded to forward the message to Citizen Lab researcher, Bill Marczak. After some research, Citizen Lab then invited Lookout Security to join in with the examination of this strange message.
Finally, after a complete analysis of the message, the researchers concluded that within the compounds of the link, there was a lead to highly sophisticated malware, which fully exploited three major, yet completely different flaws within the framework of Apple’s iOS. This allowed the attackers to have complete control over the iPhone belonging to Mansoor.
The Trident Exploit Chain consists of the following:
1) CVE-2016-4657 – “WebKit in Apple iOS before 9.3.5 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site.”
2) CVE-2016-4655 – “The kernel in Apple iOS before 9.3.5 allows attackers to obtain sensitive information from memory via a crafted app.”
3) CVE-2016-4656 – “The kernel in Apple iOS before 9.3.5 allows attackers to execute arbitrary code in a privileged context or cause a denial of service (memory corruption) via a crafted app.”
If Mansoor had clicked on any of these links found within the compound of his strange text message, his phone would have transformed into an extremely sophisticated bugging device – taken over by the UAE security agency. Citizen Lab writes:
“They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it. They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts.”
As we can see from Lookout Security on their Blog Post regarding this matter, they published that the three Zero-Day flaws have been dubbed as the “Trident,” bestowed by the original firm. Involved in this manner, is:
- “A memory corruption vulnerability in WebKit that could allow hackers to exploit a device when a user clicks on a malicious link.”
- “Two kernel bugs (allowing device jailbreak) that an attacker secretly installs malware on victim’s device to carry out surveillance.”
Apple’s latest update, in which they have labeled as “Important,” is the new patch update 9.3.5. It was finally released on Thursday. This update also advises Apple users to install the latest update patch from iOS as soon as possible, in order to further protect their devices against these three Zero-Day exploits.
One can find the ability to install this new patch update using OTA (Over-the-Air) by your iPhone, or iPad, settings portal.
Sources: The Hacker News, Apple, Ahmed Mansoor, NSO Group, Citizen Lab, Lookout, CVE (WebKit), CVE (Kernel), CVE (Memory Corruption), Citizen Lab Blog Post, Lookout Blog Post.
This article (Apple Releases an ‘Emergency’ Patch after Vulnerability Targets Human Rights Activists) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.




