Written by: Tech Anonymous
One of the team members from a group calling themselves team “MaDLeets” has confirmed that yes, the group is responsible for the attack on www.pandi.or.id earlier this month according to a quote in techworm*
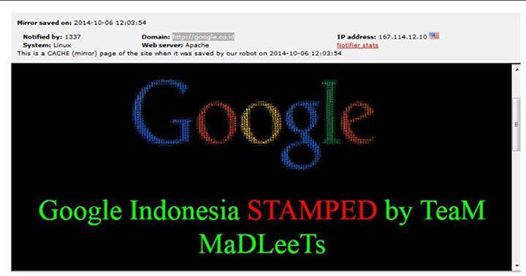
Although it appears that the “attack” was more of a defaming poke in the belly to the online giant, it still seems to be a major breech as far as the Indonesians are concerned. Apparently, when Google claimed to have upgraded it’s systems after last years breech of Google Malaysia (using the exact same method)… they may have been stretching the truth. Once again, it is believed these folks were able to wiggle their way in using a method called DNS poisoning. While so very many of you are thinking “wow, that’s cool” there are even more laymen (and women) out there thinking “WTH is that? Now I hafta worry about computer poisoning?” No, not like you’re thinking. Other than their pride and maybe a few servers suffering from the sniffles, we do not believe any computers were harmed or data stolen. Basically, the way this works is a hacker finds their way into the system, past security and into the Domain Name Server (DNS) and puts in data/commands that reroute traffic back out of the server and into a server that the hacker controls. In this case, back to a page that looked mysteriously like the Google Indonesia homepage with a slight alteration; a diagonal watermark from “MaDLeeTs”. Like a broken traffic signal in a strange town you’ve never been to. It’s taking you to the wrong place and you don’t even know it until you’ve arrived. There is no reliable information on how long the “defacing” was in effect but the group apparently took mercy on the general public after about 2 hours and added a usable search box to the false google page so that users themselves could still actually search information; an even BIGGER slap to Google : ) 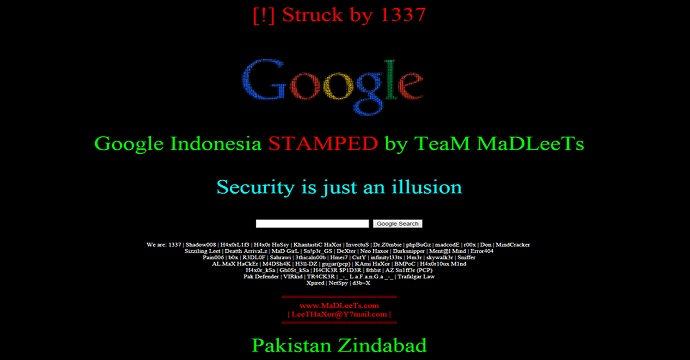
“who are these people?” one may ask. Well, there’s not a pile of information about them but this quote is taken directly from an official facebook page labeled MaDLeets;
“Verified: Official MaDLeets Fan Page! © www.MadLeets.COM
MadLeets is a Ethical and 1337 White Hat Hackers Community. We are Anti Hackers , we teach how to protect yourself from getting hacked.
MadLeets is a Ethical and 1337 White Hat Hackers Community.
We are Anti Hackers , we teach how to protect yourself from getting hacked.
we are not supported by any other organization.
Madleets.com is our Official Website / Community. we dont have any other Facebook Page.
we are 1337 , we are Ethical , we are White Hat’s & we are MaD All Time”**
Also appearing on this page is a checklist with a question;
Do you believe 1337 can haxor Google India & Israel ?
Google Indonesia ✓
Google Malaysia ✓
Google Serbia ✓
Google Burundi ✓
Google Kenya ✓
One might assume Google India and Israel may be their next targets. LoL. Through all this, the curious questions of “why Google” and “why” in general, continuously float about. A quote made after the Malaysia breech last year states:
“There’s not much reason behind it, only to prove that security is just an illusion. It does not exist.
We have no political intentions whatsoever, as you have already stated.
Regards, LeeT”***
Ok. It sounds well and good but we aren’t here to judge good and evil or light and dark. This group could be one of the “Cyber Robin Hoods” of our future. It could very well go the other direction. The Devil on one shoulder whispers “they’re just gonna do more damage as they learn more”. The angel on the other shoulder whispers “they’re just practicing while they learn and they’re going to do great things”. Time will reveal all. In the meantime, applause given in recognition of the intelligence to pull something like this off not just once but, so many times. At the same time, a display of sadness. This intelligence could be collectively directed to much higher and even more positive goals. What’s YOUR take on it all?
Links: Protect your PC and mobile devices from hackers & governments and surf anonymously
___________________________________________________________
*http://www.techworm.net/2014/10/google-indonesia-hacked-and-defaced.html
** https://www.facebook.com/Madleets
*** http://techcrunch.com/2013/10/10/google-malaysia-site-hacked-credit-claimed-by-team-madleets/