
Thursday July 3, 2014
Author: Wants to stay Anonymous
Purchasing malware to victimize people is illegal by law,but if the same thing is done by a
government official, then it’s not! Yes, police forces around the world are following in the steps of
the United States’ National Security Agency(NSA) and the FBI.
Researchers from the Citizen Lab at the Munk School of Global affairs at the University of
Toronto and computer security firm Kaspersky Lab have unearthed a broad network of
controversial spyware,specially designed to give law enforcement agencies complete access to
a suspect’s phone for the purpose of surveillance.
The malware, dubbed as Remote Control System(RCS), also known as DaVinci and Galileo,
was developed by an Italian company known as the Hacking Team,and is available for desktop
computers, laptops and mobile phones. The latest version of the malware works on all versions
of all major mobile operating systems, like Android, Blackberry OS, iOS, Windows Phone and
Symbian, but is best suited for Android and can also be installed on jailbroken iOS devices.
The team of researchers from both Citizen Labs and Kaspersky Labs in collaboration have
presented their findings during an event in London. According to the report published, the
diameter of the infrastructure supporting Hacking Team(which sells the RCS to governments
and law enforcement teams) is very vast with 326 commandandcontrol(C&C) servers
running in more than 40 countries.
MALWARE DEVELOPERS HACKING TEAM
Hacking Team is a Milanbased IT company with more than 50 employees that has made a
totally different place for itself,selling “offensive” intrusion and surveillance software to
governments and law enforcement agencies, in “several dozen countries” over “six continents”.
“It was a wellknown fact for quite some time that the Hacking Team products included malware
for mobile phones. However, these were rarely seen,” said Kaspersky Lab experts in the blog
post. “In particular, the Android and iOS Trojans have never been identified before and represent
one of the remaining blank spots in the story.”
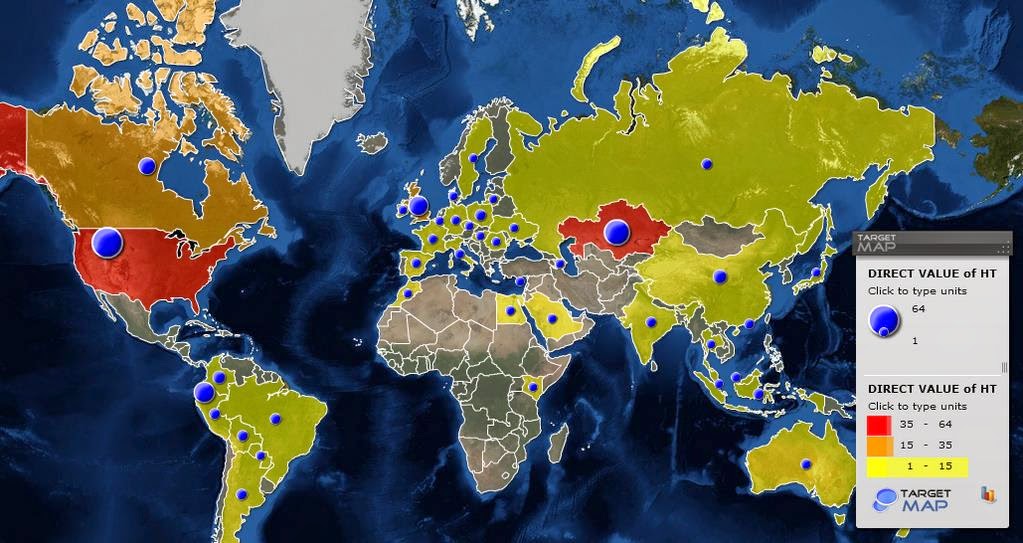
Kaspersky Labs have used a fingerprinting method to scan the entire IPv4 space and to identify
the IP addresses of the RCS C&C servers around the world and found the biggest host in the
United States with 64 counts of C&C servers. Next on the list was Kazakhstan with 49, Ecuador
with with 35, the United Kingdom with 32 servers and a host of other countries, all totalling to 326
C&C servers.
“The presence of these servers in a given country doesn’t mean to say they are used by
that particular country’s law enforcement agencies,” said Sergey Golovanov, principal
security researcher at Kaspersky Lab. “However, it makes sense for the users of RCS to
deploy C&Cs in locations they control – where there are minimal risks of crossborder
legal issues or server seizures.
ATTACK VECTORS AND MALWARE FEATURES
RCS can be physically implanted on the victim’s device via a USBflash drive or SD card, and it
can also be remotely installed through spearphishing, exploit kits, driveby downloads or
network traffic injection.
Once installed on iOS or Android devices, the new module enables governments or law
enforcement agencies to monitor the victim’s device, including the ability to
● control the phone network
● steal data from the device
● record voice email
● intercept SMS and MMS messages
● obtain call history
● report on the device’s location
● use the device’s microphone in real time
● intercept voice and SMS messages sent via applications such as Skype, WhatsApp,
Viber, and much more.
“Secretly activating the microphone and taking regular camera shots provides constant
surveillance of the target—which is much more powerful than traditional cloak and
dagger operations,” Golovanov wrote.
While the Android module is protected by an optimizer for Android called DexGuard, most of the
iOS capabilities mentioned above are also available for Android, along with support for hijacking
applications like Facebook, Google Talk, China’s Tencent and many more.
The mobile modules for each are custombuilt for each target, researchers said. from previous
disclosures, we’ve seen that RCS is currently being used to spy on political dissidents,
journalists, human rights advocates and opposing political figures.




I believe that if America truly stands for freedom of speech (first amendment) and true freedom then it needs to stop things like this. If I got hold of it and somehow got it into an officials phone, from any country, I could potentially derail that person’s life for lulz. Thats trolling material for you.
no its the new world order now they took our freedom and gave us shit its time for us to rise and show the government the true meaning of freedom rise brothers and sister fight for what is right destroy them all and kill Gods enemies vanquish the evil of the world u say u believe in God prove it and fight for your God its time to show them FREEDOM !!!!! for our families they never care about us join us spread the word world power is going down
This explains everything that is happening to my phone. privacy? Far from! Rights? I have none! Its fuckd. up and not right! I’m not an experiment! Never said I want to b used! Ur wrong for doing this in more then one way! No wonder Verizon has nothing to say to me!
I thought this was a free country
apparently I guess not