In today’s world, almost everything in our homes has become a smart device. We are updating the technology within these products, making them function as small personal computers that learn our routines and discover custom online material to accommodate our needs.
This year, more than 3.56 million unique items will be made available to people, as reported by marketing research and technology firm Gartner. However, when looking at these new devices from a security point of view, we may be dealing with millions of electronic keys to people’s lives, credit cards, passwords and everything they have kept hidden – or, at least, tried to. Every unprotected Internet of Things (IoT) unit will function as an access point for your residence and online assets. Trespassers will be able to apply the IoT to unlock the front entrance of your home. Although the pattern expands nonstop, more buyers are beginning to fret about the safety of their homes and personal information.
Where Are The Vulnerabilities?
The majority of units are operated using a mobile phone software. In order for the IoT to work, the device must be linked to the owner’s WiFi. In the event a cyber criminal finds a method to penetrate it, they can bring chaos. Entering a linked unit does not supply the hacker with a great deal straight away, however, this system may cause a total compromise of the managing smart device, and more serious, the person’s local network. Hubs, house conditioning devices, smart televisions, and other appliances depend on online systems and mobile programs.
Cloud technology is accompanied by its issues: loss of power over information, listening without permission, information exchanges from users to cloud machines, legal and agreement problems, and such like. Cellular devices independently encounter bad protection tactics – for instance, no mobile protection setup, poor technical settings and destructive application files.
However, below we have listed a few of the most widespread weak spots to consider when buying a new Internet of Thing product:
Default Settings
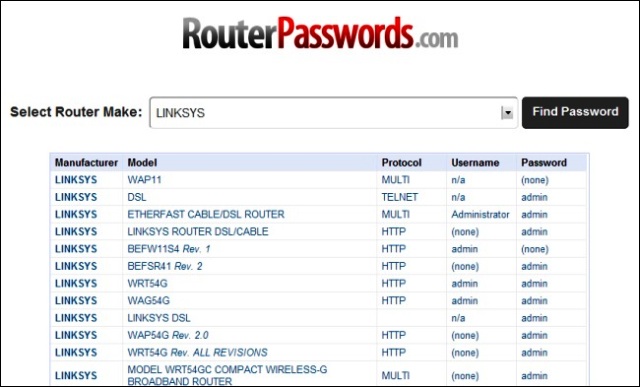
Credentials are crucial in data protection. Nevertheless, the Internet of Things evolves the manner in which we authenticate. In some instances, the devices incorporate biometrics and, at times, don’t even prompt consumers to verify. If smart devices are swiftly forced to market without sturdy verification components, they could be at risk from brute-force assaults. For example, a number of leaked documents and hacks show numerous smart equipment having default account details like ‘admin’, ‘12345’ or in some cases they don’t need account details at all. On a similar observation, many smart online or cloud interfaces do not maintain two-factor verification.
Overall Security
Transferring information in plain text from a gadget’s receptors up to the cloud is not an effective safety application; however, it has been discovered that a few IoT applications can be affected by defective SSL implementations, revealing sign in details, codes, along with other fragile information. Devices such as your smart thermoregulator and television requests your wireless passphrase, and commonly stores it in plain text in the smart device’s memory. A lot of units may also be unsophisticated enough to hook up to virtually any system that features the unchanged title.
Rare Revisions
The Internet of Things and its devices require forced automated application upgrades. Updates play a variety of duties, such as patching safety gaps which can be abused by online criminals. A high-end network router, from a trusted make, possessed a year old firmware weakness, which allowed a crook to take complete control over the product. Disturbingly, the standard application did not mention firmware versions or updates. Ultimately, this brings us to the question: how many of us check for the updates ourselves?
Not-So-Secure Online Interface
A number of the online user interfaces will not lock people from their accounts following numerous unsuccessful login attempts. They neglect to make sure sturdy passphrase components are in place; supply zero security over cross-site scripting problems, as well as SQL injections. Hackers only need to fool the individual behind the WiFi and security system to push a hyperlink. In the event that the online ‘web-face’ is prone, it should present the hacker with a chance to access the online administration screen.
Defective Software
A flawless and perfect code is only a fantasy. People desire effective applications, and they require it immediately. This might lead to defectively built applications that are circulated early with little to no attention to safety. Ultimately, this could lead to incomplete revisions or backdoors, which could potentially be abused by online criminals. In addition, a great number of Android structured smart televisions permit the setup of 3rd party applications. A harmful backlink delivered through Skype, can very quickly deceive the consumer and prompt them to set up a backdoor. Many products may also execute unrequested firmware updates — these may download spyware rather than your much-enhanced firmware.
Equipment Disappointments
Obsessed with producing a dazzling piece of artwork, many producers ignore their product’s component bug(s). This may enable hackers to hard-reboot the equipment and their proportionate hot spots. Attackers will get in the center and trick the cellular application seeking to create a link. If the link works, the hacker can obtain the login name and code of the person’s router. The majority of IoT weaknesses are not new to the online-security business. Up until now, we have observed studies and evidence of notion, then again it is merely a question of time until hackers begin exploiting bitcoins and other hidden currencies via linked fridges, or until smart televisions are barred by a ransom-ware. As a result, in the years ahead, safety has got to be the focus of any IoT system.
Source: Tech Worm
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (Is Your Smart Home Safe?) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





My home is not very smart so no problem there but I try to keep my cloud or One as it is called on my new computer cleared of everything on a weekly basis. Is this a smart thing to do? Some have said that is your back-up system for your computer but it also uses up a lot of my memory space and sometimes they say I need to buy more One space.