
Whether you know it or not, whether you believe it or not, you are being watched constantly by Big Brother — overly intrusive democratic governments; controlling authoritative regimes; and intelligence agencies that act more like government spies. So how do you protect yourself online and ensure you remain secure offline? There are many ways to protect yourself from the prowling eyes of Big Brother, become near invisible, and avoid being tracked…
Mislead, Misinform, Misdirect
Should you quit social media completely, since data harvesting occurs on all major social media sites? Absolutely not. Trying to go untraceable to reduce the risk of being tracked online is futile, to say the least. If there are no traces of you online, you will stick out like a sore thumb. For you, no news of you on the Internet may be good news, but Big Brother will ensure that no news of you on the Internet is bad news for you. The moment you decide to self-impose a social-media detox, you will draw curiosity as to who you are and what you are up to during your day-to-day life. That’s even worse.
To turn the table on Big Brother, engineer the parts of “you” that are traceable, a kind of misdirection. Keep your social media profile and go astray: share, like, post content that leads prying eyes to construct an inaccurate psychological profile of you; basically keep the Big Brother focused on the left hand while you move with the right hand. You can also create a fake profile or multiple new profiles to confuse them further.
Change Your Buying Habits
When you shop online using your credit card, you unintentionally guide the interested parties through the process of your patterns of activity and character based on the items you buy, when you buy them, and where you buy them. Do you notice how Facebook shows you ads for something you search on Google, even when you are not logged into Facebook?
If Facebook can have access to your search on Google and other websites, how do you ensure secrecy while making an online purchase – when you know Big Brother is watching you, as well? Stick to currencies like Bitcoin or cash on delivery to purchase what you need; buy different items; buy from different websites; go international; in short, break your pattern. You can also consider options to barter and exchange services, instead of relying on any currency at all.
Invest In An Anti-Surveillance Smartphone Case
How do high-level government agencies hide their activities? By surrounding their buildings with copper shielding. Why copper? Because copper is a highly conductive metal that allows the user to escape surveillance by blocking electromagnetic fields (EMFs allow others to pry into your information and watch your activity). Your Smartphone also uses electromagnetic fields, so if you want to move without worrying about who’s keeping tabs on you, you must buy anti-surveillance or Faraday enclosure for your Smartphone.
Spy-proof Smartphone cases, such as Tunnel, allow you to hide your location and data, as well as warn you if you’re being monitored. Whistleblower Edward Snowden plans to develop a modified iPhone 6 case-like device, dubbed an “introspection engine” by its designers, that aims to notify users whenever their phone is transmitting data, as well as obstruct phone cameras to prevent unwanted monitoring. IBTimes writes:
The device includes a small, built-in monochromatic screen that can monitor when an iPhone is transmitting, cover the rear-camera and even juice up the iPhone with extra battery power. Connecting to a phone’s internal antennas for cellular connection, GPS, Bluetooth, and Wi-Fi through the SIM card slot, the device can monitor and trigger an alert if a phone is errantly transmitting data via radio signals that can potentially put a user at risk of detection. They say it can also immediately shut the phone off altogether.
Encryption, Encryption, Encryption
Yes, encryption. Encryption works, stresses Snowden. “Properly implemented strong crypto systems are one of the few things that you can rely on. Unfortunately, endpoint security is so terrifically weak that NSA can frequently find ways around it.”
How does it work? Consider this: when you use your credit card to shop online, your computer encrypts that information so that others don’t steal your personal data while being transferred to a third party to carry out a financial transaction. Similarly: you can protect your identity, as well as your data, from people you don’t want to see it. This is done by encrypting your hard drive and your sensitive files to encrypting your emails and your computer’s Windows. In order to keep the content of your files a secret, your cloud storage safe, important emails secure, or hide your entire operating system, you can encrypt everything so that no one can breach your privacy without your approval or your password.
This article (How To Hide Yourself From the Government’s Prying Eyes) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





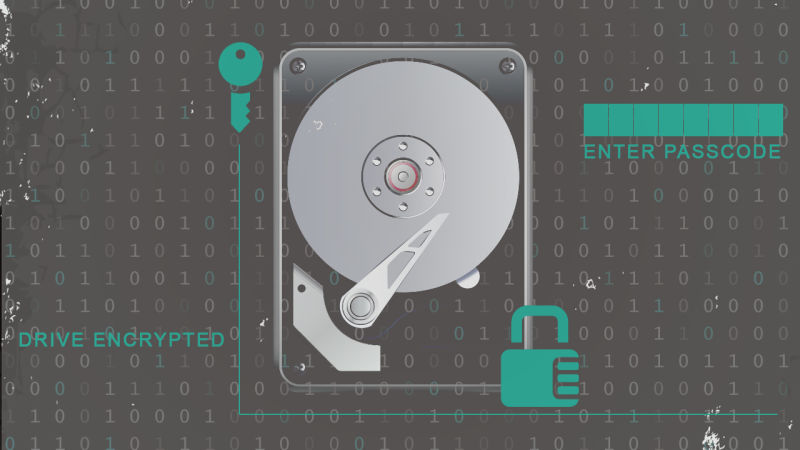



Many varients of Linux can setup LUKS encrypted drives as part of the installation. Everything, include the OS, is strongly encrypted. https://guardianproject.info/code/luks/