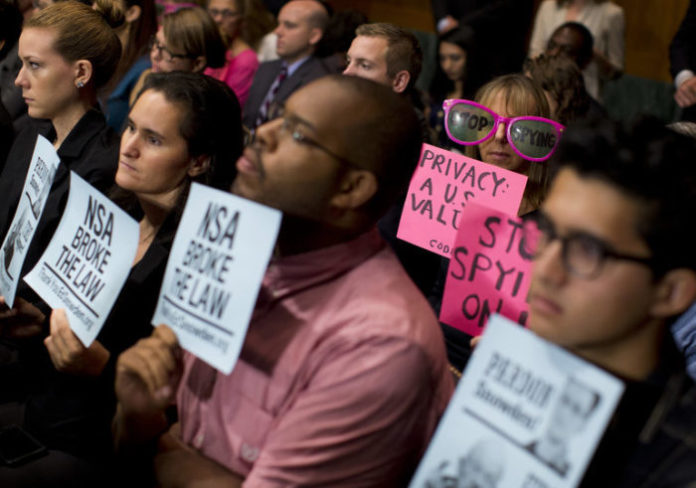
If you were out of town the other day, we’re here reminding you that WikiLeaks has done it again. Julian Assange, living in his small room inside the Ecuadorian Embassy in London, has exposed the United States Central Intelligence Agency (CIA) big time. After tweeting a series of cryptic messages about Vault 7 in February, WikiLeaks has now published what it claims to be the largest ever release of confidential documents on the CIA.
According to WikiLeaks, the damning documents titled “Year Zero” is just part one of the Vault 7 series it intends to roll out in the days ahead. The leaked documents – 8,761 of them – were reportedly leaked from an isolated, high-security network situated inside the CIA’s Center for Cyber Intelligence in Langley, Virginia.
RELEASE: Vault 7 Part 1 “Year Zero”: Inside the CIA’s global hacking force https://t.co/h5wzfrReyy pic.twitter.com/N2lxyHH9jp
— WikiLeaks (@wikileaks) March 7, 2017
The files show how the CIA has used covert hacking tools embedded in iPhones, Android, Microsoft and Smart TVs to invade our privacy. This has sparked outrage among human rights campaigners and privacy activists.
According to activists, the United States government, through its numerous intelligence agencies (both overt and covert), has become a brutal dictator, blatantly disregarding the citizens’ rights to their privacy. Since the CIA was the central figure in the latest leak by WikiLeaks, activists directed their anger towards the agency. Activists said the leak is a big dent on the already tarnished image of the CIA, and the United States government.
CIA’s secret hacking division produced a huge amount of weaponized malware to infest iPhone. Android phones–and lost control of it. #Vault7 pic.twitter.com/KmFLEVmbnE
— WikiLeaks (@wikileaks) March 7, 2017
The Australian journalist and activist using the pseudonym Anonwatcher wrote: “The electronic gadgets we own are the CIA’s gateway to our privacy, more than we’ve ever thought or cared to contemplate. Nothing is safe.” Anonwatcher’s statement was backed by other human rights groups campaigning for total freedom on the internet. According to these campaigners, the files published by WikiLeaks confirm the long-time suspicion that the United States government has used the CIA and other intelligence agencies to perpetuate the spy business around the world via the internet.
CIA steals other groups virus and malware facilitating false flag attacks #Vault7 https://t.co/K7wFTdlC82 pic.twitter.com/Z0nat1Lqsv
— WikiLeaks (@wikileaks) March 7, 2017
“Hacking is one of the most invasive activities governments can engage in, yet it occurs in the dark, without public debate. It’s not just the CIA, but law enforcement agencies in the United States and around the world that conduct hacking operations with significant repercussions for human rights and digital security. This leak demonstrates the urgent need to have a serious discussion about government hacking and to implement a legal framework,” said Nathan White, Senior Legislative Manager at Access Now, a Washington D.C.-based international NGO that focuses on the intersection of human rights and technology.
Access Now said the files leaked highlight the inherent risks involved in government hacking operations. The organization utterly condemned the United States government for engaging in such a flagrant abuse of power. It also called for full protection of human rights and immediate reforms to the Vulnerabilities Equities Process.
WikiLeaks’ #Vault7 reveals gaping holes in all popular operating systems + anti-viruses programs https://t.co/K7wFTdlC82 pic.twitter.com/QHs8JYF0FR
— WikiLeaks (@wikileaks) March 7, 2017
“Today, our digital security has been compromised because the CIA has been stockpiling vulnerabilities rather than working with companies to patch them. The United States is supposed to have a process that helps secure our digital devices and services — the ‘Vulnerabilities Equities Process.’ Many of these vulnerabilities could have been responsibly disclosed and patched. This leak proves the inherent digital risk of stockpiling vulnerabilities rather than fixing them,” White said further.
Jointly developed CIA+MI5 malware infests Samsung smart TVs to turn them into covert microphones #Vault7 pic.twitter.com/Ki0wRlgjPP
— WikiLeaks (@wikileaks) March 7, 2017
The CIA has refused to comment on the latest leak. We understand the CIA, instead of bowing in shame and putting a stop to this criminal activity, is rather, focusing on hunting down whoever leaked the files to WikiLeaks, seeking their retribution.
Chelsea Manning and Edward Snowden warned us. But it seems both Manning’s and Snowden’s disclosures never deterred the United States government away from the spy business. Of course, we’re well aware of the United States continuing to spy – as that has been the current norm for all countries vying for influence in the international arena.
CIA illicitly hoarded ‘zero day’ attacks, putting at risk industry, government and even Trump’s Twitter account https://t.co/K7wFTdlC82 pic.twitter.com/miJOPvl7MD
— WikiLeaks (@wikileaks) March 7, 2017
However, the scope and the rate at which the United Sates government is spying on us is unacceptable. From the leaked documents, the CIA was planning to embed secret recording devices in computerized or smart cars in order to tap into conversations of targeted people. This speaks volumes of the issue we are dealing with. It calls for huge concern among all of us.
Nothing is indeed safe and we’re all at risk. We must unite and fight this, rather than surrender our privacy to our governments in this digital era, shrugging our shoulders. All available legal measures should be used to prevent our government(s) from watching and hearing us, and invading our privacy. The time to take action is now, starting with street protests to let our voices be heard.
This article (WikiLeaks’ Vault 7 Release Sparks Outrage Among Human Rights Campaigners, U.S. Government Condemned and Shamed) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.
Supporting Anonymous’ Independent & Investigative News is important to us. Please, follow us on Twitter: Follow @AnonymousNewsHQ