
The world went into shock after the informer named Edward Snowden, made the National Security Agency’s information collecting methods completely open. Among the successful techniques deployed by the National Security Agency, sits a rather simple but efficient tool known as Quantum Inserts. Apparently, this special tool is helpful whenever phishing techniques are not particularly useful. Since it works by corrupting the internet browser even though it is opening a page, it forces the user to access to an additional web page that leads the user to download terrible spyware. To detect tricky National Security Agency’s Quantum Insert hits, you must first understand how the method works.
When this came to light, many known #infosec bloggers, various tech websites and many reputable newspapers published one thing or the other about the dirty tricks and methods that the NSA had been using. Both the National Security Agency and their British counterpart the Government Communications Headquarters (GCHQ), demands rapid functioning servers that tend to be positioned nearby the targets machine. From there, they are able to intercept the browser’s order or a request before it accesses the requested web page. This then diverts the user, causing them to enter a different web page that contains harmful malware.
A video by #TheIntercept showing one of many methods on how the #NSA #hacks.https://t.co/vx00GCAZkr
— Anon.Dos (@anondos_) September 19, 2015
In order for these malware spitting machines to accomplish this process, the servers can be set tactically throughout the internet. The servers that are programmed to perform this task are also known as shooters. These machines cover massive segments or definite places over the internet.
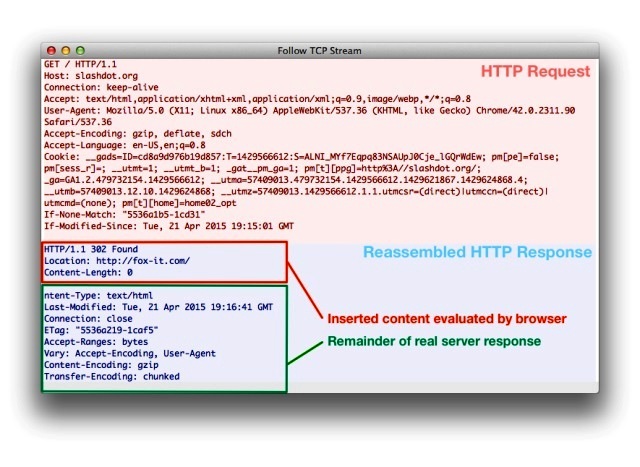
A Normal Way of Going to a Web Page:–
The internet browser sends GET (Requests data from a specified resource) request to the server using the following information.
– Source and Destination Internet Protocol information of the browser.
– Acknowledge & Sequence Numbers.
Then the server reacts with the same Acknowledgement numbers. In addition, the server also includes constant figures to the Transmission Control Protocol packets.
Using these Transmission Control Protocol packets in a sequential arrangement, the internet browser constructs the web page.
When There is a Quantum Insert Attack:-
The Quantum Inserts are “fired” by the shooter servers to show up prior to the authentic GET request.
The Quantum Insert then reproduces the unchanging strings of the Transmission Control Protocol packets, but using a different payload.
The browser reads the fake Transmission Control Protocol packets.
The false Transmission Control Protocol packets construct the duplicate web page.
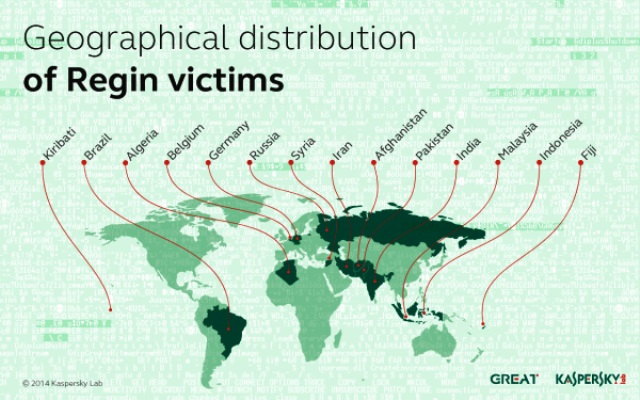
This technique was originally utilized by GCHQ, using Regin malware in the giant Belgian telecommunications company called Proximus Group. The technique identified profiles of employees operating for the Proximus Group and generated identical copies of the personal’s profiles—similar to the ones on Linkedin. As a result, when the account of the employee was visited, the rapid operating servers (also known as shooters) shot the same signal prior to the genuine signal, causing the user to receive the infectious downloading page.
This method, highly relies on the battle around the actual browser’s connection speed or the GET request, plus the time period it takes the malicious servers to position the fake request before the real GET request, hence the positioning of malicious servers at ideal points of the internet. Because of the confined insights about Quantum Insert attacks, the methods of discovering it aren’t completely developed. The researchers at Fox-IT have cloned the hack on the company’s own computers, in order to analyze the packets and devise a detection method.
PAYLOAD DEVIATION
Examining the first Transmission Control Protocol packets payload data is the initial stage in which you may detect a Quantum Insert. However, as the starting Transmission Control Protocol packet may be the real one, the Quantum Insert may place the fake Transmission Control Protocol at any time during the protocol session. Ultimately, this could cause the technique to be unsuccessful.
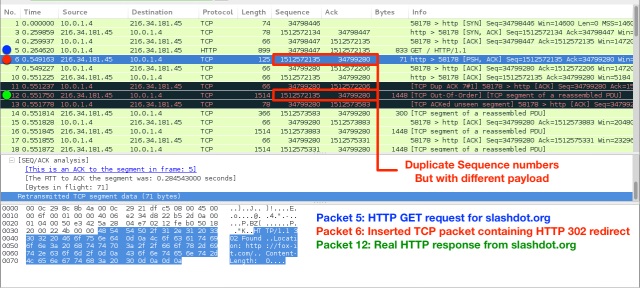
THE HOP LIMIT ODDITY
The Hop Limit, or the Time To Live values, is a process that controls the lifespan of data in a computer or over the internet. However, the Hop Limit value may also differ around packets due to the Quantum Inserts, the packet is likely to have a longer Hop Limit or Time to Live limit since it could be used later than the actual packet.
ATTACK DETECTION SYSTEMS
Even though there is not sufficient data to correctly deal with discovering a Quantum Insert strike, experts at Fox-IT believe in using the method of Intrusion Detection Systems to detect a Quantum Insert hack. More facts on the special packets are available on the GITHUB page.

Avoiding the hacks requires basic knowledge in online monitoring and staying anonymous over the web. Quantum Insert hacks can be prevented by understanding the following methods:-
1) Encrypting Information
2) Awareness of Popular Web Services
3) Virtual Proxy Networks
4) The Onion Router browser or the Dark Web
5) Anti-Malware
6) Dis-Arming Web Tracking
The more knowledge you have – the better you can protect yourself.
Source: WIRED, FossByte, Fox-IT
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (Detect Those Nasty NSA Quantum Insert Attacks) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.





Is it possible for someone to write some sort of addon or program that can detect this sort of thing?
Your name say it all
lol