
American will never be destroyed from the outside.
If we falter and lose our freedoms,
it will be because we destroyed ourselves. – Abraham Lincoln
About two years after Ed Snowden released intelligence data concerning the National Security Agency’s local observation, Americans give off an impression of being unwilling, incapable, or basically excessively aloof, making it impossible to make moves to ensure their own security in the world of electronics. Informants like Snowden and the columnists who encourage their approaching hazard antagonistic recoil, with some being “marked” under the undefined Espionage Act. Their crucial part in holding an intel and intrusive government accountable for its invasions into the general population’s personal lives is undeniable, yet response to this stays tepid. Is it true that we are to be sure ready? If we falter and lose our freedoms, it will be because we destroyed ourselves. Despite famously uncertain ‘terrorism’; or, maybe surprisingly more dreadful, have we basically started to anticipate such interruptions?
Image Source: Google Image – Journalist Glenn Greenwald and the Guardian won a Pulitzer Prize for reporting based on Snowden’s information
It was the 5th of June and that is when it all started, the Guardian published “NSA Collecting Phone Records of Millions of Verizon Customers Daily”, columnist Glenn Greenwald and the Guardian never specified that they had a fortune trove of other NSA records, or that they originated from one individual. At that point after three days, the source voluntarily came forward and the world now knows him as Edward Snowden.
The Secret Court That Allowed NSA to Poke Their Big Nose
The first story uncovered that Verizon had been giving the NSA basically every last bit of its clients’ telephone records. It soon was uncovered that it was not just Verizon, but basically every other phone organization in America. This disclosure is still a standout amongst the most disputable ones. Ethical hackers have tested the lawfulness of the system in court, and one Judge esteemed the project illegal and almost Orwellian, while another ruled it legitimate.
The turmoil created by this first story has driven President Barack Obama to underwrite a change to the project, and the House of Representatives to pass the first law that tries to change it.
The presence of PRISM was the second NSA stunner, nearing under 24 hours after the first. At first, reports depicted PRISM as the NSA’s project to straightforwardly get to the servers of U.S tech monsters like Google, Facebook, Microsoft and Apple, among others. It is the truth was marginally distinctive.
The Friendly Social Media Watch
In less than 24 hours after the first article was published – the announcement of PRISM was the second bombshell that was dropped on NSA. Files and publications described PRISM as NSA’s program that had direct access to Google, Twitter, Facebook, AOL, Microsoft, Apple you name it. But it was a bit over kill. The reality was a bit different.
The program was less “underhanded” than initially suspected. Truly, the NSA does not have direct access to the servers, however can ask for client information from the organizations, which are propelled by law to consent. It was maybe as questionable as the first NSA scoop, inciting innovation organizations to first prevent any information from securing it, then later battle for the privilege to be more straightforward about government information demands. The organization’s wound up part of the way winning that battle, getting the administration to facilitate a few confinements and consider more straightforwardness.
Our British Cousins the GCHQ & its Global Fiber Optic Cables Network
The British intelligence office, the Government Communications Headquarters (GCHQ), taps fiber optic links everywhere throughout the world to catch information moving through the worldwide Internet. The GCHQ lives up to expectations nearly with the NSA, sharing information and knowledge in a program that is codenamed Tempora.
Tempora is one of the key NSA/GCHQ projects, permitting the spy offices to gather unfathomable troves of information, however for reasons unknown, it has at times been neglected. After a few months of Tempora’s disclosure, a German daily paper uncovered the names of the organizations that work together with the GCHQ in the Tempora program: Verizon Business, British Telecommunications, Vodafone Cable, Global Crossing, Level 3, Viatel and Interoute.
Don’t Feel Bad We Spy on Our Leaders Too
Image Source: Google Image – President of the United States Barack Obama, right, and German Chancellor Angela Merkel are seated together at a G7 dinner in Brussels, on June 4. Their relationship has been tense since reports revealed that the NSA tapped Merkel’s phone
Over the months, endless stories in light of Snowden archives have uncovered that the NSA has kept an eye on various world leaders and foreign governments.
The German news weekly Der Spiegel uncovered that the NSA focuses no less than 122 world leaders. Furthermore, stories in the previous years have pointed that NSA’s focused specially on the German Chancellor Angela Merkel, Brazil’s President Dilma Rousseff, and Mexico’s previous President Felipe Calderon, the French Foreign Ministry, and additionally politicians at the 2010 G8 and G20 summits in Toronto.
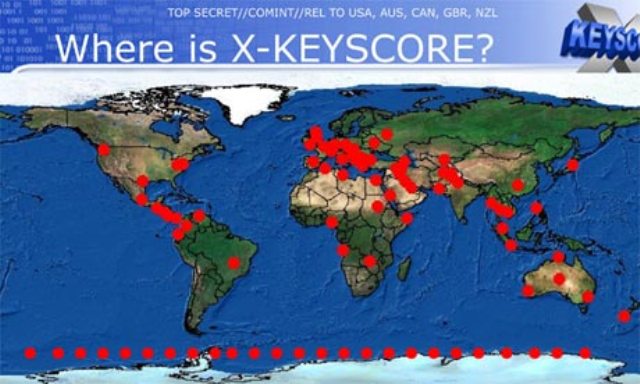
XKeyScore – Software that Sees it All
Image Source: The Guardian – One presentation claims the XKeyscore program covers’ nearly everything a typical user does on the internet
XKeyScore is a tool the NSA uses to inquiry “about everything a target does on the Internet” through information it blocks over the world. In uncovered documents, the NSA depicts it as the “widest reaching” framework to pursuit through Internet information.
NSA Special Hacking Team
The NSA has available to it a world class programmer group codenamed Tailored Access Operations or TAO that hacks into PCs around the world, taints them with malware and does “the works” when other reconnaissance strategies come up short.
Der Spiegel, which itemized TAO’s insider facts, named it as “a squad of handymen that can be brought in when ordinary access to an objective is blocked.” But they can most likely be best depicted as the NSA’s dark sack operations group.
TAO comes in focused on operations when the NSA cannot discover insight or they need more detailed intel on an objective through its mass observation programs. Before Snowden, the vast majority of their operations and systems were covered in mystery, but thank you Mr. Snowden.
NSA Wants Your Messages Too
This is NSA checks your messages everyday.#Snowden pic.twitter.com/k7MC0dRL6n
— Anon.Dos (@anondos_) May 14, 2015
It is not just about Internet information however. The NSA, tailing its unofficial motto of “WE WANT IT ALL!” captures more than two hundred million instant messages consistently worldwide through a system called Dishfire.
In leaked archives, the organization depicted the gathered messages as a “goldmine to exploit” for a wide range of personal information.
archives likewise uncovered that the NSA can “undoubtedly” split cell phone encryption, permitting the office to all the more effectively unravel and access the substance of captured calls and instant messages.
NSA Is Obsessed With Phone Calls In Bahamas and Afghanistan
The National Security Agency hacks and stores all telephone calls made in the Bahamas and Afghanistan through a system called MYSTIC.
The Bahamas was uncovered by The Intercept, Greenwald’s new site, while the second was uncovered by WikiLeaks, which protested The Intercept’s choice to withhold the second nation’s name. As a bonus they also snoops’ phone calls metadata in Kenya, Philippines & Mexico.
Source: The Guardian, Free Snowden, Spy Guide, The Global Intelligence Files, The Spy Files
You want to discuss a certain topic with likeminded people or you want to organize a local protest or you have an idea for a project that can help people in need in your local community or all around the world? Join our forum! www.anonboards.com
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ







this is not the NSA history, this is just shitting on their surveillance.