When the Seattle Police Department executed an early morning raid on the home of David Robinson, they already knew he had nothing to do with the child pornography that was transmitted through his IP address. Robinson is a privacy advocate who has been active in the Tor community. He has allowed for a Tor exit node to be run from his home, knowing the potential risks. The raid on his home, conducted by the Seattle PD – who knew the home was an exit point for the anonymous browser network – only goes to show that the war on privacy is in full swing.
Robinson told the press, “They were there because I run a Tor exit relay.”
The Tor network is a browser based privacy tool that bounces the user traffic through a number of nodes. These nodes are hosted by volunteers who believe in Internet anonymity. The final node the signal passes through before reaching its destination, is known as an exit relay. While all of the traffic is encrypted and does not leave any trace on the exit relay computer, the host of the relay runs the risk of being raided by police who either don’t understand Tor, or simply look to harass those who participate.
“Traffic passes through my computers and I don’t know what it is,” Robinson stated. “It’s much like the post office or the telephone company. Anybody can use it. Bad guys can also use it.”
The Seattle police were fully aware that Robinson hosted the relay. There is a publicly accessible list of Tor exit nodes. This list should assist law enforcement in determining the source of the transmission or at least eliminate potential suspects. The police arrived and demanded passwords to the computers. Robinson and his wife, Jan Bultmann, cooperated and provided their passwords. The police found nothing, seized none of their equipment and made no arrests. According to Robinson, he and his wife were “petrified” and believed the encounter equated to a violation of their privacy.
The department spokesman Sean Whitcomb told the pres that the department does in fact know how Tor works, but stated the raid was a necessary part of the investigation. “Knowing that, moving in, it doesn’t automatically preclude the idea that the people running Tor are not also involved in child porn. It does offer a plausible alibi, but it’s still something that we need to check out.” Basically, Whitcomb advised that even though they understand the technology and the purpose behind it, they will continue to raid the homes of Tor exit relay hosts “just to be sure.”
The explanation of being thorough is a poor attempt to cover the fact that law enforcement wants to punish people who exercise their rights of free expression. Tools like Tor have become essential for privacy in this war against free speech. The attitudes and statements of law enforcement all but guarantee that raids like this one, will continue with no end in sight.
Sources: Naked Security, NPR.
This article (Police Raid on Tor Exit Relay Host Confirms Continued War Against Privacy) is a free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.



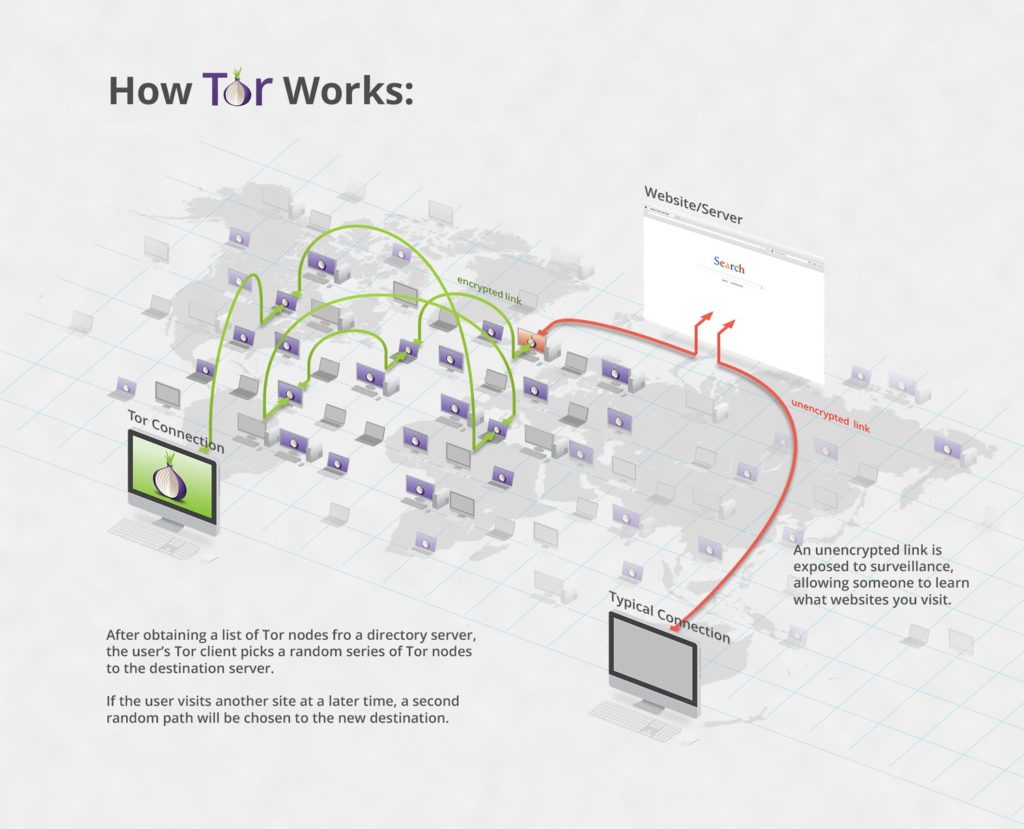



The police knew about David’s exit relay (aka a bridge) because it’s included in Tor’s public list. Each request made at https://bridges.torproject.org/ results in 3 bridge addresses being automatically sent. Police will naturally be gathering bridge addresses, as part of the war on privacy and dissent. A solution is for bridge hosts to create bridges that are excluded from the public list. Details at:
https://www.torproject.org/docs/bridges.html.en#RunningABridge