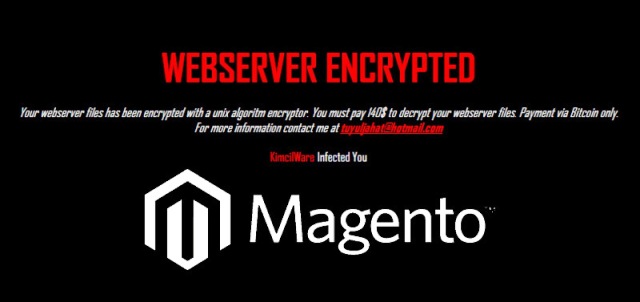
Ransomware known as KimcilWare is concentrating on online stores and e-commerce websites that host the Magento system, which is used by Rosetta Stone, Nichole Miller, Blu Dot, Nike, and many other famous online stores.

However, based on the analysis by the security experts, attackers exploit weaknesses in the e-commerce system and set up the KimcilWare on the web server. Once mounted, hackers use an algorithm to block ciphers, encrypt the online files present on the server and then ask for a payment in Bitcoins. These payments start from $100 and go above $400.
Magento is an online e-commerce store that is used by more than two hundred thousand businesses worldwide (that is what Magento’s website claims). The company offers a complete front-end and back-end solution to its customers. According to Magento, the hackers are targeting general web server vulnerabilities instead of Magento itself. However, according to many articles on the internet, the ransomware is targeting online stores that are running Magento.

However, that is not entirely true; there have been nine or more websites that have contained the ransomware. The earliest acknowledged hit was two months ago.

Almost a month ago, a Magento client published a report that said they had been hit by the ransomware. But to maintain its reputation, Magento argues that the KimcilWare has compromised only four online stores. A team of security experts stated that when they discovered the vulnerability, they were unsure whether this malware was hitting a particular version of the store.
The ransomware also infected a recent post from a customer that had installed a fresh version of Magento. He mentioned that it was related to the Vimeo video gallery extension on his website. Magento responded to the claim by stating that there is no information that suggests that a Magento extension is responsible for this problem. However, after the security specialists scanned the extension, nothing was found, meaning it was clean.
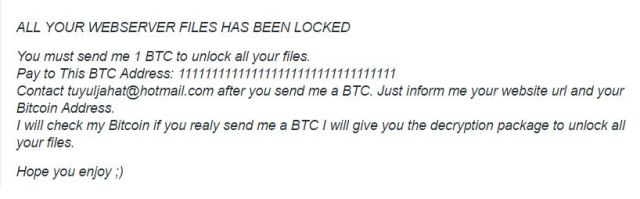
However, experts at Fortinet have found the crooks behind this ransomware, and have found a way to decrypt your Magento files, for further details visit Fortinet Blog.
You want to support Anonymous Independent & Investigative News? Please, follow us on Twitter: Follow @AnonymousNewsHQ
This Article (If You Have A Website That Is Running Magento Then You Need To Know About KimcilWare) is free and open source. You have permission to republish this article under a Creative Commons license with attribution to the author and AnonHQ.com.




